User datagram protocol traffic filtering method and device, server and memory medium
A user datagram and traffic filtering technology, applied in the field of network security, can solve problems such as poor effect and difficulty in meeting protection requirements, and achieve the effect of good protection effect and reduced impact.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to make the object, technical solution and advantages of the present invention clearer, the implementation manner of the present invention will be further described in detail below in conjunction with the accompanying drawings.
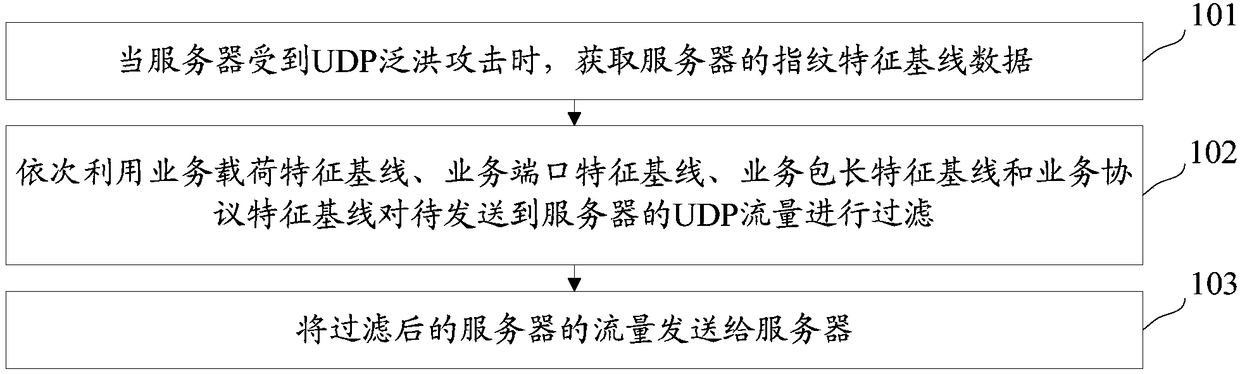
[0025] In order to facilitate the understanding of the technical solutions provided by the embodiments of the present invention, the problems existing in the existing UDP traffic filtering solutions are described below:
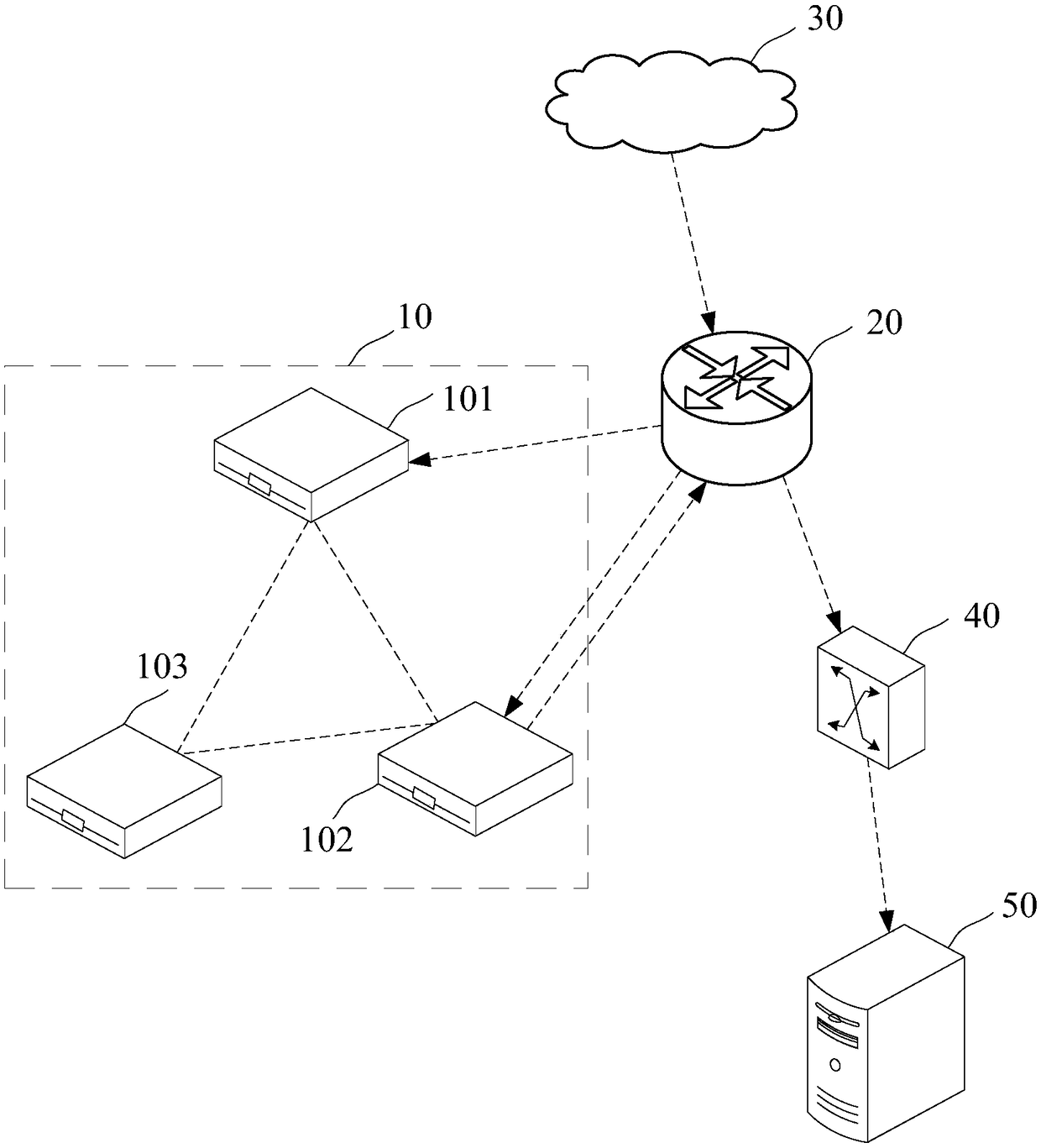
[0026] DDoS attack means that hackers send a large amount of abnormal traffic to the destination server by controlling the dead network distributed in various places. The server is busy processing abnormal traffic, unable to process normal user requests, and even the system crashes, resulting in denial of service. UDP Flood is a very common DDoS attack method. Through a large amount of UDP garbage traffic, server bandwidth is blocked, resulting in business paralysis. Since UDP is a connectionless transport protocol, s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com