Conflict detection method for URL rules
A conflict detection and rule technology, applied in electrical components, transmission systems, etc., can solve problems such as the inability to apply WEB security gateways, lower detection accuracy, repeated node application, etc., achieve high rule conflict detection performance, reduce the number of comparisons, reduce The effect of repeated applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
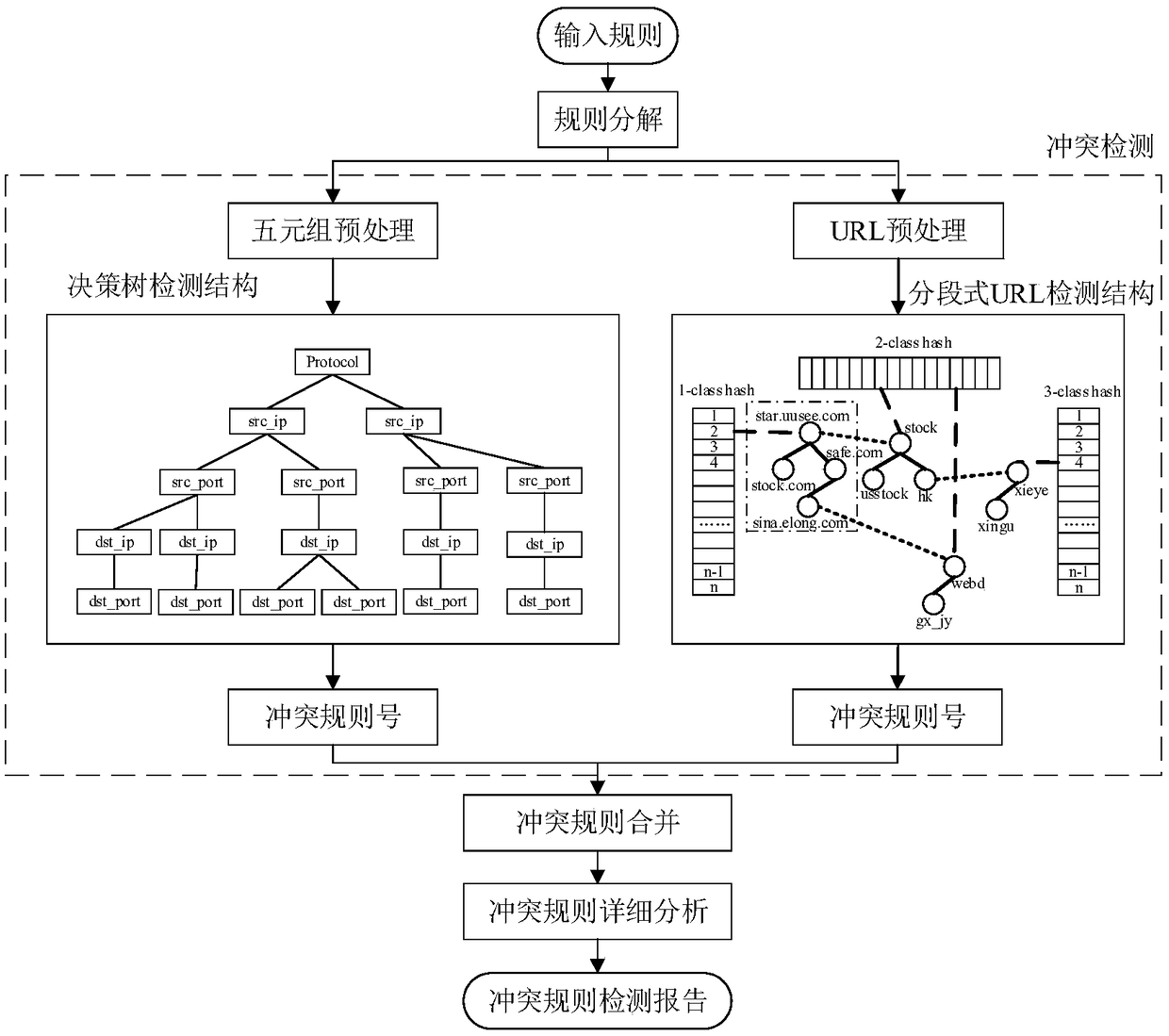
[0019] The following examples describe the present invention in more detail.
