Training method, a detection method and a system for a malicious webpage detection model
A malicious webpage and detection model technology, applied in the direction of platform integrity maintenance, etc., can solve the problems of difficult rule update, high cost, and increased false detection rate, so as to improve prediction efficiency, reduce system resource consumption and time consumption, and artificial energy consumption. consumption, effects with generalization properties
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
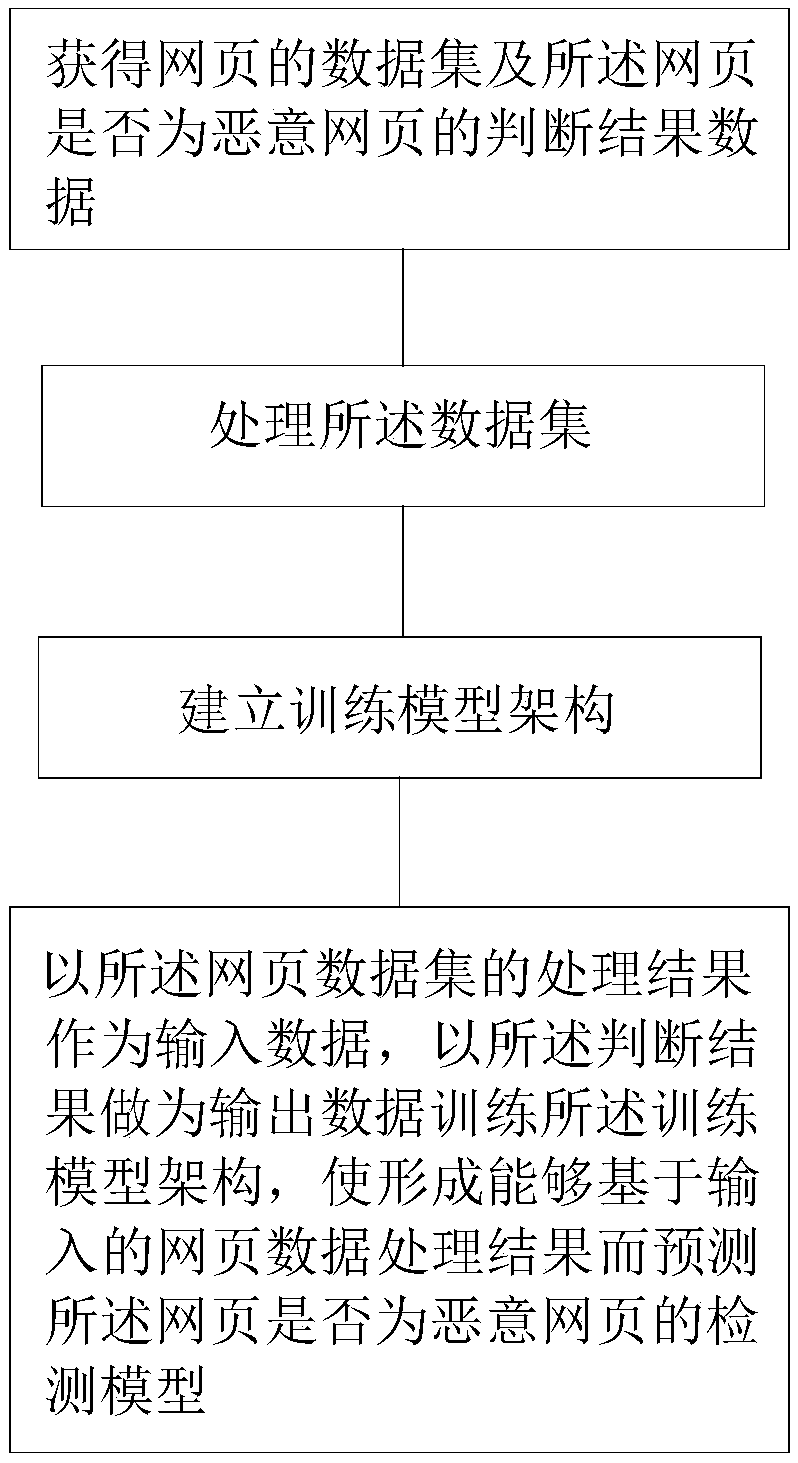
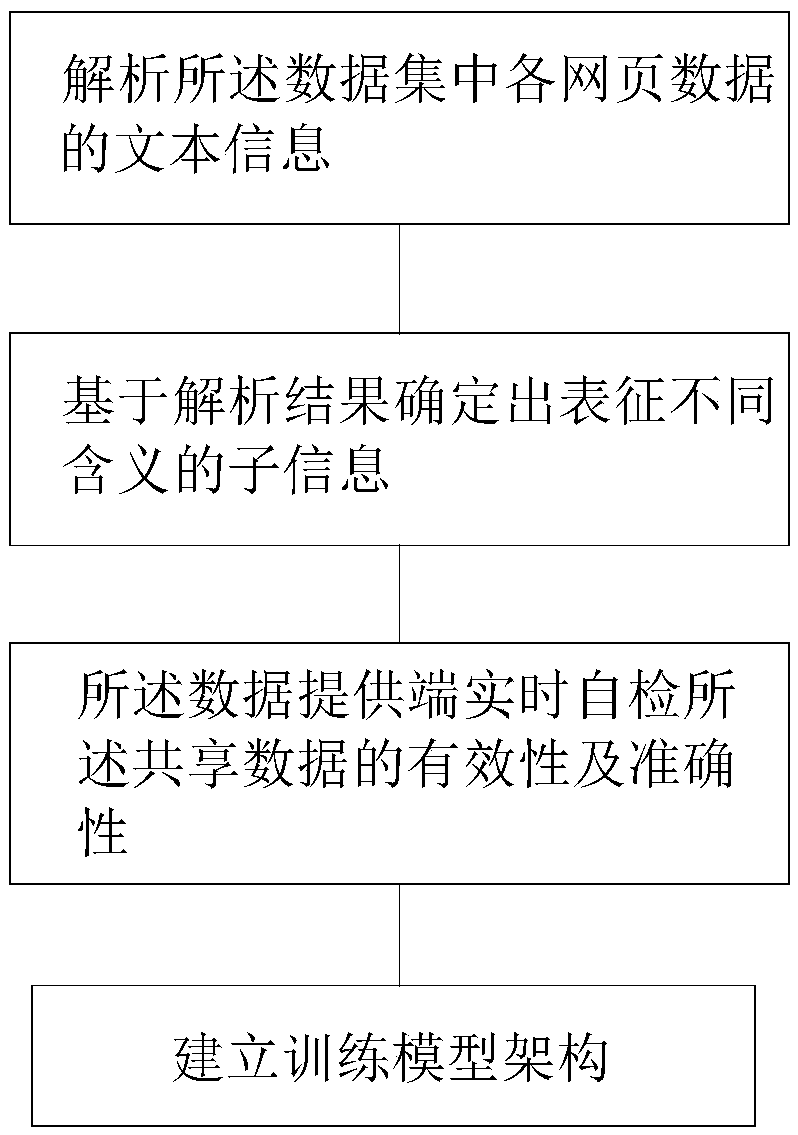
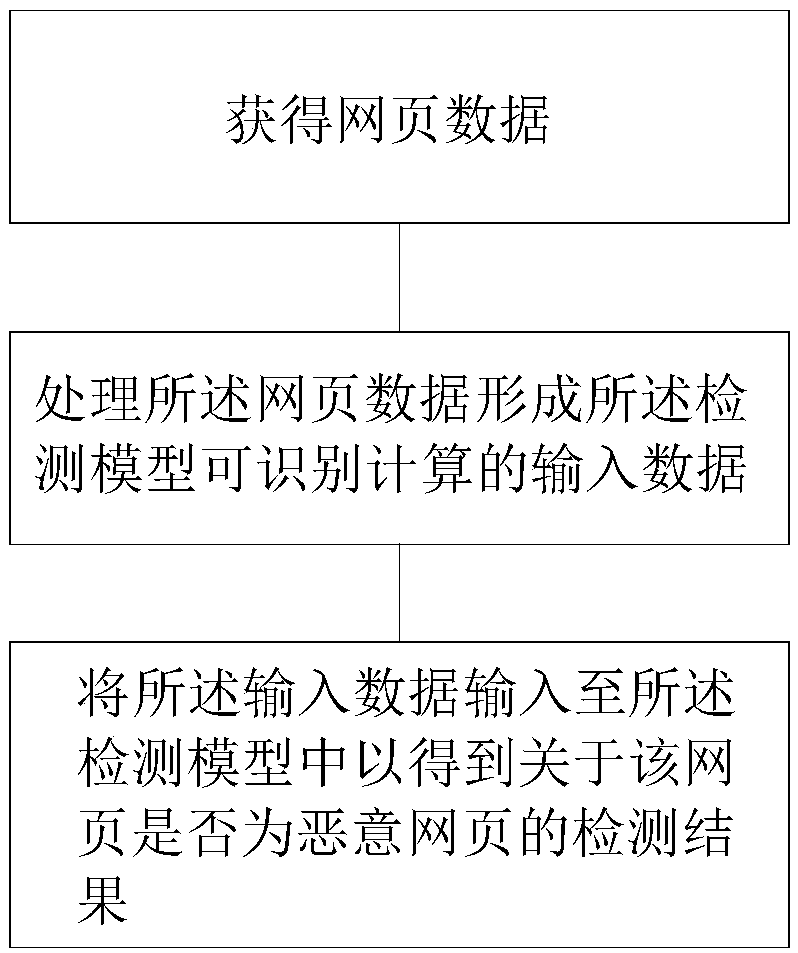
[0046] Below, specific embodiments of the present invention will be described in detail in conjunction with the accompanying drawings, but they are not intended to limit the present invention.
[0047] It should be understood that various modifications may be made to the embodiments disclosed herein. Accordingly, the following description should not be viewed as limiting, but only as exemplifications of embodiments. Those skilled in the art will envision other modifications within the scope and spirit of the disclosure.
[0048] The accompanying drawings, which are incorporated in and constitute a part of this specification, illustrate embodiments of the disclosure and, together with the general description of the disclosure given above and the detailed description of the embodiments given below, serve to explain the embodiments of the disclosure. principle.
[0049] These and other characteristics of the invention will become apparent from the following description of preferr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com