Cash register and method for verifying security of cash register
A security verification and cash register technology, applied in security communication devices, user identity/authority verification, instruments, etc., can solve the problems of illegal tampering and switching of POS machine 1 business, and achieve the effect of improving security and increasing security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
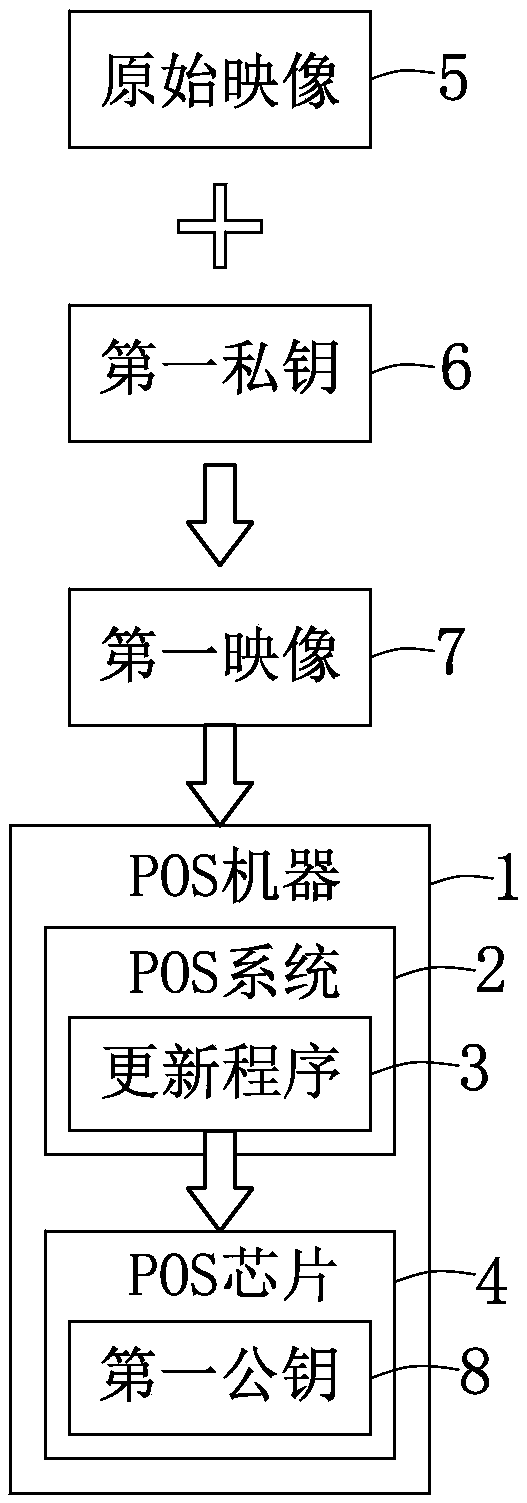
[0027] Please refer to image 3 , Which presents a block diagram of the security verification of a cash register (POS) according to an embodiment of the present invention. In this embodiment, the POS machine 11 includes: a communication component 110, a verification unit 119, a processing unit 120, and a storage component 130. The processing unit 120, the communication component 110, the verification unit 119, and the storage component 130 are all electrically connected to each other. In one embodiment, the processing unit 120 in the POS machine 11 is electrically connected to the communication component 110, the verification unit 119, and the storage component 130, respectively.
[0028] The processing unit 120 also contains a POS chip 14, which can adopt the PC-Base architecture, and its operating system adopts Windows interface, supports a variety of peripheral devices, touch screen, POS keyboard and standard keyboard operation, can be connected to IC chip card card reading M...
