Composite identity authentication-based network trading system
A network transaction and identity authentication technology, which is applied in the field of composite identity authentication network transaction system, can solve the problems of inability to adapt to the network transaction environment and lengthy transaction process, and achieve both versatility and security, clear division of public and private, and guaranteed security sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
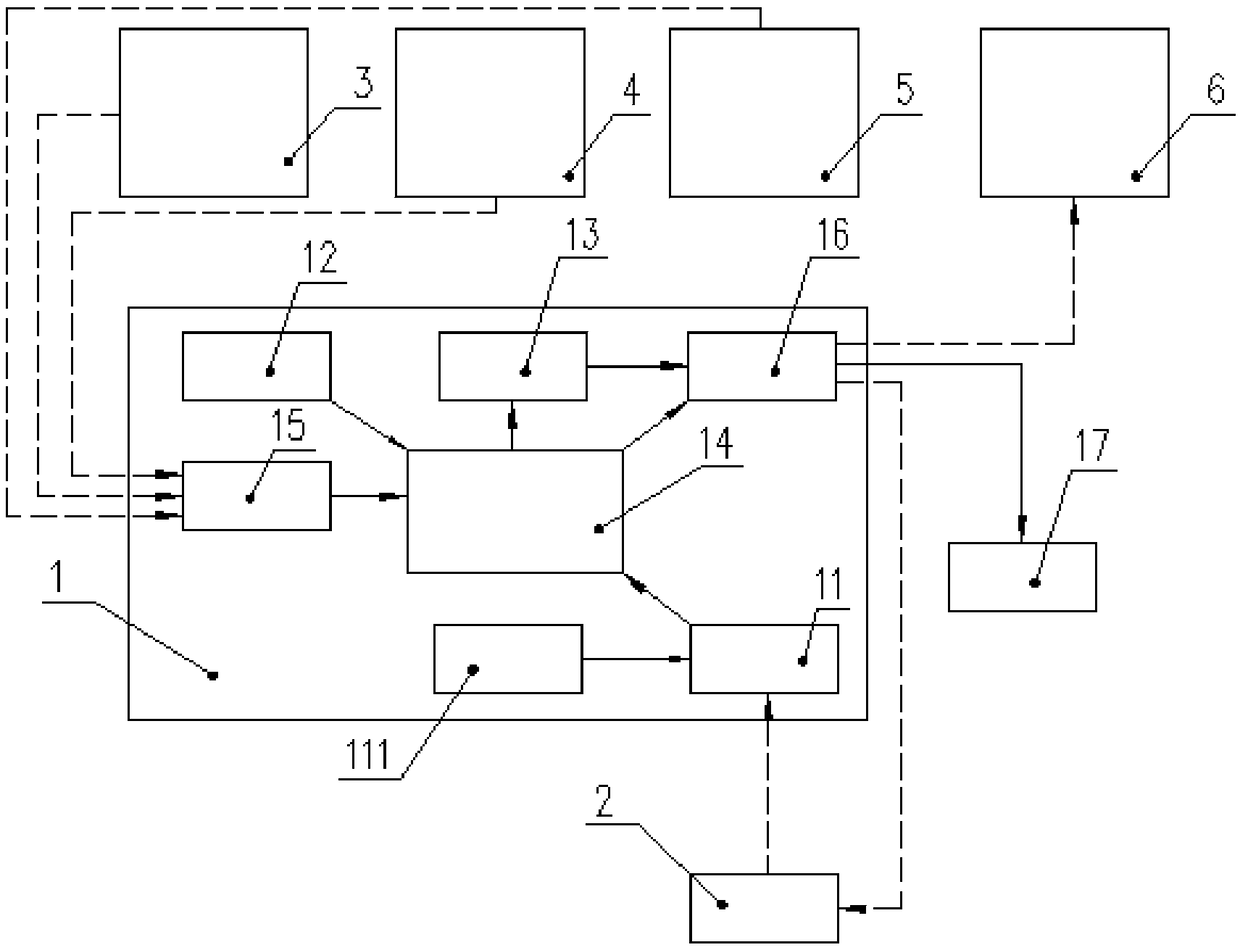
[0033] The network transaction system of composite identity authentication of the present invention, such as figure 1 and figure 2 As shown, it includes a verification device 2 and a plurality of terminals 1, and is characterized in that it also includes: a privacy database 3 for recording the user's private information, a first private chain 4 for recording the authentication and encryption information, and a first private chain 4 for recording the information related to the user. The second private chain 5 and the public chain 6 of the mapping relationship linked by the privacy database 3; each terminal 1 is respectively linked with the first private chain 4, the second private chain 5, and the public chain 6 and forms corresponding network nodes.
[0034] The terminal 1 includes a data input terminal 11 for obtaining external verification information, a read-only storage unit 12 recorded with independent physical information, a temporary storage unit 13, a processing unit ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com