Weakly secure multicast transmission topology construction method based on network coding for integer transmission rate
A technology of transmission rate and network coding, applied in the field of secure multicast data transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
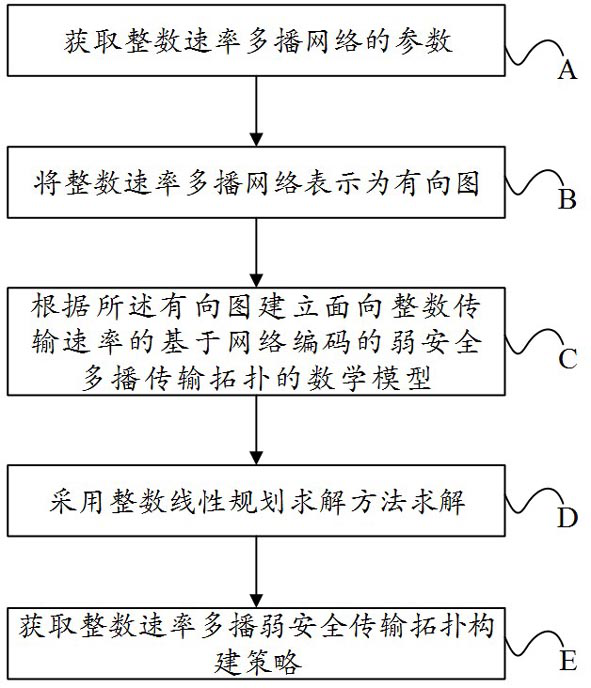
[0033] Example: see figure 1 Shown is a flow chart of a network coding-based weakly secure multicast transmission topology construction method for integer transmission rates.
[0034] Specific methods include:
[0035] A: Obtain the parameters of the network where the weak security multicast based on network coding of the integer transmission rate is located.
[0036] The specific parameters of the network where the weak security multicast based on network coding with the integer transmission rate is located are:
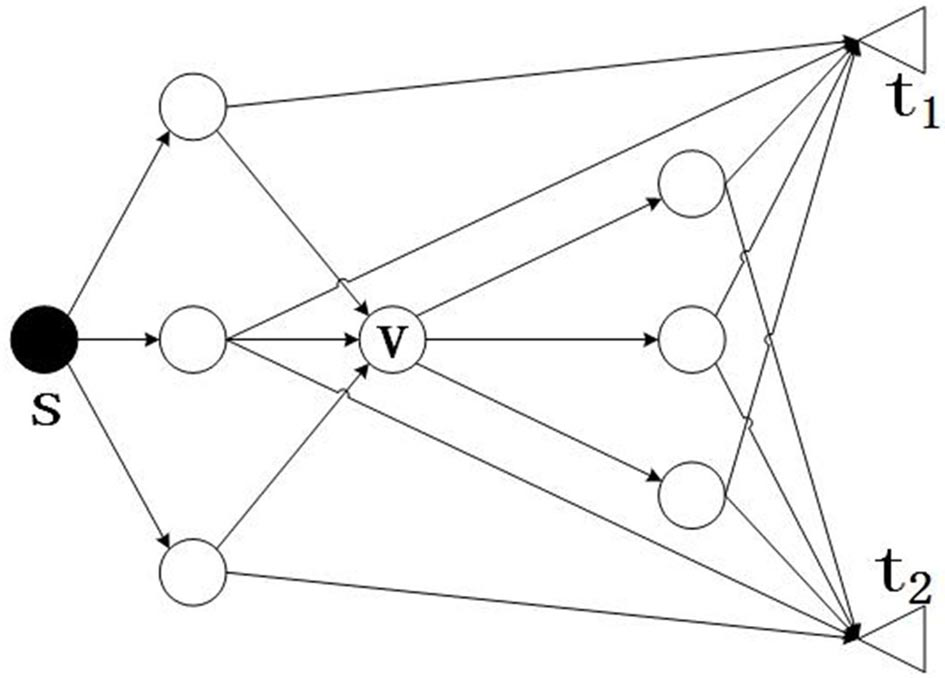
[0037] A1: Expresses the set of node parameters in the network where the multicast is located (including the source node of the multicast, all destination nodes, other nodes, namely intermediate nodes);
[0038] A2: Express the parameters of the link in the network where the multicast is located: whether there is a communication link; the capacity of the communication link between nodes, that is, the highest transmission rate;
[0039] A3: Parameters related to c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com