no. 3 example
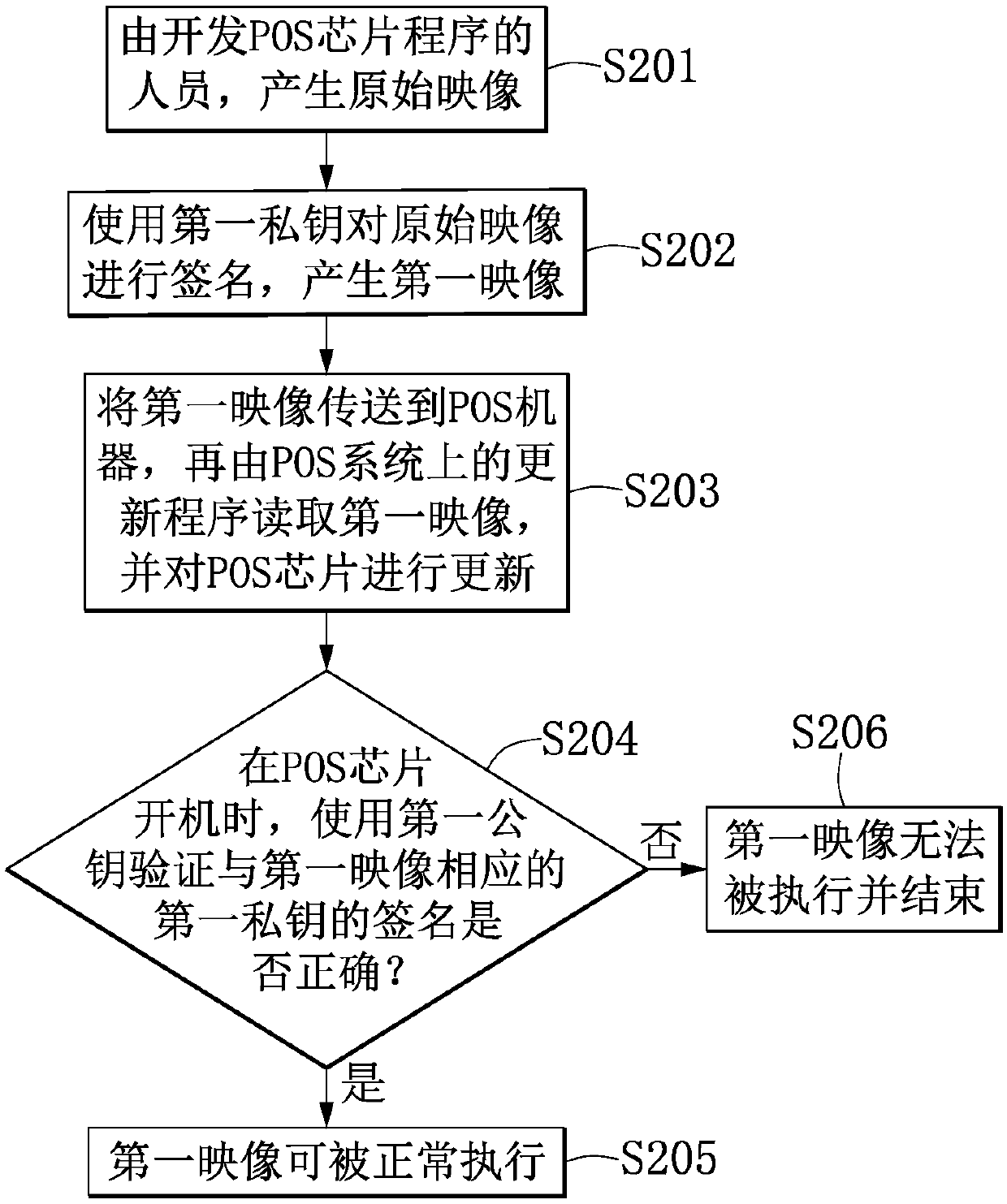
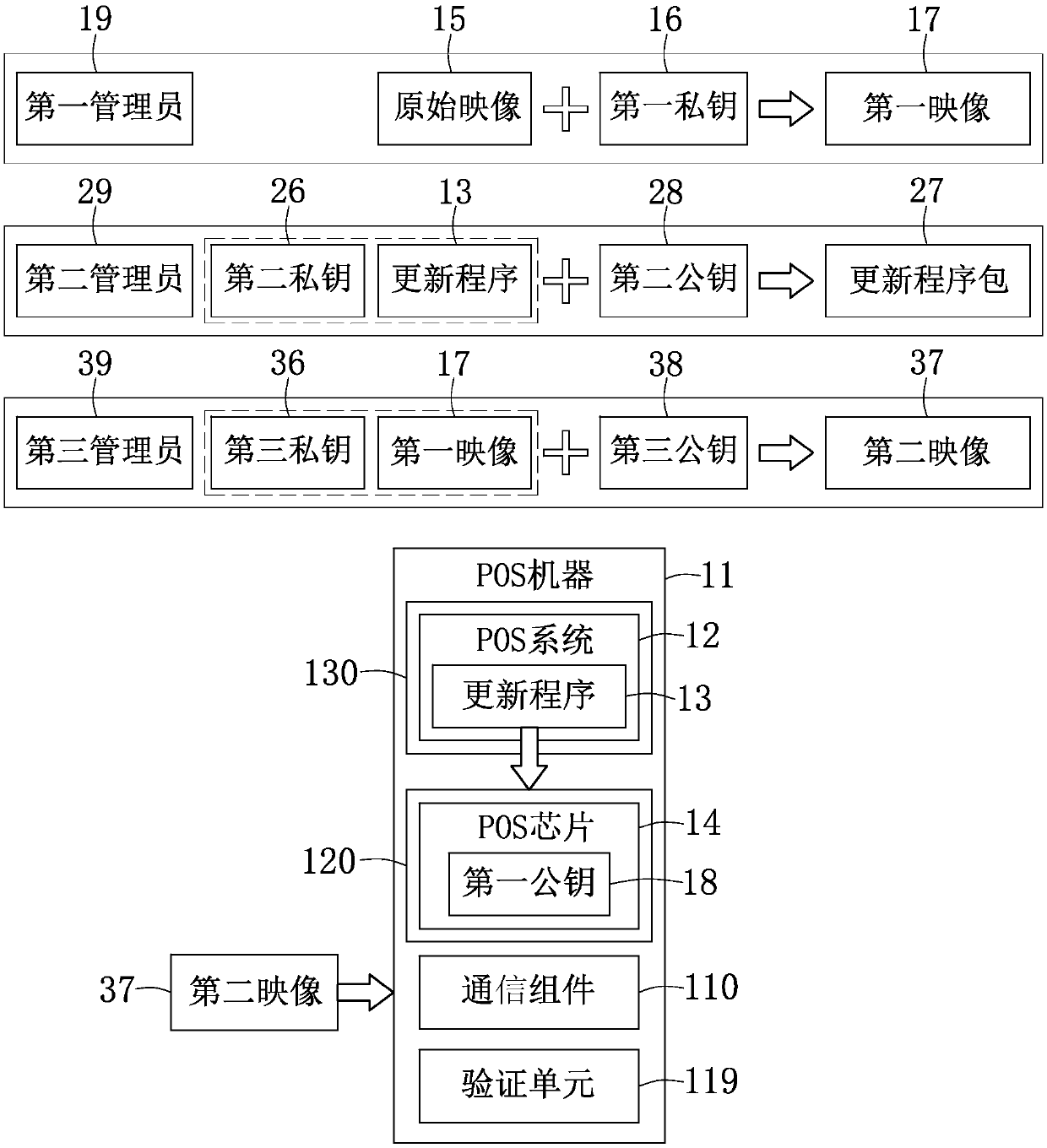
[0051] See also image 3 with Figure 5 . Figure 5 A flowchart of POS security verification according to an embodiment of the present invention is presented.
[0052] In step S501, the POS system 12 verifies the signature of the second private key 26 corresponding to the update package 27. A certain virtual terminal (or a second administrator) 29 delivers the update package 27 to a virtual terminal (such as a person) that executes the installation of the update package, and installs the update program for updating the image later on the POS system 12 13, and the update program 13 has not been installed in the POS system 12 in advance. At this time, the POS system 12 will verify the update program package 27 and whether it is signed with the second private key 26 matching the stored second public key 28.
[0053] If the verification is successful, the update program 13 is installed in step S502, and the second image 37 can be transmitted to the POS machine 11 through any virtual ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap