Quality assessment method and device for multi-source threat intelligence
A quality assessment and intelligence technology, applied in the field of Internet security, can solve the problems of lack of intelligence richness assessment, inability to judge the quality of intelligence, and inability to judge the timeliness of intelligence products, and achieve the effect of standardization.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] In order to enable those skilled in the art to better understand the technical solutions of the present invention, the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
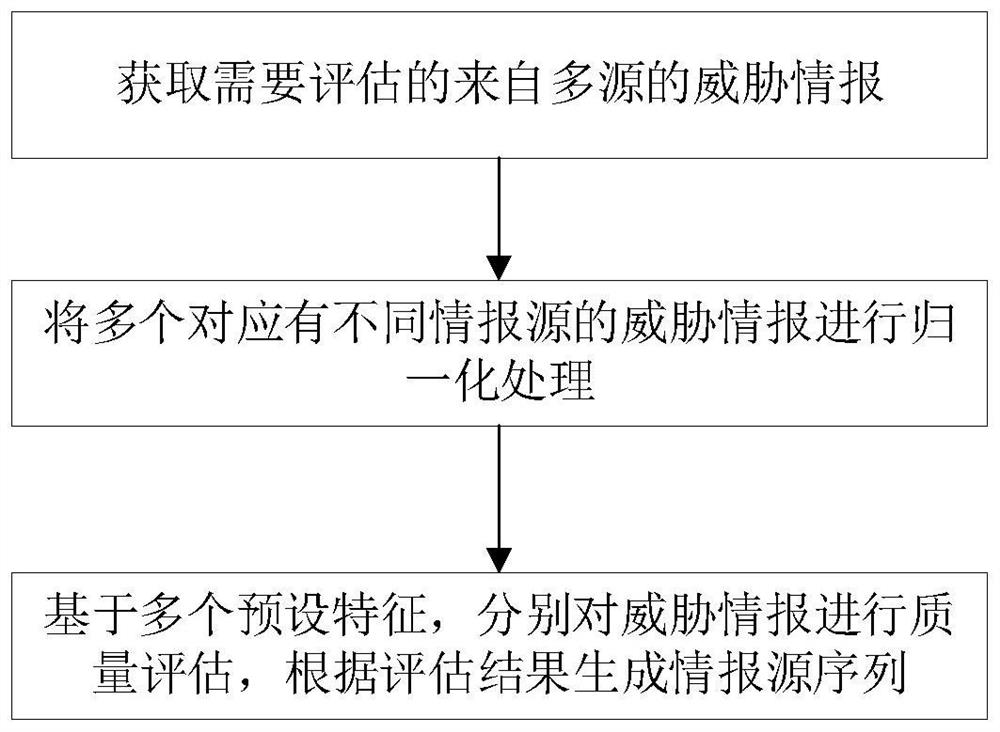
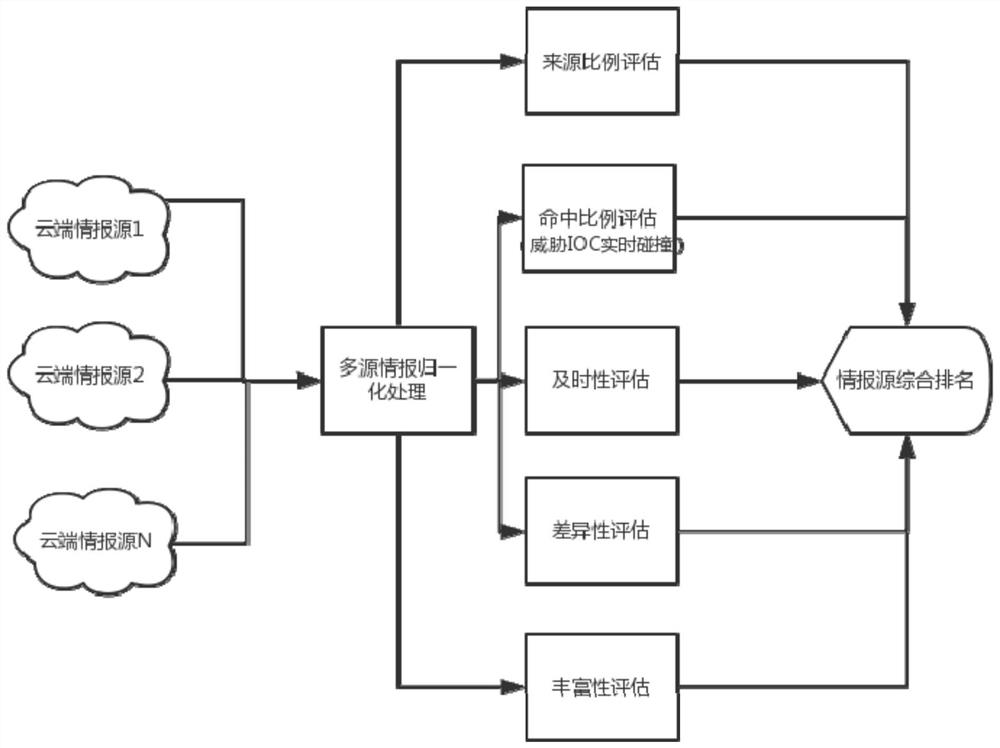
[0035] Threat intelligence data is a non-physical object in a special industry, and it is not convenient to evaluate data quality in actual production and application. This invention summarizes an effective multi-angle systematic evaluation method based on years of accumulation in the threat intelligence field. like figure 1 As shown, this embodiment carries out the following steps:
[0036] Obtain threat intelligence from multiple sources that needs to be assessed;
[0037] performing normalization processing on multiple threat intelligence corresponding to different intelligence sources;
[0038] Based on multiple preset characteristics, the quality of threat intelligence is evaluated separately, and the intelligence source s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com