A user behavior fine classification method and system of a mobile application private encryption protocol
An encryption protocol, mobile application technology, applied in transmission systems, digital transmission systems, instruments, etc., can solve the problems of complex classifier effect tuning, high data set requirements, low universality, etc., to achieve fast training speed, reduce Feature dimension, the effect of good classification effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] In order to enable those skilled in the art to better understand the technical solutions in the embodiments of the present invention, and to make the purpose, features and advantages of the present invention more obvious and understandable, the technical core of the present invention will be further described in detail below in conjunction with the accompanying drawings . It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
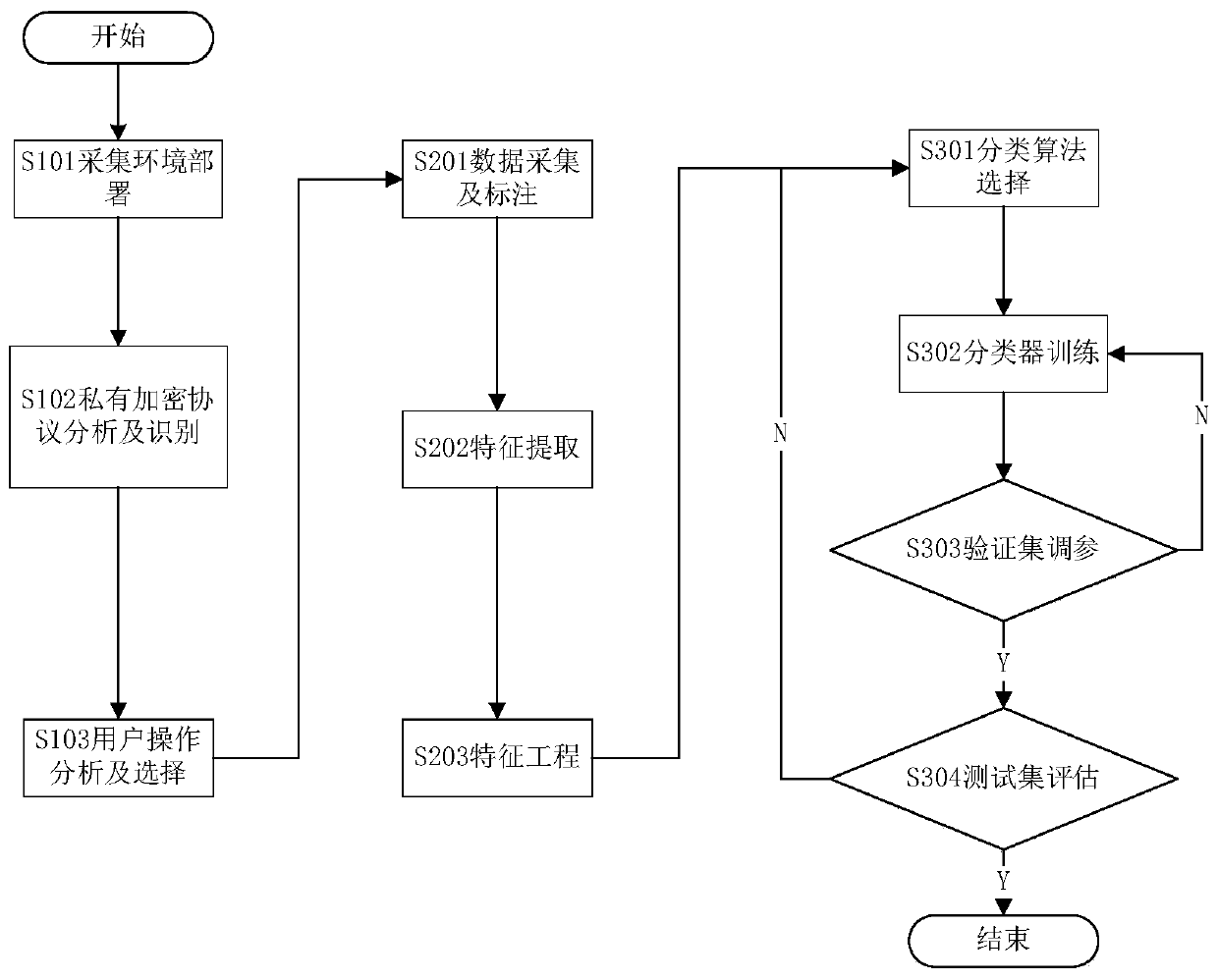
[0045] The scheme of the present invention comprises the following steps,
[0046] Step S101, user data collection environment deployment. Install each version of the application to different iOS and Android devices. Connect the device to the wireless hotspot, and use the traffic collection tool to capture the application traffic.
[0047] Step S102, identifying the private encryption protocol in the traffic. Set the characteristics of the privat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com