A Regulatory Anonymous Authentication Method Based on Zero-Knowledge Proof
A zero-knowledge proof and anonymous authentication technology, applied in the field of supervised anonymous authentication, can solve problems such as excessive exposure of user identity and attribute information, and achieve the effect of increasing mandatory supervision functions, ensuring anonymity, and protecting identity privacy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
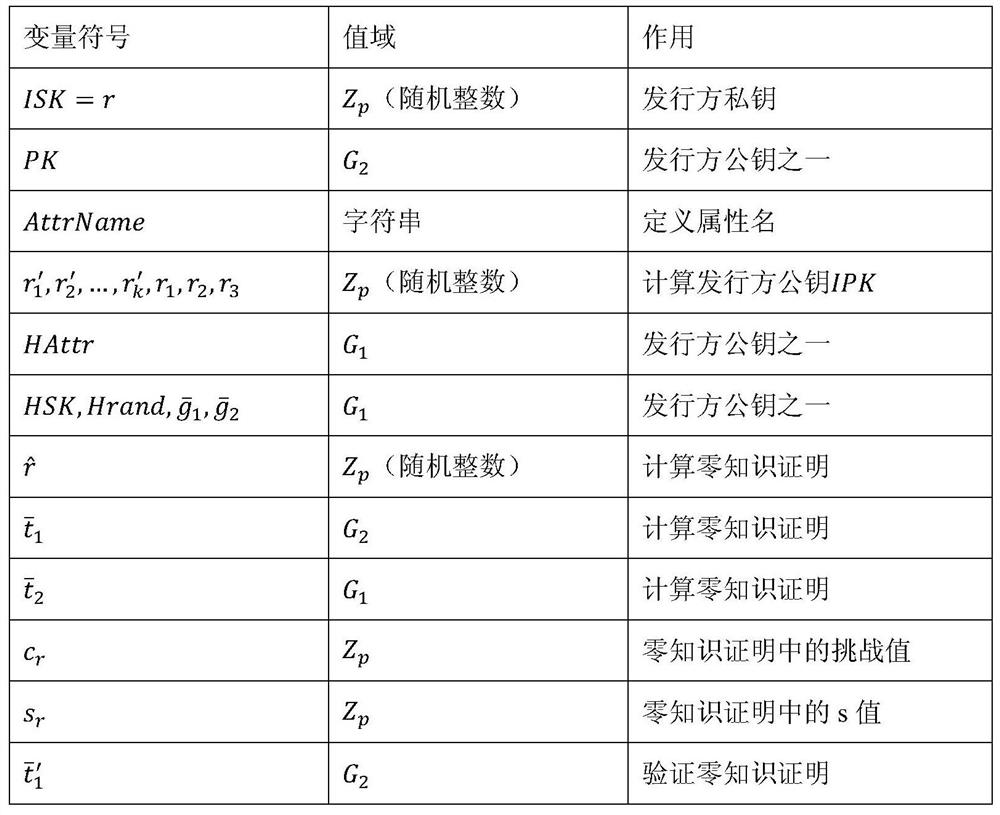
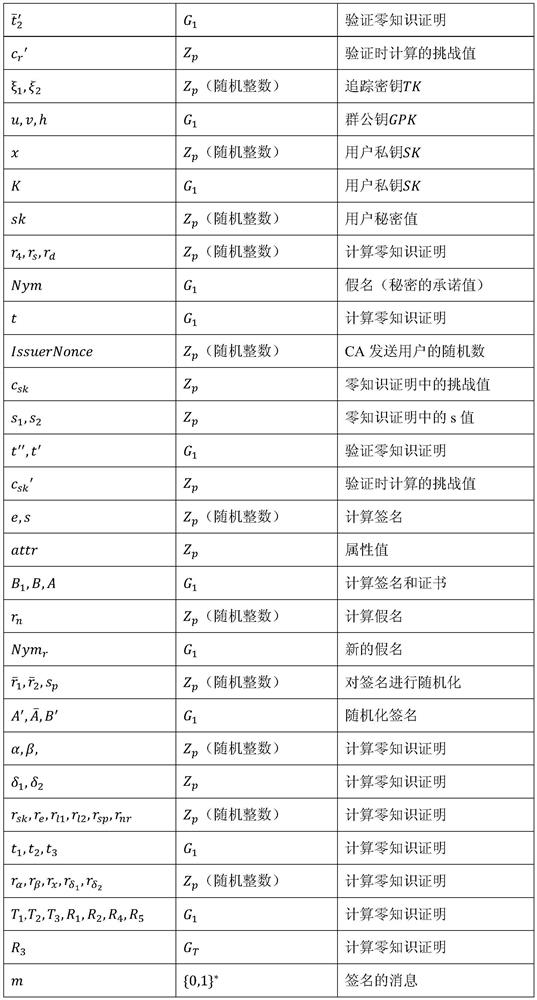
[0011] The present invention combines zero-knowledge proof, group signature scheme and other cryptography technologies to design an attribute-based supervised anonymous authentication method, which solves the problems of insufficient privacy protection and unsupervised user identity in the traditional authentication system.
[0012] 1. Program overview
[0013] The method includes three types of participants, CA (trusted center), user and verifier. After the system is established, the CA generates the issuing key pair, the tracking key and the group public key. Then the user registers, and the CA assigns a pair of private keys to it, and at the same time, the CA issues relevant certificates to the user according to the attribute information submitted by the user. When the user presents the certificate, the verifier can specify the attributes that need to be presented on the user certificate, and the user signs the certificate while hiding the attribute values that do not ne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com