Bluetooth device connection method based on network security and system thereof
A Bluetooth device and network security technology, applied in the field of network security, can solve problems such as hidden security risks, wasting time, reducing connection efficiency, etc., and achieve the effects of improving connection security, improving security, and saving time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
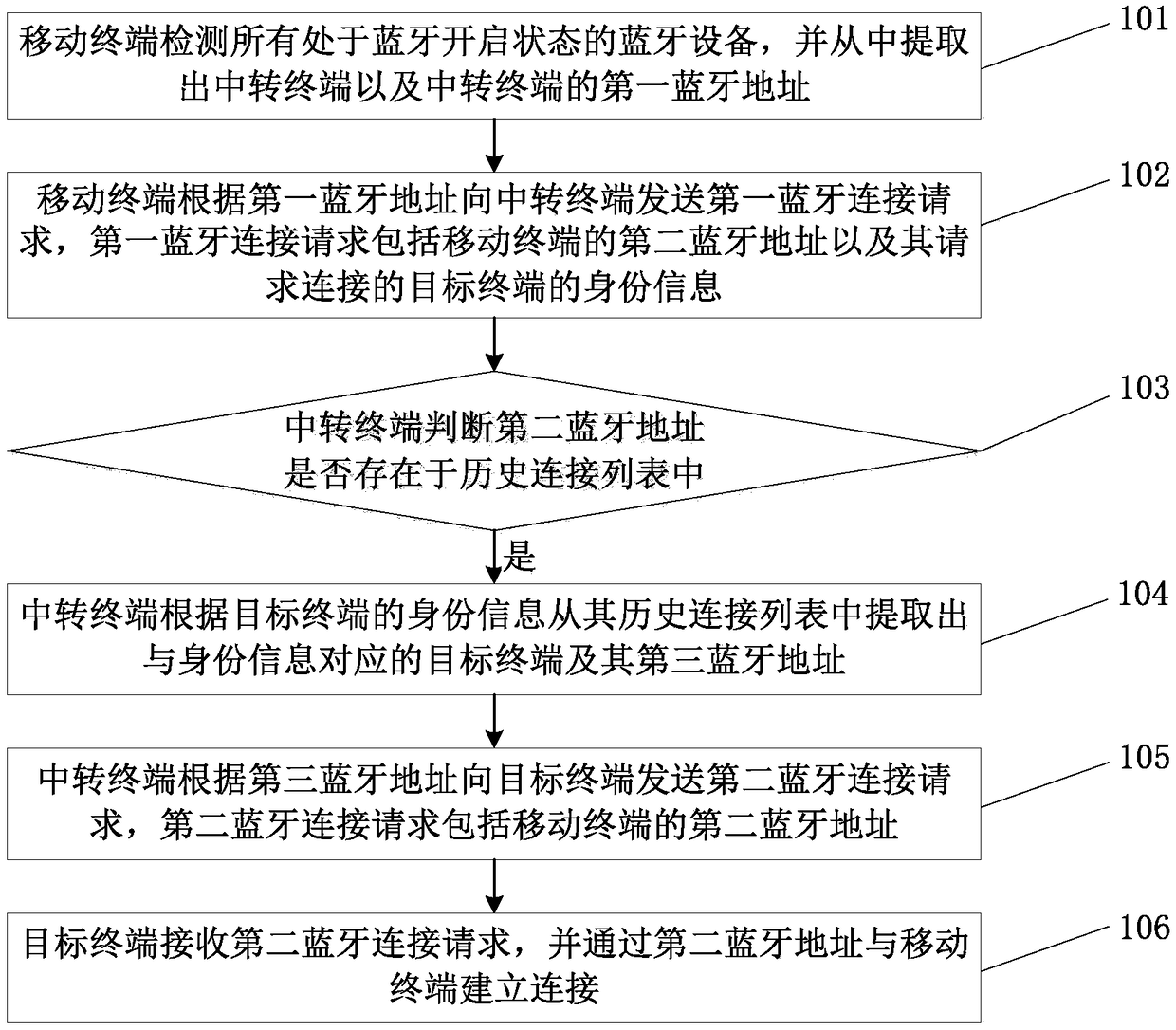
[0062] Such as figure 1 As shown, a Bluetooth device connection method based on network security, the mobile terminal establishes a Bluetooth connection with the target terminal through the transfer terminal, including the following steps:
[0063] 101: The mobile terminal detects all Bluetooth devices in the Bluetooth-on state, and extracts the transfer terminal and the first Bluetooth address of the transfer terminal;
[0064] 102: The mobile terminal sends a first Bluetooth connection request to the transfer terminal according to the first Bluetooth address, where the first Bluetooth connection request includes the second Bluetooth address of the mobile terminal and the identity information of the target terminal for which it requests connection;
[0065] 103: The transfer terminal extracts the historical connection list, and judges whether the second Bluetooth address exists in the historical connection list;
[0066] 104: If yes, the transfer terminal extracts the target t...
