Elliptic curve radio frequency identification authentication method based on resource-constrained tag
An elliptic curve and radio frequency identification technology, applied in the information field, can solve the problems of high communication overhead, consumption of storage resources, poor security performance, etc., and achieve the effect of wide application range, low security and strong practicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
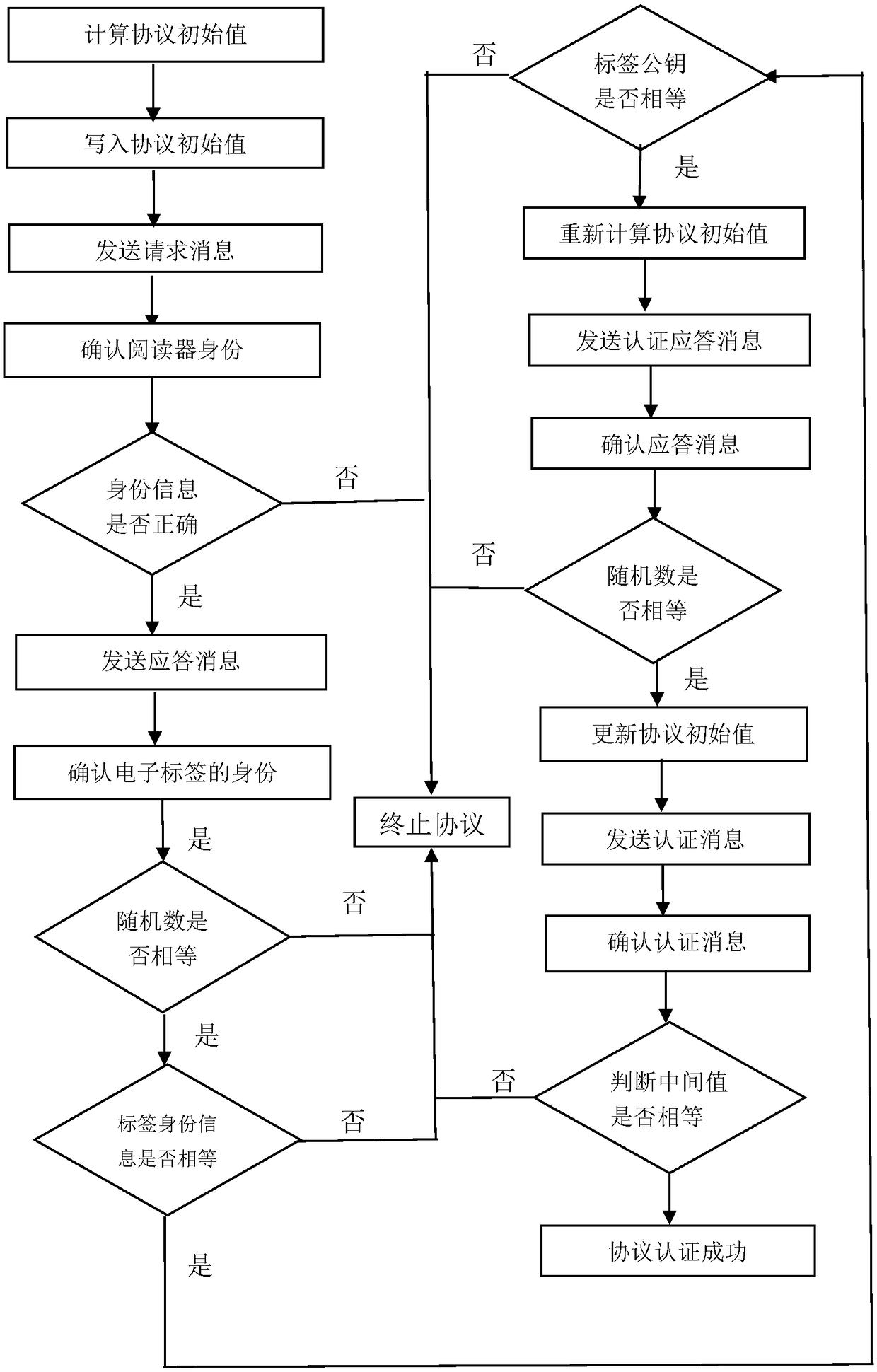
[0056] Attached below figure 1 , further describe the concrete steps of the present invention:
[0057] Step 1, calculate the protocol initial value.
[0058] The reader generates a random number r v , using the operation of multiplying the point on the elliptic curve by the base point, a pair of stored values (r v ,U v ).
[0059] The reader uses the Photon hash function to combine the reader's private key with the stored value (r v ,U v ) in U v The dot product value is hashed to get a session key k v .
[0060] Step 2, write protocol initial value.
[0061] The identity information of the electronic tag and the public key of the electronic tag are pre-stored in the reader.
[0062] The reader will store the value (r v ,U v ), session key k v And the identity information of the reader is written into the electronic tag in advance.
[0063] The initial value of the reader writing protocol refers to that the reader pre-writes a pair of storage values (r v ,U...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com