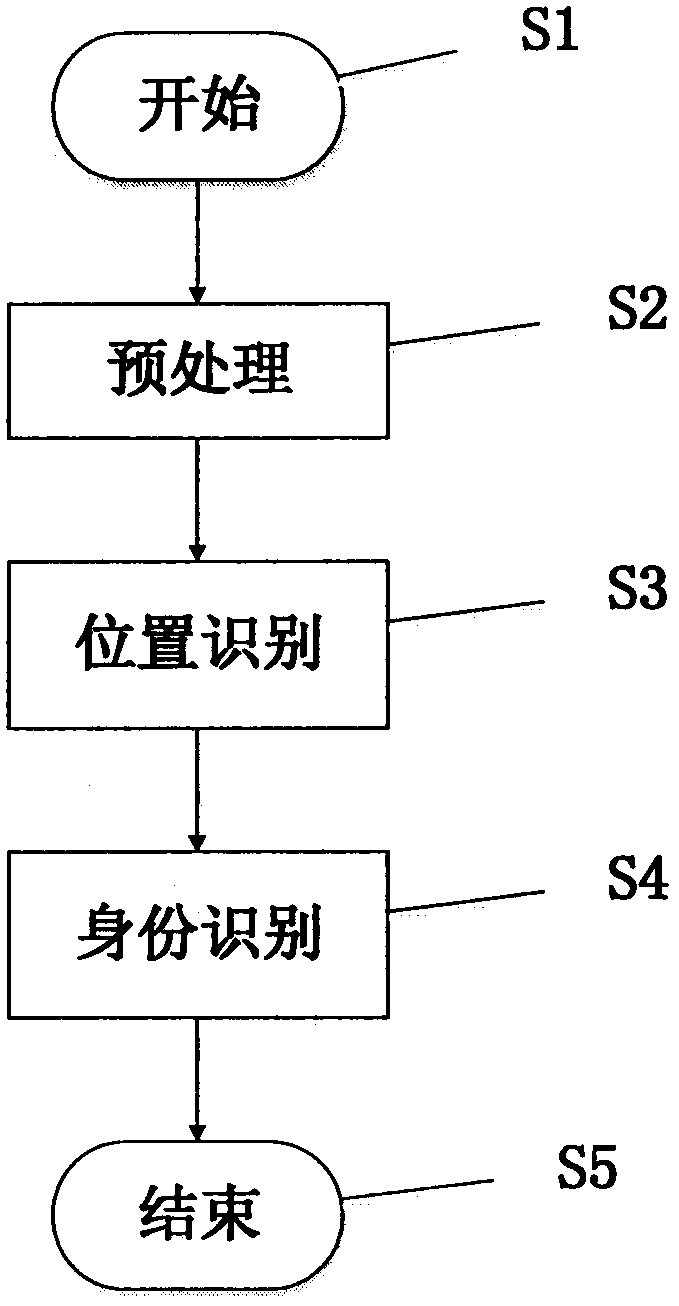
User identity recognition method based on carrying position and carrying mode of smart mobile phone
A technology of user identification and carrying location, which is applied in character and pattern recognition, computer security devices, devices with sensors, etc. problem, to achieve a safe and reliable authentication method, to ensure authenticity, and to achieve the effect of a wide range of applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
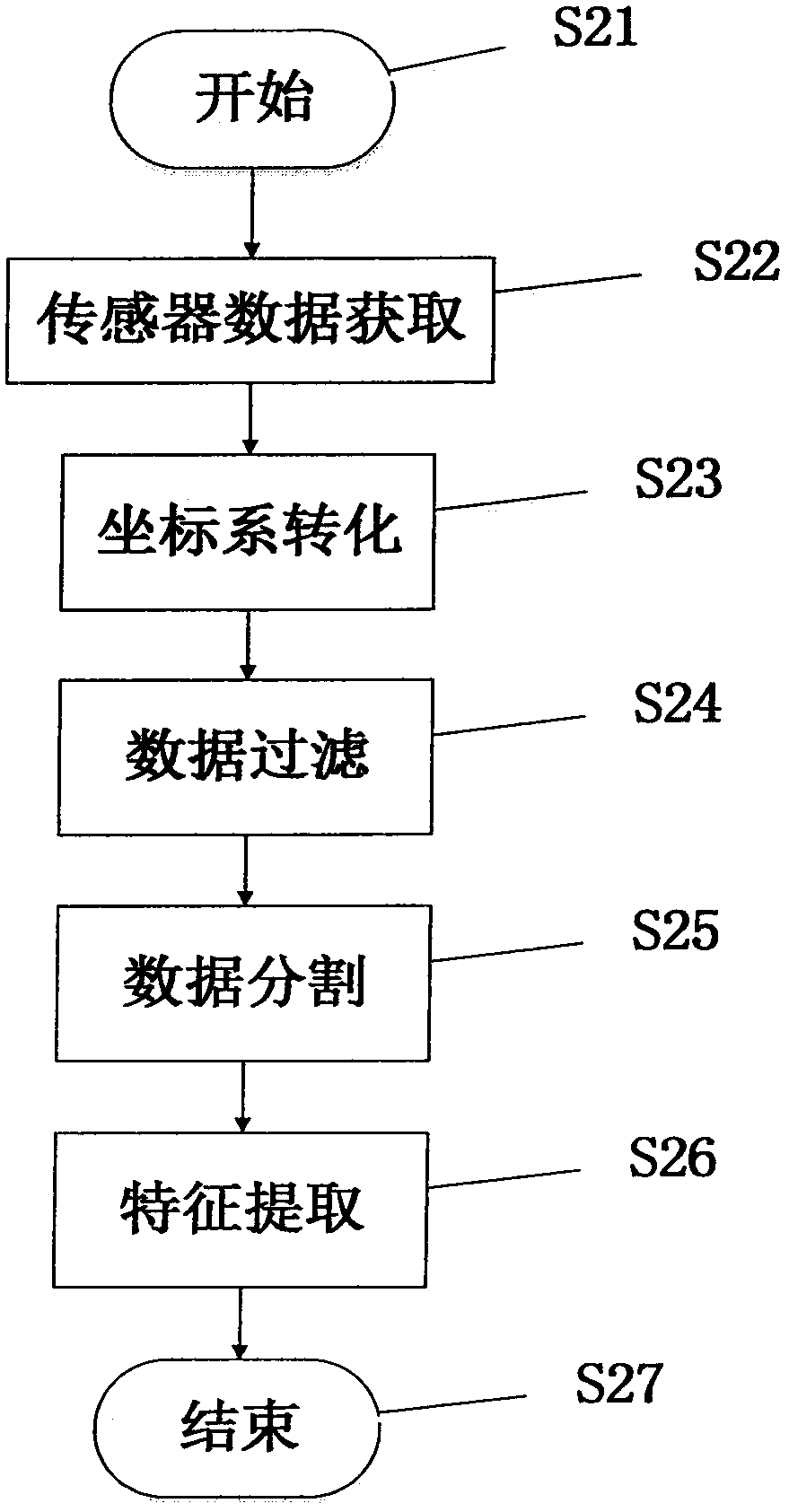
[0126] Embodiment 1 provides a method for collecting data from mobile phone sensors of users in different locations, including the following steps:
[0127] First, the user sets the program to the sample collection mode, selects a location where the sample will be collected from the location options, and at the same time places the mobile phone in the corresponding location. ) above the distance can be. In the process of walking, try to ensure that there is no relative movement between the mobile phone and the body, change the wearing method of the mobile phone, and follow the above steps to re-collect sample data of other wearing methods. Users can define custom wearing methods according to personal needs. and identification.
