Preposed audit method
A data packet and network registration technology, applied in the direction of electrical components, transmission systems, etc., can solve problems such as system bottlenecks, low efficiency, and inflexible audit methods, and achieve the effect of reducing hardware requirements, reducing complexity, and improving audit efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention is further described below in conjunction with accompanying drawing and embodiment:
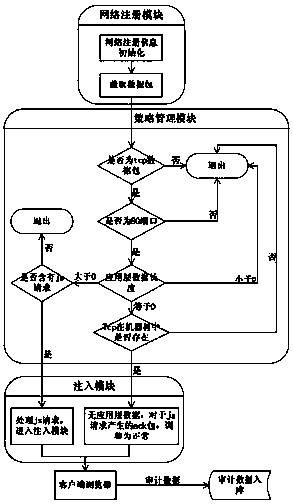
[0031] like figure 1 As shown, a pre-audit method completes the audit analysis behavior through the audit system, wherein the audit system is pre-installed on the client browser, and the audit analysis behavior on the original audit device is pre-installed on the client browser to complete , to share the original responsibility of auditing equipment.
[0032] The network data packets are intercepted through the netfilter system framework, by matching the relevant strategies for the intercepted data packets, by modifying the last data packet in the data packet flow, and inserting the corresponding js before it, and the js obtains the necessary information in the client browser. information to enable the audit process.
[0033] The audit system includes a network registration module, a policy management module and an injection module.
[0034] 1. The network regi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com