Physical Layer Security Transmission Method Based on Full-duplex Signal Cancellation
A technology of physical layer security and transmission method, which is applied in the field of secure communication, can solve problems such as injecting artificial noise, and achieve the effect of reducing signal-to-noise ratio and increasing bit error rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
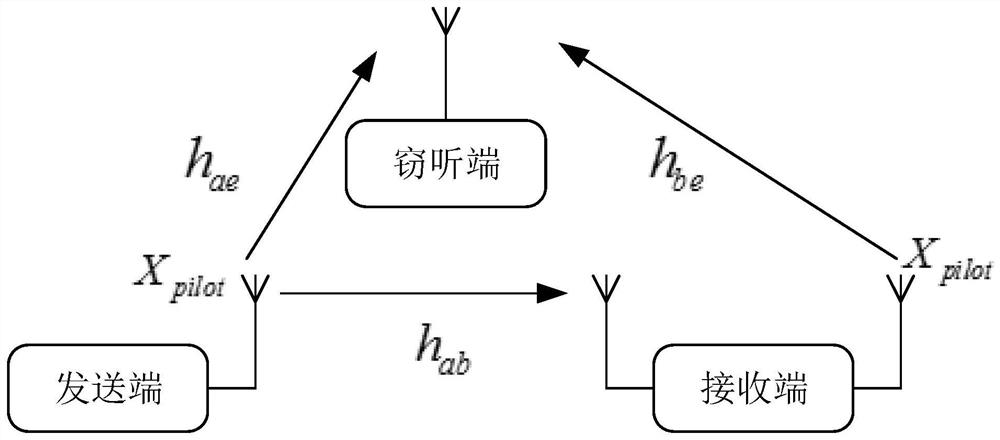
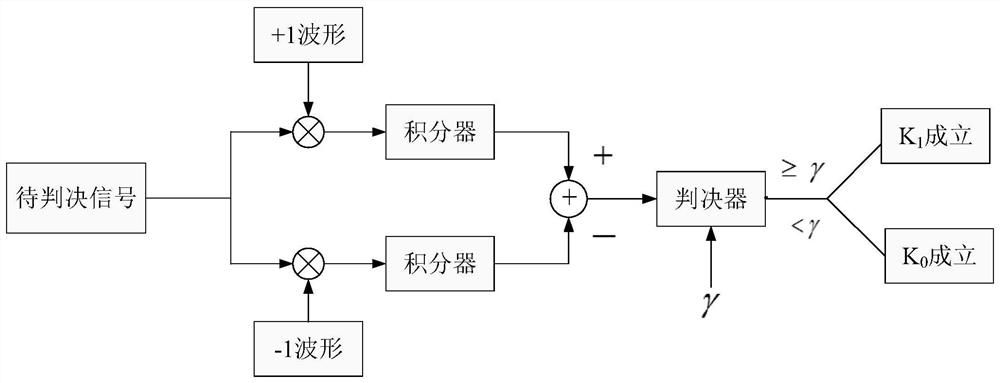
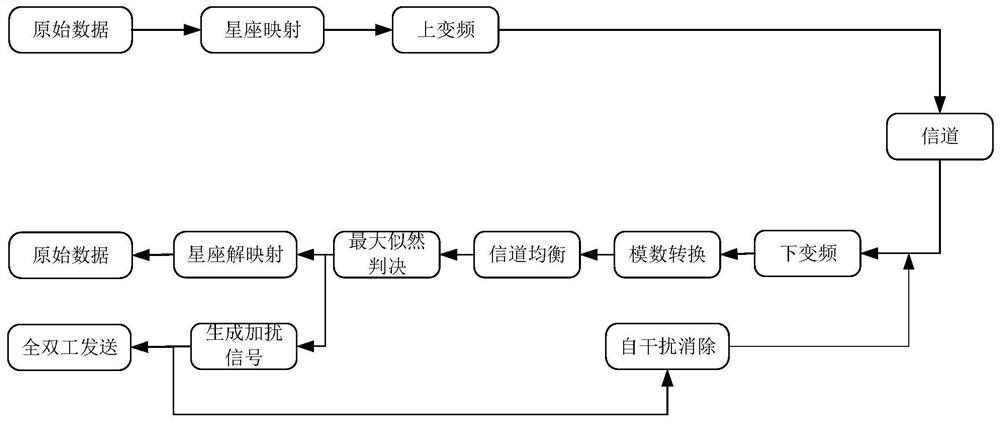
[0032] Specific implementation mode one: as figure 1 with image 3 As shown, the physical layer security transmission method based on full-duplex signal cancellation described in this embodiment includes the following steps:
[0033] Step 1. The receiving end uses full-duplex technology to send the same pilot signal X at the same frequency as the sending end at the same time pilot ;
[0034] Step 2. The receiving end uses the self-interference cancellation technology to remove the self-interference and obtain the pilot sequence received signal Y pilot ;
[0035] Step 3, receive the pilot sequence signal Y obtained in step 2 pilot with pilot signal X pilot The inverse multiplication of is used for channel estimation;
[0036] Step 4: The sending end generates a bit sequence of 0 and 1 to be sent, and the bit sequence is processed and transmitted to the channel;
[0037] Step 5, the receiving end receives the signal in the channel (transmitted to the channel in step 4), a...
specific Embodiment approach 2
[0070] Specific implementation mode two: the difference between this implementation mode and specific implementation mode one is: the specific process of said step two is:
[0071] Pilot signal X sent by the sender pilot After passing through the channel, the pilot sequence received by the receiving end receives the signal Y pilot Expressed as:
[0072] Y pilot = h ab x pilot +Z
[0073] Where: Z is additive Gaussian white noise, h ab is the channel coefficient between the sending and receiving ends.
specific Embodiment approach 3
[0074] Specific implementation mode three: the difference between this implementation mode and specific implementation mode one is: the specific process of the step three is:
[0075] Then use the least squares method for channel estimation, the pilot sequence received signal Y pilot with pilot signal X pilot Multiply the inverse of , and get the channel estimate The expression is:
[0076]
[0077] At the same time, the eavesdropping end also performs corresponding channel estimation, because the eavesdropping end receives the same pilot symbol X from the sending end and the receiving end at the same frequency. pilot ,Such as figure 1 As shown, the channel estimate at the eavesdropping end is where h ae is the channel coefficient between the sending end and the eavesdropping end, h be is the channel coefficient between the receiving end and the eavesdropping end.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com