Embodiment 2
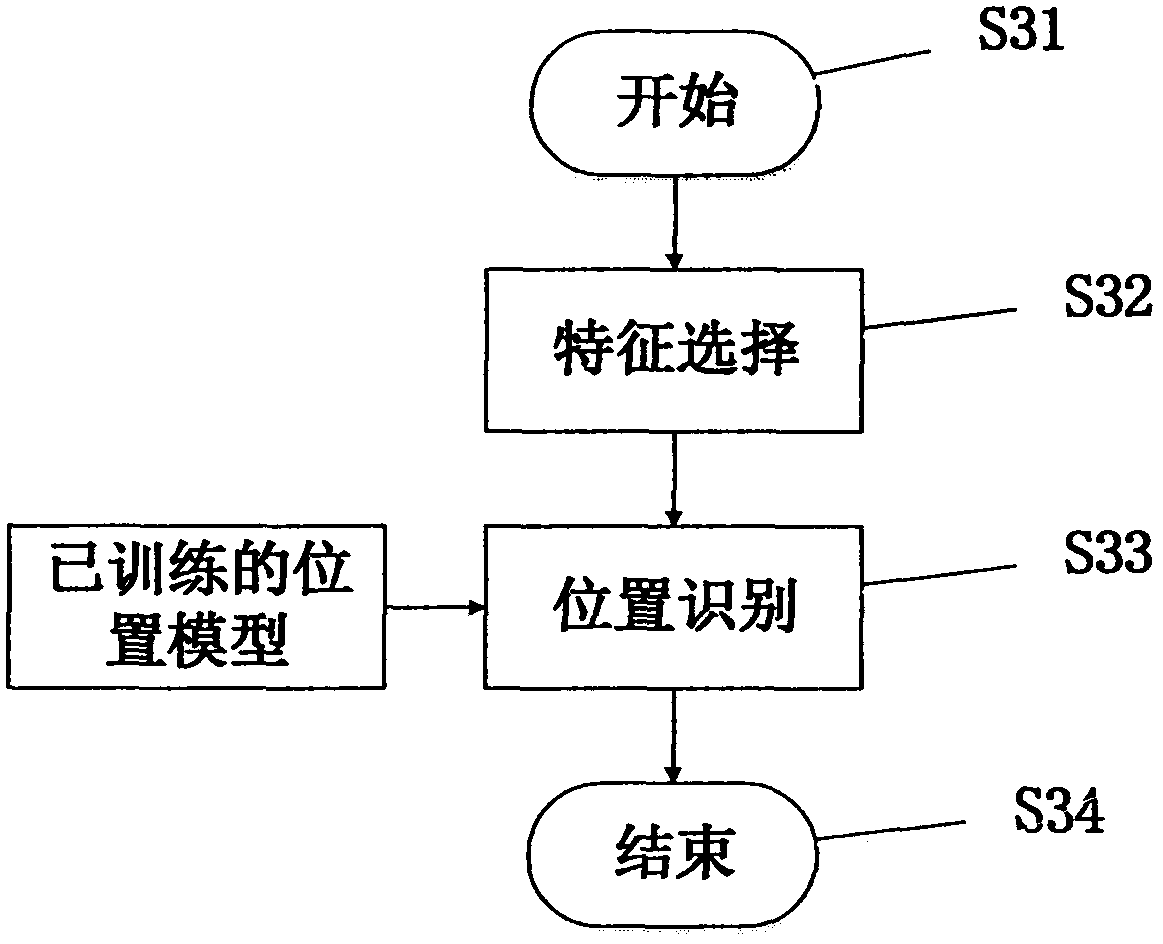
[0129] Embodiment 2 provides an example of mobile phone location information identification, which mainly includes the following steps:
[0130] Taking the user's mobile phone as an example, the collected sensor data is filtered and segmented, and then the SFFS algorithm is used to extract the feature set suitable for location information recognition, and these feature sets are corresponding to the position of the user's hand, and then the DT algorithm is used Train a model for location recognition. Similarly, change the location of the mobile phone (for example: the left pocket of the jacket, the right pocket of the jacket, the waist, the left trouser pocket, the right trouser pocket, etc.), and re-train the model in other positions according to the above steps.
Embodiment 3
[0132] Embodiment 3 provides an example of mobile phone user identification, which mainly includes the following steps:
[0133] In Embodiment 2, we can identify the user's mobile phone wearing method with a high accuracy rate. However, there is still a certain probability of error. In order to solve this problem, in the model training of identity authentication, we can use the data marked with location tags by ourselves for model training of location recognition. At the same time, in a real environment, everyone wears a mobile phone in a very different way, and in the actual operation of our system, the user can also decide which positions to use for identity authentication: For example, user A often The trouser pocket and mobile phone are used to carry the mobile phone, so in the process of location recognition and identity authentication, only the data of the corresponding location is needed to be trained, which is a good solution to the personalized wearing style of each use...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com