A Verifiably Secure Privacy Enhancement Method for Quantum Key Distribution
A quantum key distribution, security and confidentiality technology, applied in the field of verifiable security and security enhancement, to achieve easy-to-implement effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
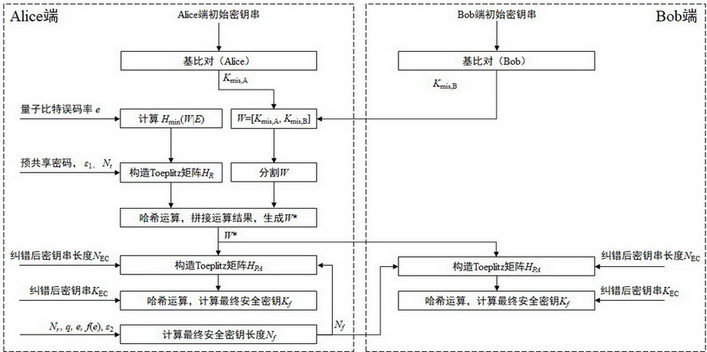
[0034] Such as figure 1 As shown, a verifiable security enhancement method for quantum key distribution of the present invention, the steps are:
[0035] S1: Generate an initial random number string W, and the two communicating parties (Alice and Bob) generate a random number string K respectively during the base comparison process of quantum key distribution mis,A and K mis,B , and then Alice combines the two into a random number string W=[K mis,A ,K mis,B ].
[0036]S101: During the base comparison process of quantum key distribution, when the base selections of Alice and Bob are opposite to each other, the two parties respectively save the random bit strings detected at this time, denoted as K mis,A and K mis,B ;
[0037] S102: Bob sends K mis,B Send to Alice;
[0038] S103: Alice's random number string K mis,A and K mis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com