An implementation method of certificateless public key cryptosystem based on elliptic curve
A public-key cryptosystem and elliptic curve technology, applied in the field of information security, can solve the problems of low operating efficiency, low computing efficiency, and incompatibility with standard cryptographic algorithms, achieve small storage burden, fast computing efficiency, and avoid certificate management and use problem effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
[0073] (2) Embodiment two;
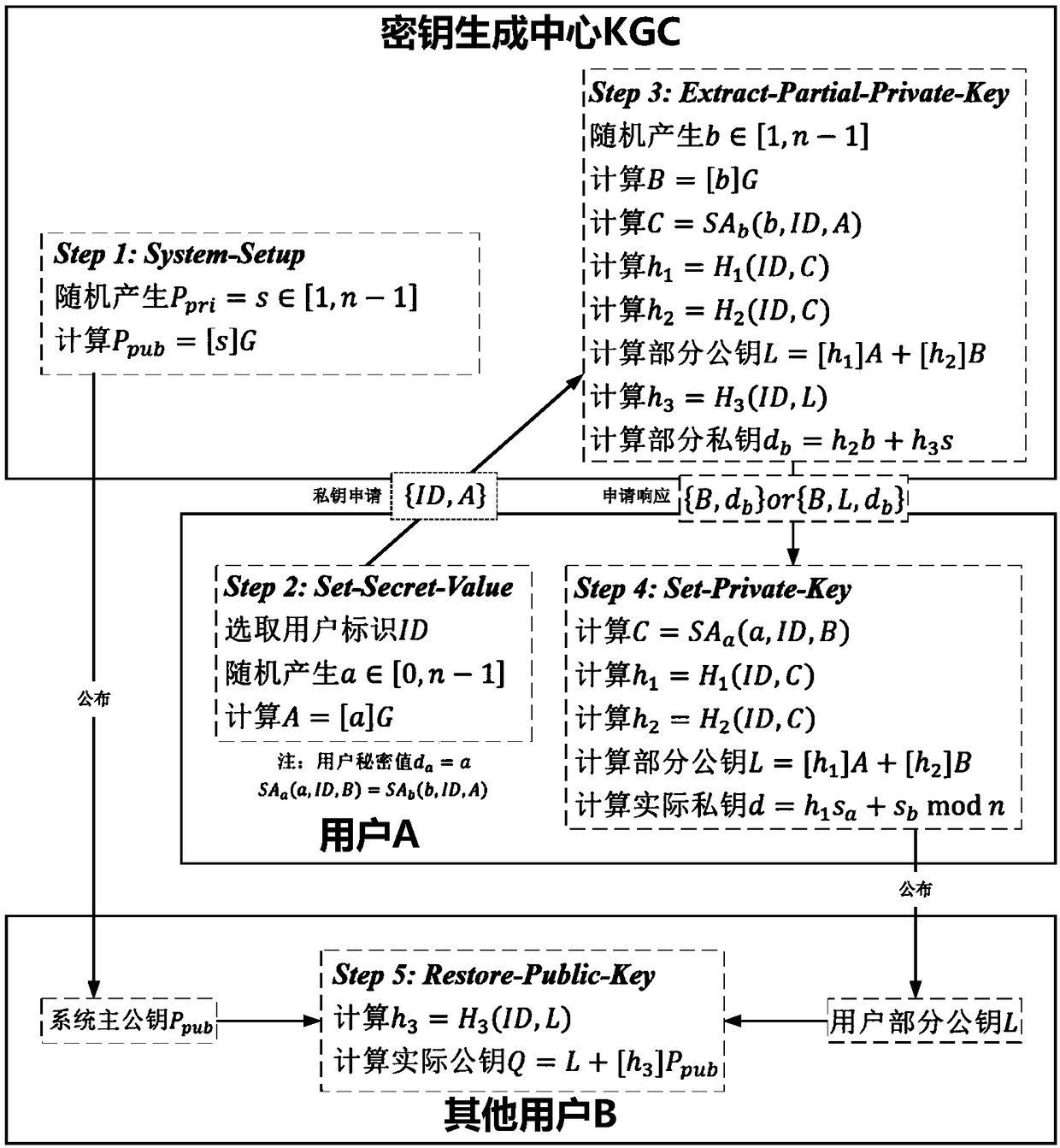
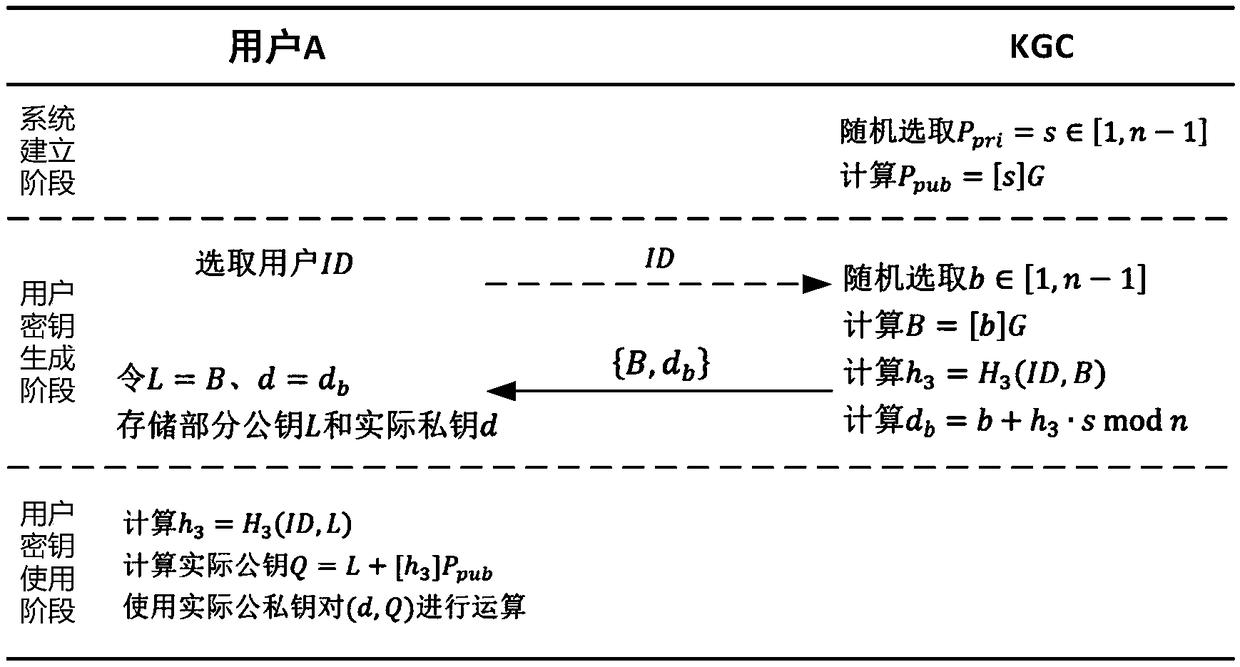
[0074] please see image 3 , the implementation principle of Embodiment 1 of the present invention is divided into three stages: system establishment stage, user key generation stage and user key use stage.
[0075] In the system establishment phase of this embodiment, the system establishment is completed by the key generation center KGC. Elliptic curve parameters and secure hash function are selected in the same way as in the first embodiment. The specific logical operation mode of the cryptographic function is:
[0076] 1) The secret negotiation function is selected as SA a (a,ID,B)=[a]G||B and SA b (b, ID, A)=A||[b]G, that is, data concatenation;
[0077] 2) The security mapping function is selected as H 1 (ID, C) = Hash(0x01||ID||C), H 2 (ID, C) = Hash(0x02||ID11C) and H 3 (ID, L)=Hash(0x03||ID||L), where Hash(·) is a hash algorithm.
[0078] Finally, KGC randomly generates the system master private key and calculates the system maste...