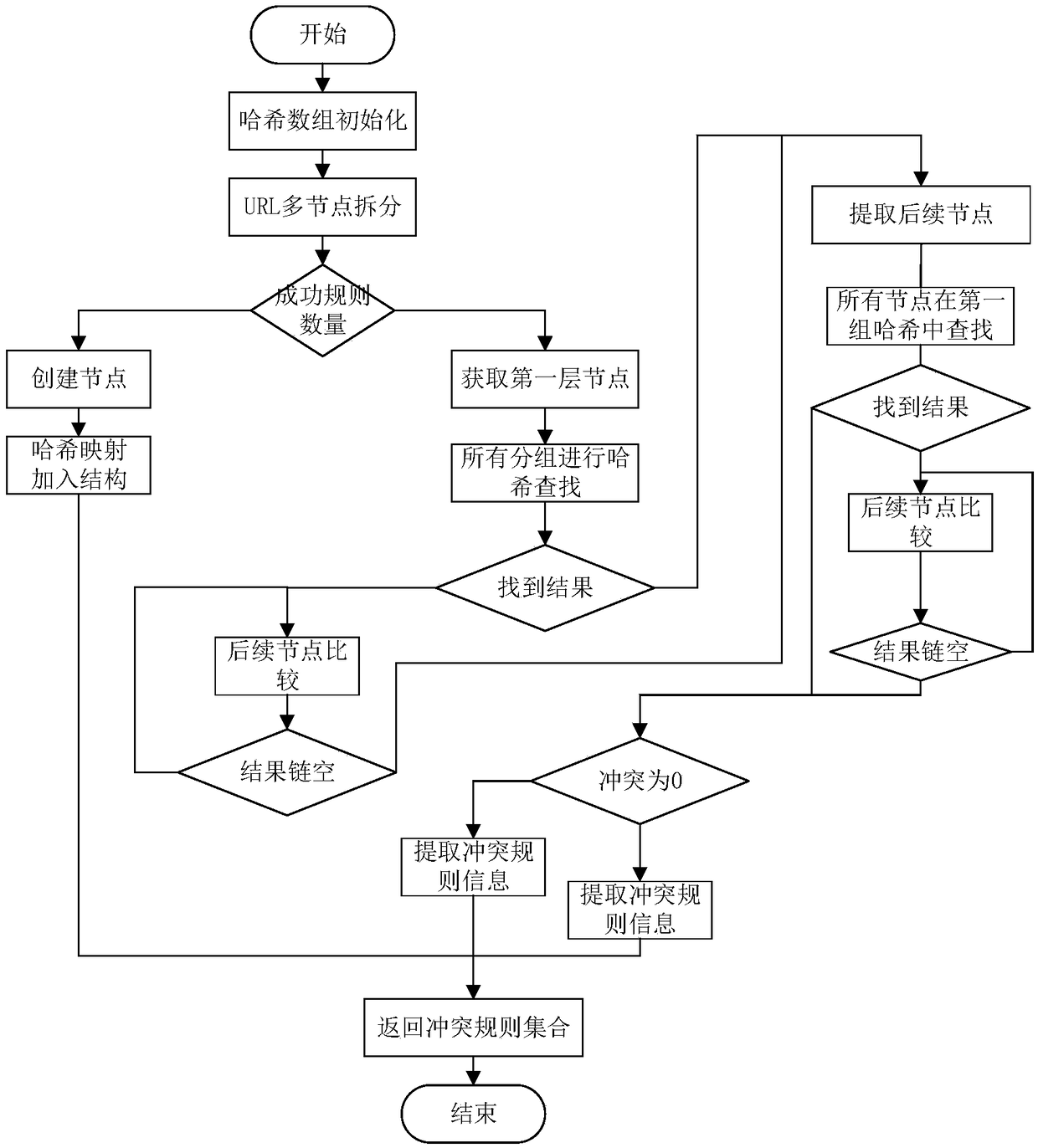
[0020] 1) Initialize the index arrays corresponding to k groups of hash functions, create k groups, 1~k correspond to each part of the URL nodes, and set all elements of each array to NULL. The k value is the number of layers with the largest number of layers in the URL rule item, and each group of hash functions corresponds to the layer path in the URL.
