Unlocking method and device and storage medium
An unlocking and sound lock technology, applied in the field of communication, can solve problems such as low unlocking accuracy and success rate, misreading, and low user experience, so as to improve unlocking accuracy and success rate, avoid misreading, and simplify unlocking operations Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
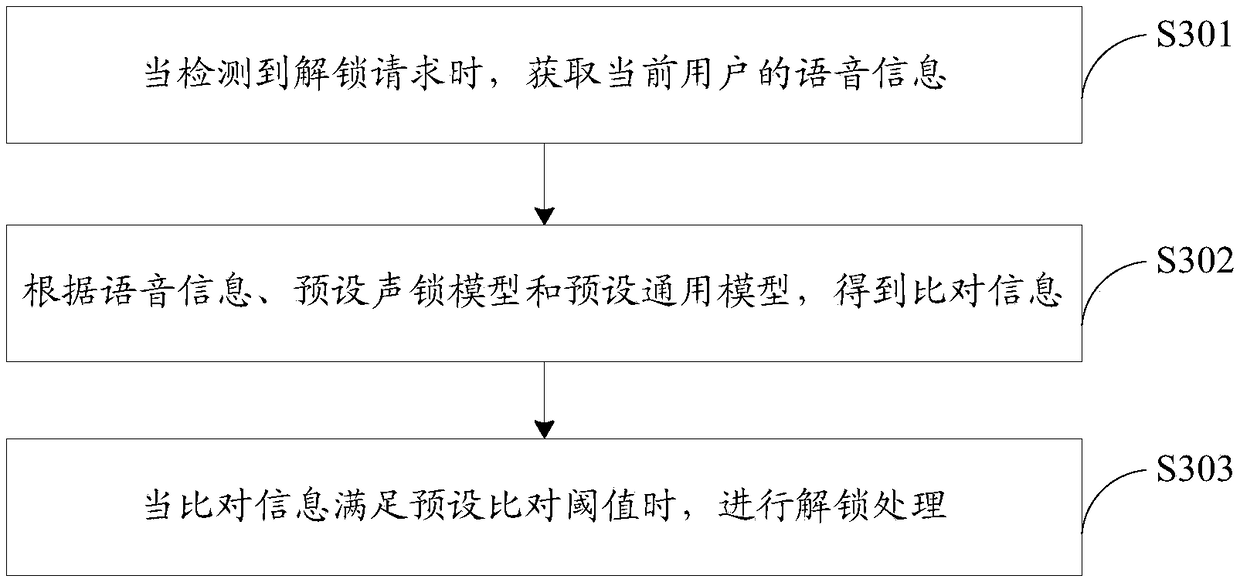
[0067] An embodiment of the present invention provides an unlocking method, image 3It is a schematic diagram of the implementation flow of an unlocking method proposed by the embodiment of the present invention, as shown in image 3 As shown, in the embodiment of the present invention, the unlocking method may include the following steps:
[0068] S301. Acquire voice information of the current user when an unlock request is detected;
[0069] In the embodiment of the present invention, after the terminal and the applications installed on the terminal are locked, on the one hand, the terminal needs to be unlocked to enter the working state; on the other hand, the application needs to be unlocked to complete the user's login.
[0070] Here, when the terminal detects that the unlocking function of the terminal or the application function installed on the terminal is activated, the unlocking request is detected. For example, the user presses on a locked screen, or the user star...
Embodiment 2
[0094] The embodiment of the present invention also provides another unlocking method, Figure 6 It is a schematic diagram of the implementation flow of another unlocking method proposed by the embodiment of the present invention, as shown in Figure 6 As shown, in the embodiment of the present invention, the unlocking method may include the following steps:
[0095] S601. Collect historical voice information through a voice device;
[0096] In the embodiment of the present invention, the voice data on which the preset sound lock model is established is derived from historical voice information automatically recorded by the terminal and generated when the user operates the terminal. The user operation may be, but not limited to, answering / dialing calls, historical voice information generated during text messages, WeChat and QQ voice / video calls. Therefore, the terminal needs to collect historical voice information through a voice device. Here, the voice device can be a micr...
Embodiment 3
[0125] Based on the same inventive concept of embodiment one and embodiment two, Figure 7 A schematic structural diagram of an unlocking device provided by an embodiment of the present invention, such as Figure 7 As shown, the unlocking device includes: a processor 71 , a memory 72 , a receiver 73 and a communication bus 74 .
[0126] In the embodiment of the present invention, the communication bus 74 is used to realize connection communication between the processor 71, the memory 72 and the receiver 73; the processor 71 and the receiver 73 are used for Execute the data sending program stored in the memory 72 to perform the following steps:
[0127] When an unlock request is detected, the voice information of the current user is obtained; according to the voice information, the preset sound lock model and the preset general model, comparison information is obtained; when the comparison information meets the preset comparison threshold, Perform unlock processing.
[0128] I...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com