Embodiment 3
[0087] (3) Embodiment three;
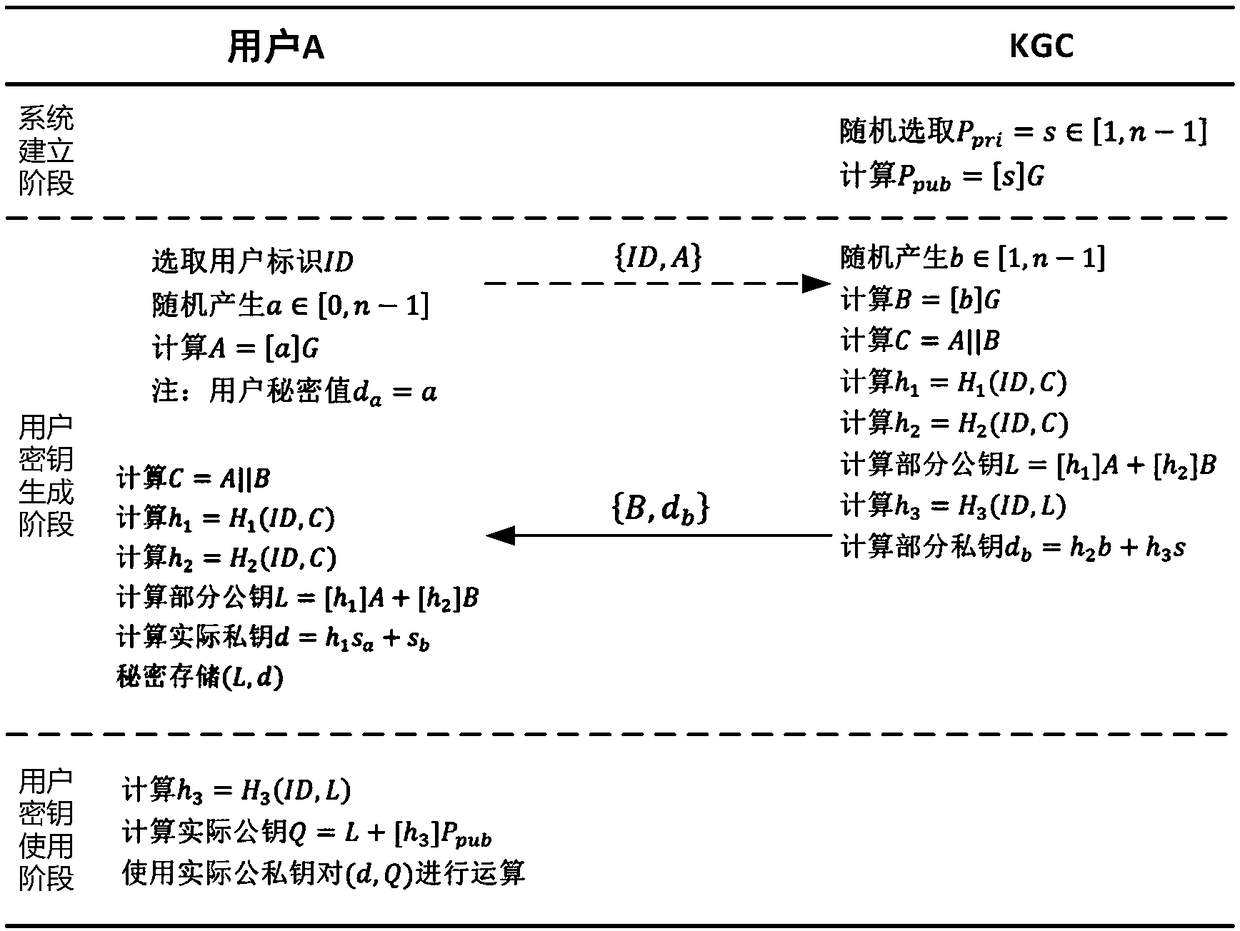
[0088] please see Figure 4 , the implementation principle of Embodiment 1 of the present invention is divided into three stages: system establishment stage, user key generation stage and user key use stage.
[0089] In the system establishment phase of this embodiment, the system establishment is completed by the key generation center KGC. Elliptic curve parameters and secure hash function are selected in the same way as in the first embodiment. The specific logical operation mode of the cryptographic function is:
[0090] 1) The secret negotiation function is selected as SA a (a, ID, B) = [a] B and SA b (b, ID, A)=[b]A, that is, the ECDH key agreement based on the elliptic curve point product operation;
[0091] 2) The security mapping function is selected as H 1 (ID, C) = Hash(0x01||ID||C), H 2 (ID, C) = 1 and H 3 (ID, L)=Hash(0x03||ID||L), where Hash(·) is a hash algorithm.
[0092] Finally, KGC randomly generates the system master p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com