Embodiment 2
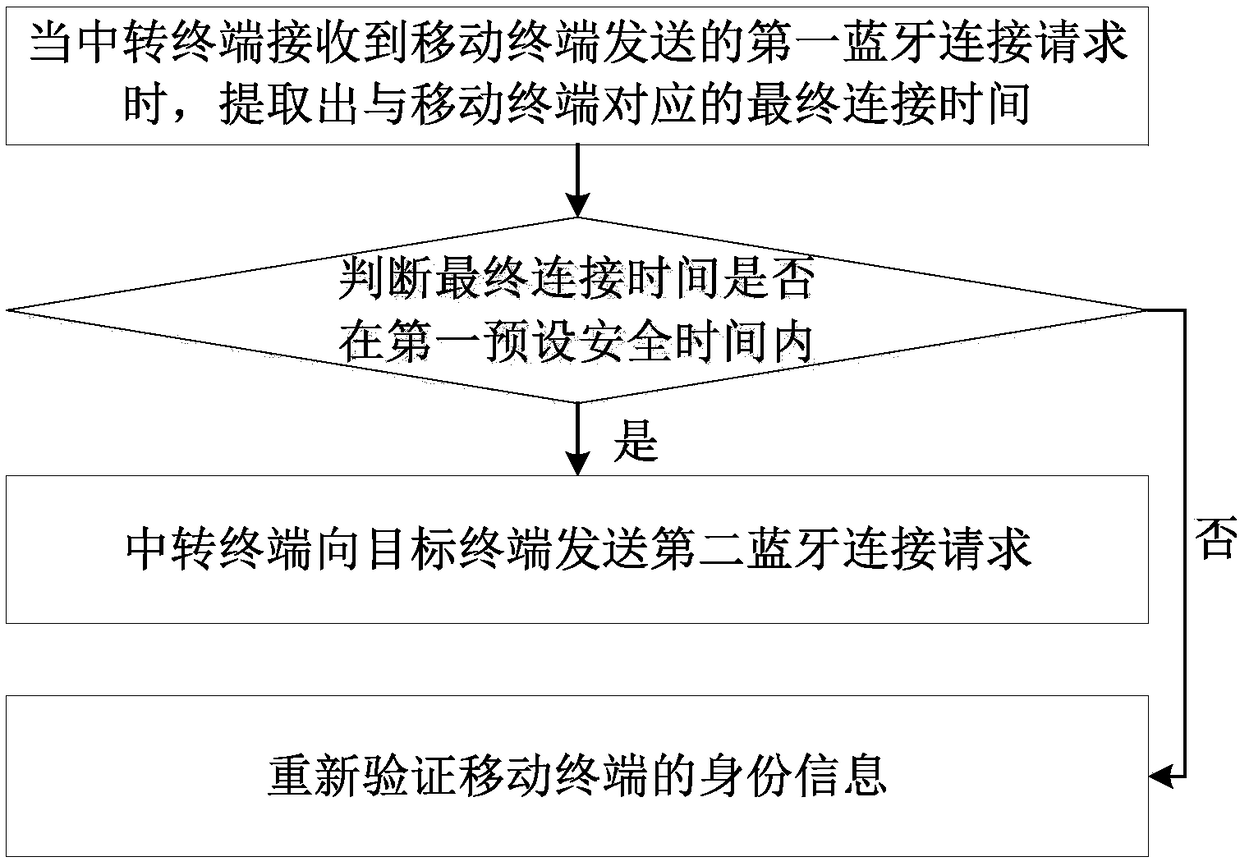
[0071] Such as figure 2 As shown, the transfer terminal is provided with a first preset security list, and the first preset security list includes the final connection time of each Bluetooth device connected to the transfer terminal;
[0072] When the relay terminal receives the first Bluetooth connection request sent by the mobile terminal, it extracts the final connection time corresponding to the mobile terminal;
[0073] judging whether the final connection time is within the first preset safety time;
[0074] If so, then send a second bluetooth connection request to the target terminal;
[0075] If not, re-verify the identity information of the mobile terminal.
