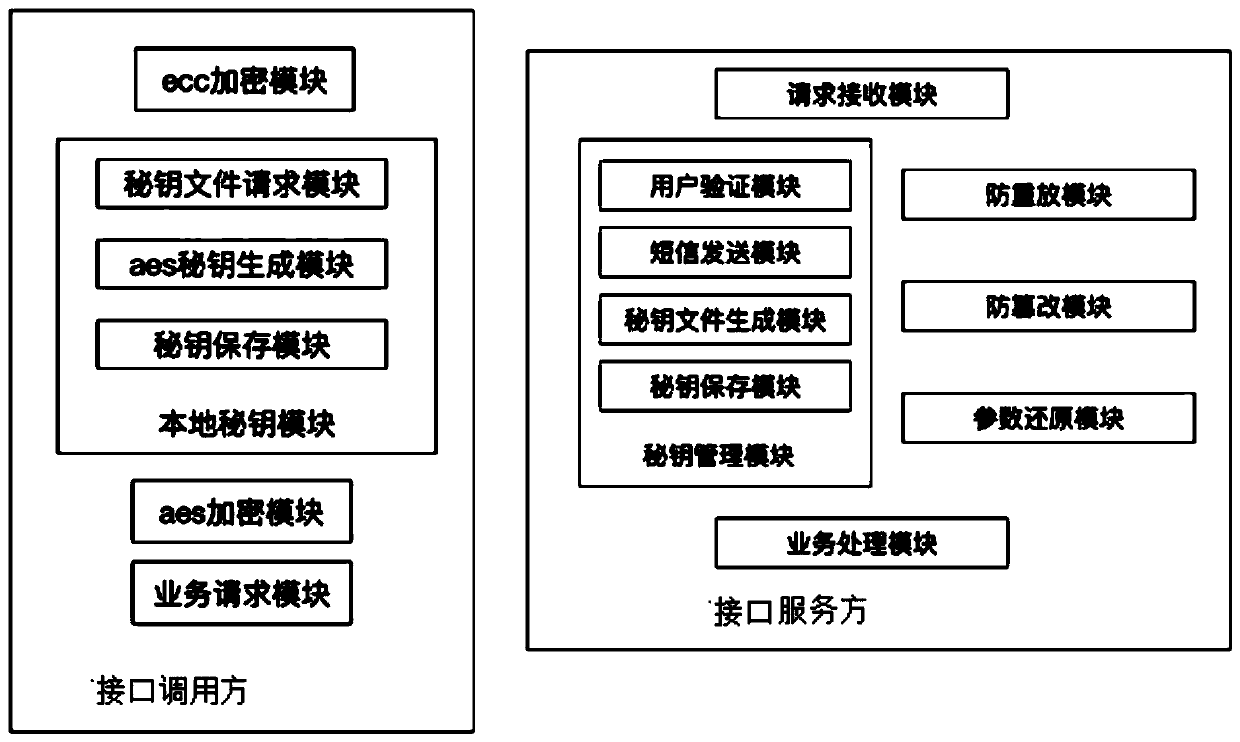
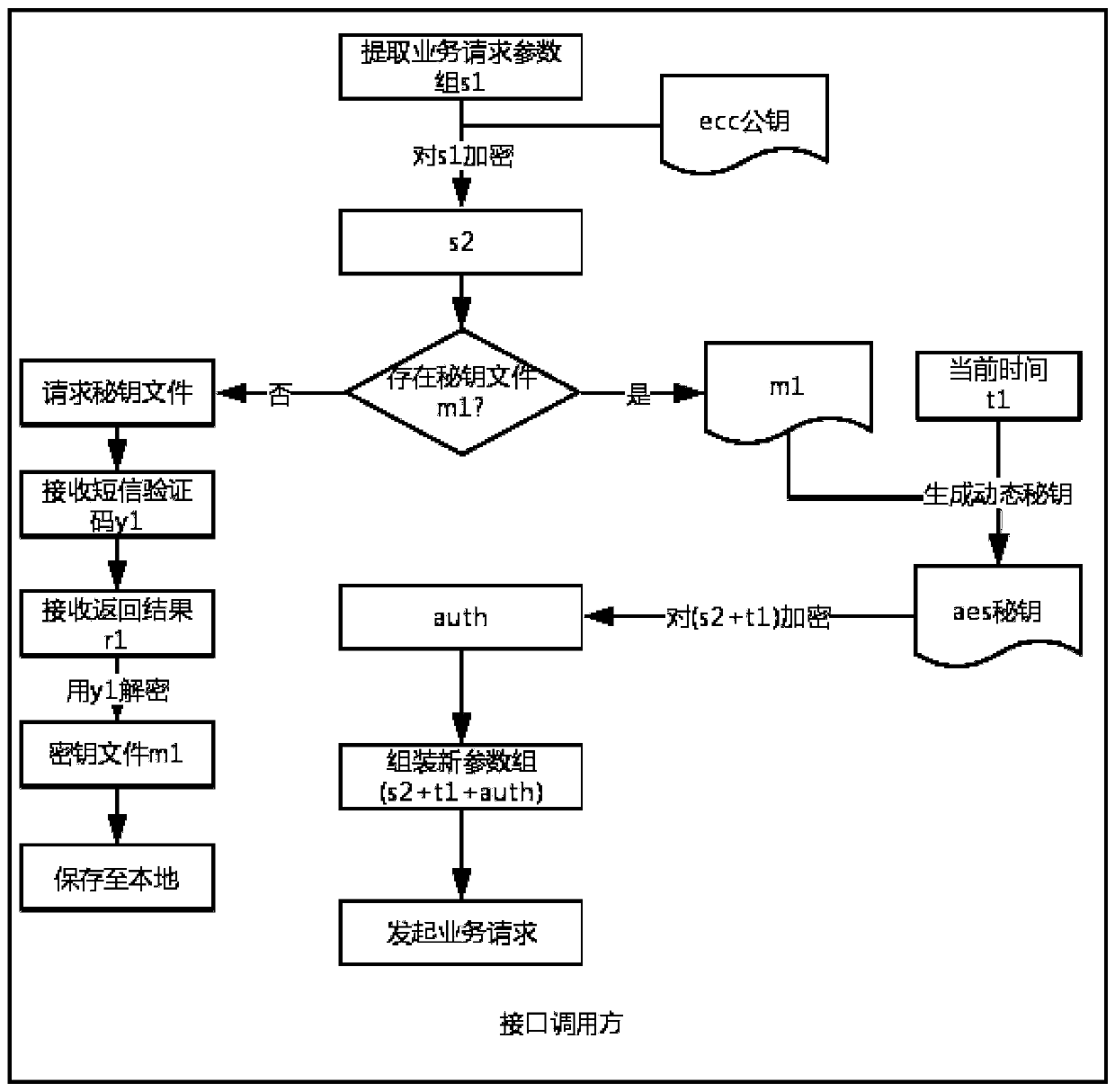
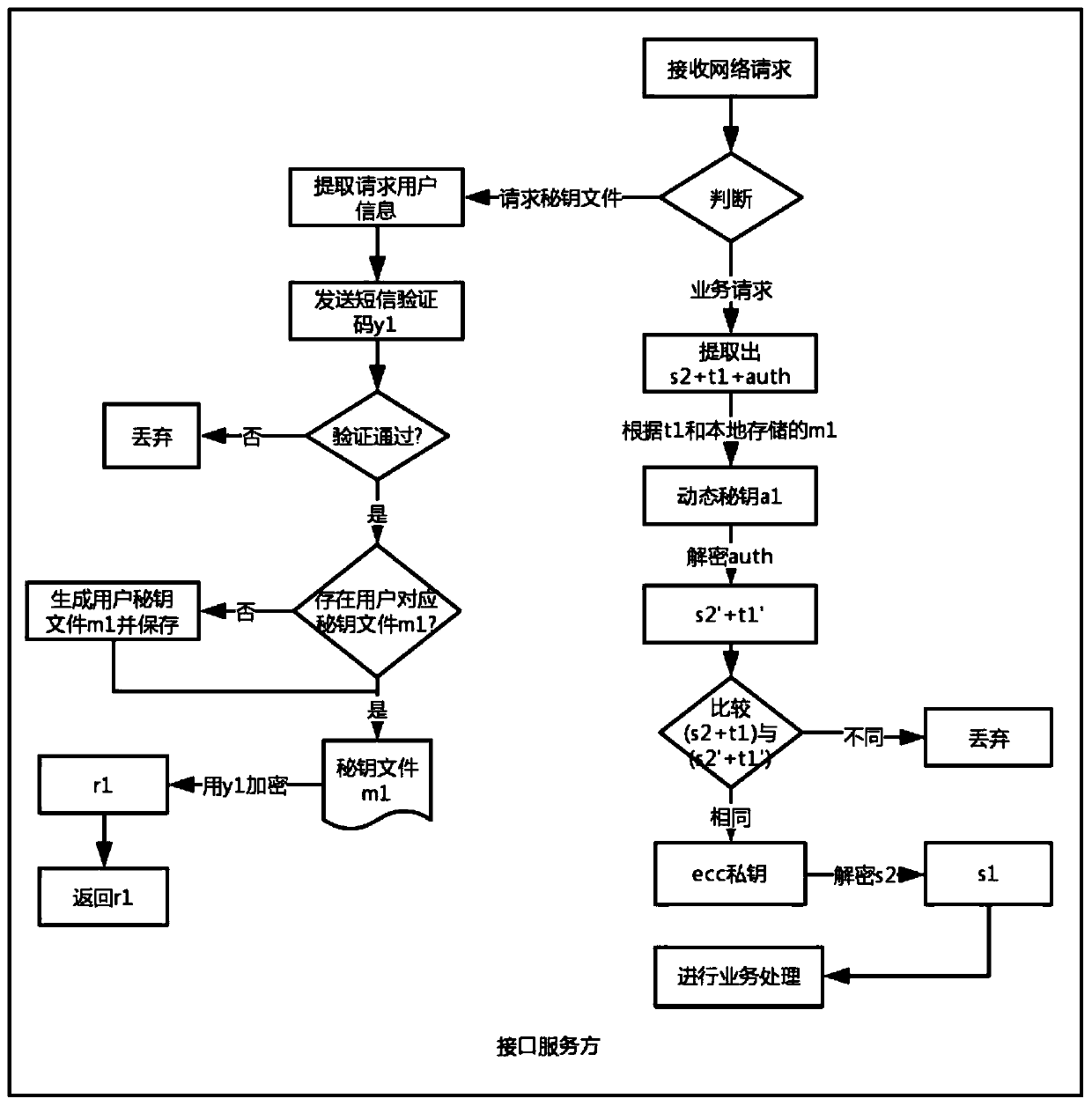
A microservice interface security call device
A technology for interface invocation and secure invocation, applied in the field of microservice systems, it can solve the problems of inability to prevent tampering attacks, replay attacks, and third-party attacks, and achieve improved security, high feasibility, and interface invocation. safe effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 2
[0078] In order to design a dynamic key generation rule with reliable operation and high security performance, the dynamic key generation rule:
[0079] Step 1. Let the key file m1 be a matrix array X1, the matrix array X1 has m rows and n columns, m is equal to the length of the key, and n is equal to 10;
[0080]Step 2: Use the time t1 to superimpose into a calling reference array X2, and the number of elements in the calling reference array X2 is equal to m;
[0081] Step 3: Take each key element from the key file m1 in turn according to the value of each element in the reference array X2, and all the key elements form an array-shaped key a1 in turn: Let the i-th key element of the key a1 For a1i, the value of the i-th element in the reference array X2 is equal to X2i, then a1i is equal to the value of the i-th row and column X2i+1 in the matrix array X1.
[0082] Example: array of matrices (That is: m=18, n=10), t1=20180116104106 (representing 10:41:06 on January 16, 20...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com