An Information Steganography Algorithm Based on Double Perturbation Scoring of Binary Image Based on STC Code
A binary image, dual technology, applied in the field of information hiding, to achieve the effect of small embedding disturbance, good imperceptibility, and high security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
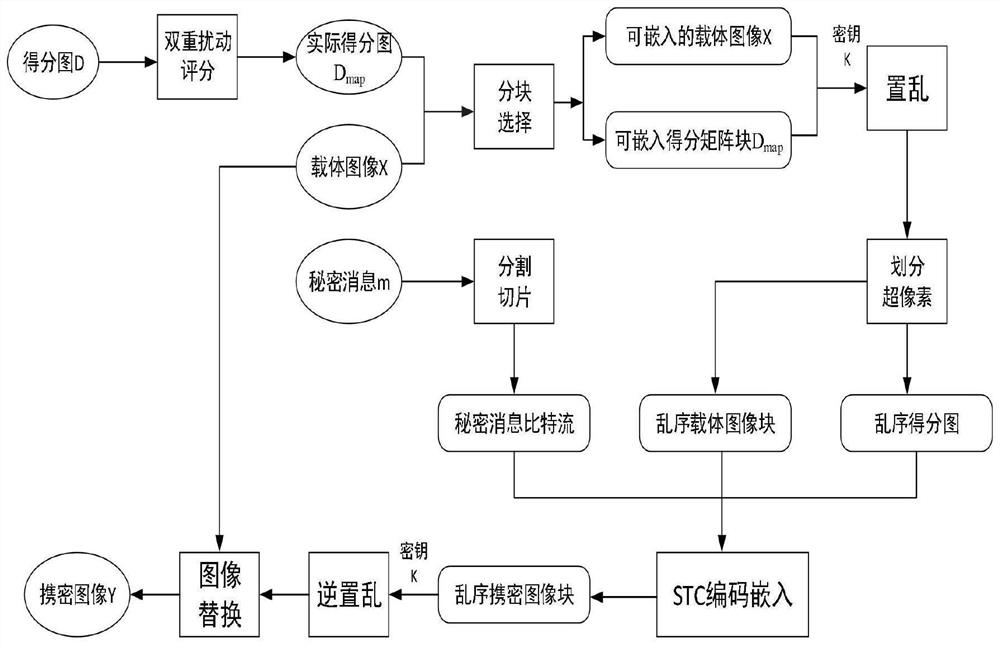
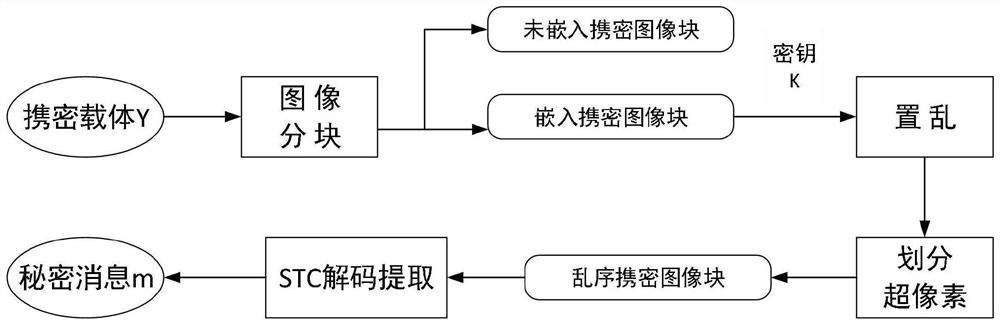
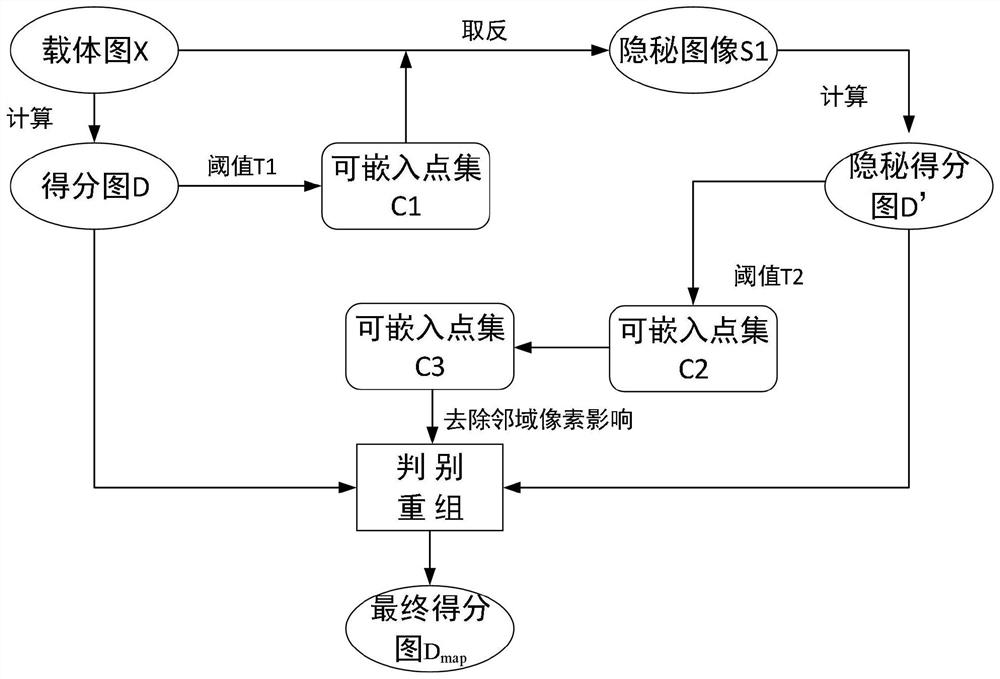
[0064] Such as figure 1 , figure 2 as well as image 3 As shown, the embedding process of an information steganography algorithm based on STC-coded binary image double perturbation scoring includes the following steps:
[0065] (1) Use the crmiLTP disturbance measurement method to calculate the disturbance score map D of the carrier image X, obtain the disturbance score score1(x,y) of each pixel, and filter the embeddable point set C 1 ;
[0066] (2) Flip the embeddable point set C sequentially 1 Pixels at the included positions, recalculate the image S 1 Disturb the map D' to get the perturbation score score2(x,y) of each pixel;
[0067] (3) Set the threshold T 2 , when both score1(x,y) and score2(x,y) are less than T 2 , from the steganographic image S 1 Filtering embeddable point sets in C 2 ;
[0068] (4) Remove point set C 2 Neighborhood pixels, filter out the embeddable point set C 3 ;
[0069] (5) Set the threshold T 3 , make the difference between score1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com