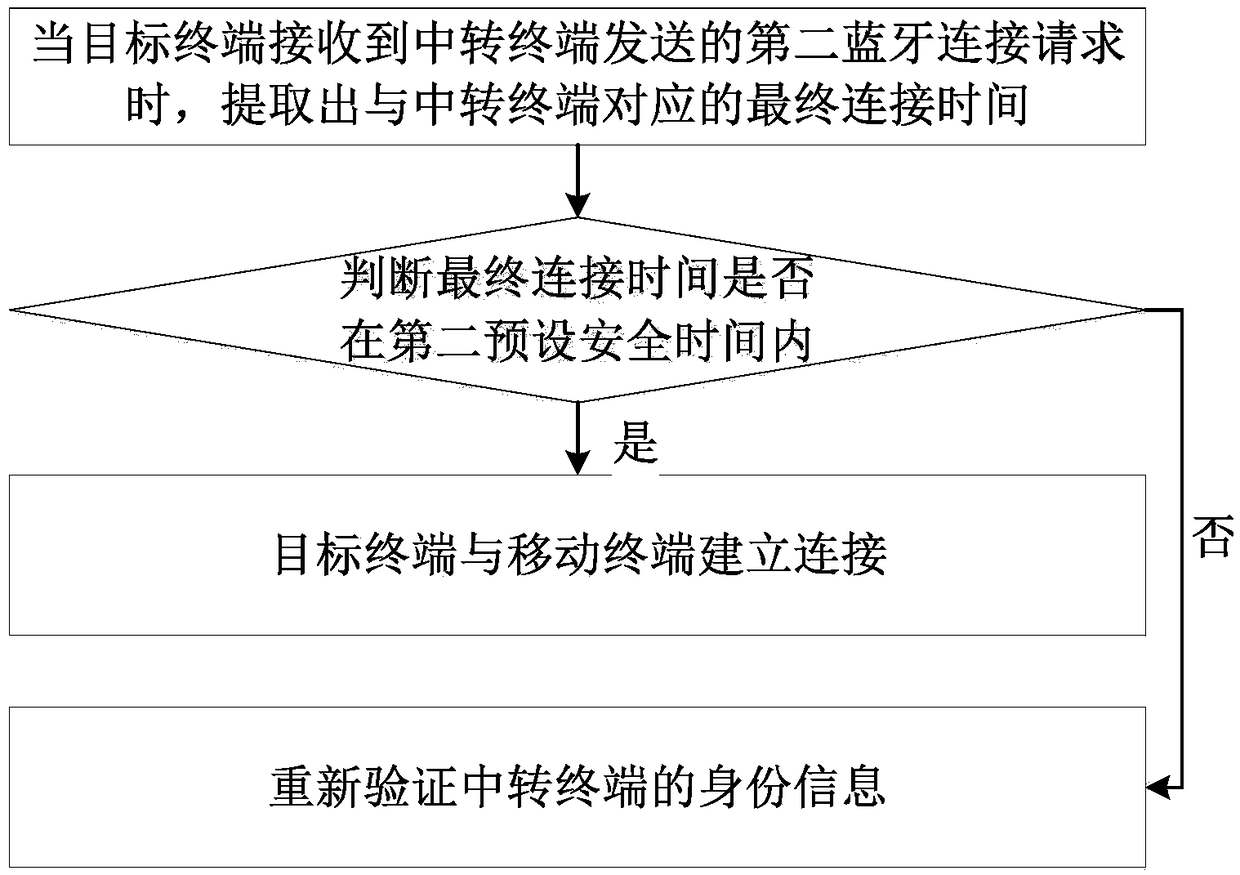
[0076] Such as image 3 As shown, the target terminal is provided with a second preset security list, and the second preset security list includes the final connection time of each Bluetooth device connected to the target terminal;
[0077] When the target terminal receives the second Bluetooth connection re...
Embodiment 3
[0085] Such as Figure 4 As shown, after step 106, it also includes:
[0086] The target terminal adds the second Bluetooth address of the mobile terminal to the storage device.
[0087] Such as Figure 5 As shown in , the target terminal records the access times of the mobile terminal;
[0088] Judging whether the number of access times is greater than or equal to the preset number of times;
[0089] If so, the target terminal adds the second Bluetooth address of the mobile terminal to the storage device.
[0090] Specifically, the mobile terminal establishes a connection with the target terminal for the first time through the transfer terminal. When the mobile terminal does not cause security problems after multiple connections with the target terminal, the mobile terminal can directly connect to the target terminal without passing through the transfer terminal. At the same time, The mobile terminal is equivalent to another transit terminal.
[0091] After the mobile te...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com