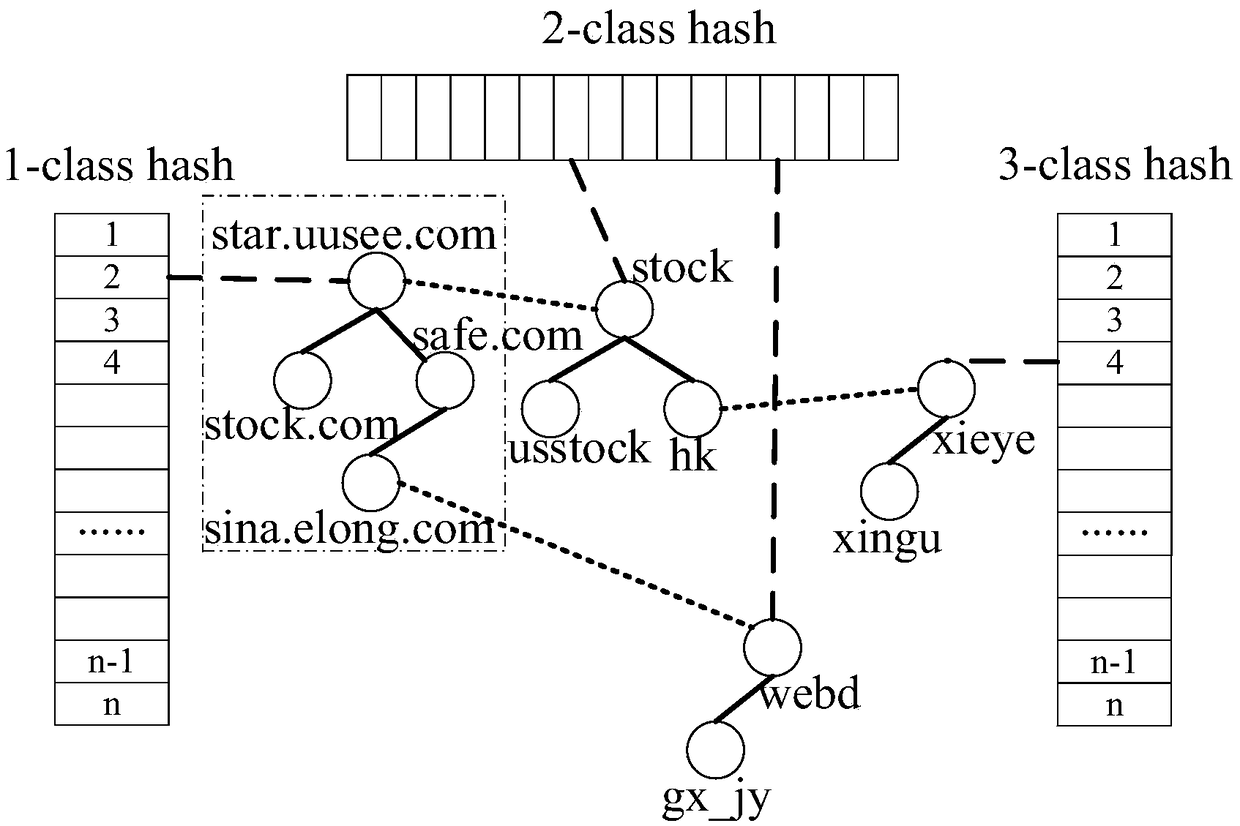
[0021] 2) If the set of rules to be detected is empty, it means that the detection is over. Otherwise, the URL rule item is split into multiple nodes, and the split unit is " / ". The example is as follows: www.sogou.com / labs / research / list_tsinghua. PHP is the most common form of URL, which can be split into four nodes: www.sogou.com, labs, research and list_tsinghua.php.
[0022] 3) If it is the first rule, a node is created for each path of the URL item, and the nodes are connected with each other using successor pointers, and the successor of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com