Block chain technology-based storage method and computer readable storage medium
A block chain technology technology, applied in the field of computer-readable storage media, servers, and storage methods based on block chain technology, can solve problems such as obtaining private keys, difficulty in obtaining private keys, and inability to trade account funds, etc., to achieve good results Effect of management and improvement of convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
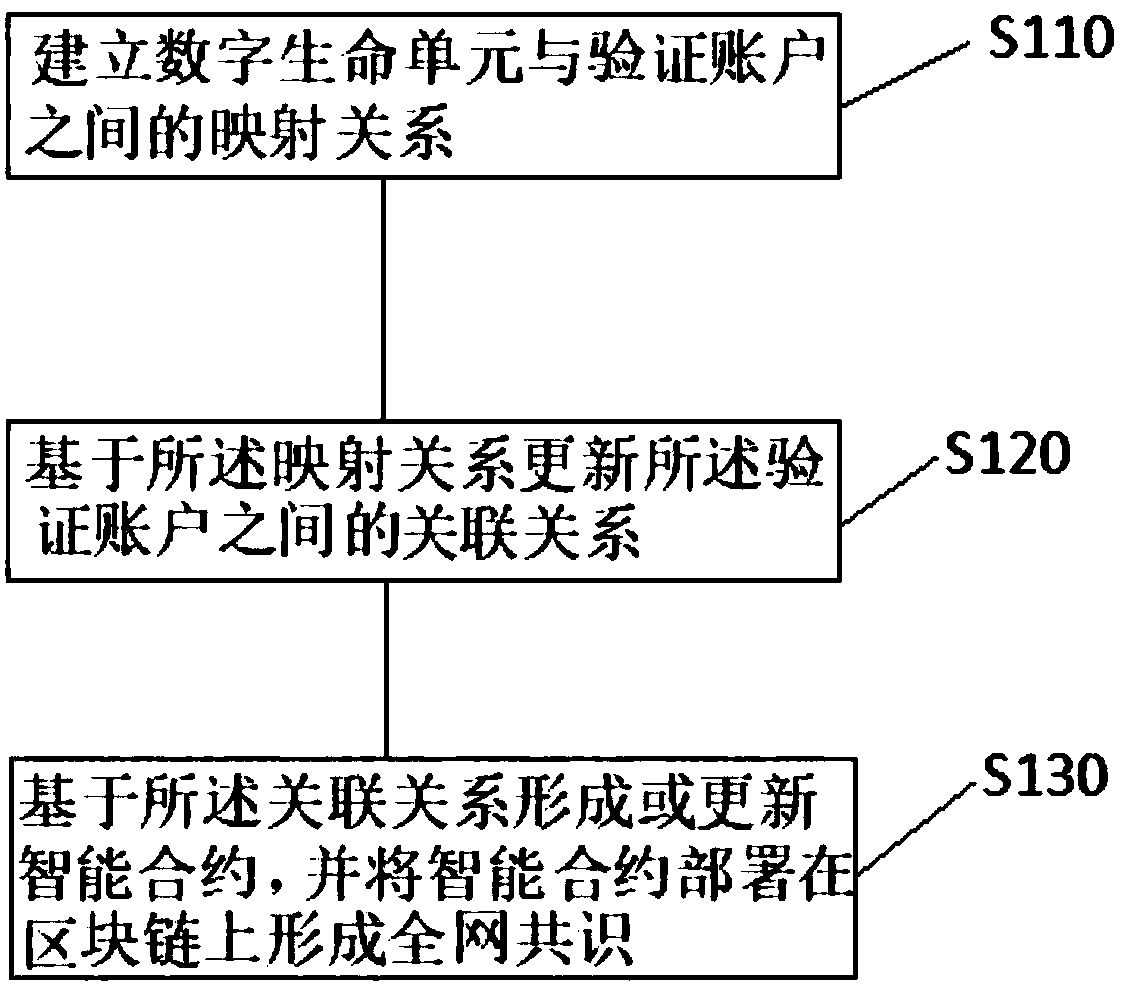
[0029] figure 1 It is a flowchart of a storage method based on blockchain technology in Embodiment 1 of the present invention. This embodiment is applicable to the storage of any electronic data. The method can be executed by an independent storage device, and can also be configured in a server for application. Such as figure 1 As shown, the method can be applied to new blockchains as well as established blockchains, including:
[0030] Step S110, establishing a mapping relationship between digital life units and verification accounts; digital life can also be called siliconized life, which is a new life form created by electronic media such as computers, and is a digital life with natural life characteristics or behaviors. system, the digital life unit at least includes identity information and biometric information corresponding to the digital life source. The verification account includes at least identity information and social data of the account creator.
[0031] Sch...
Embodiment 2
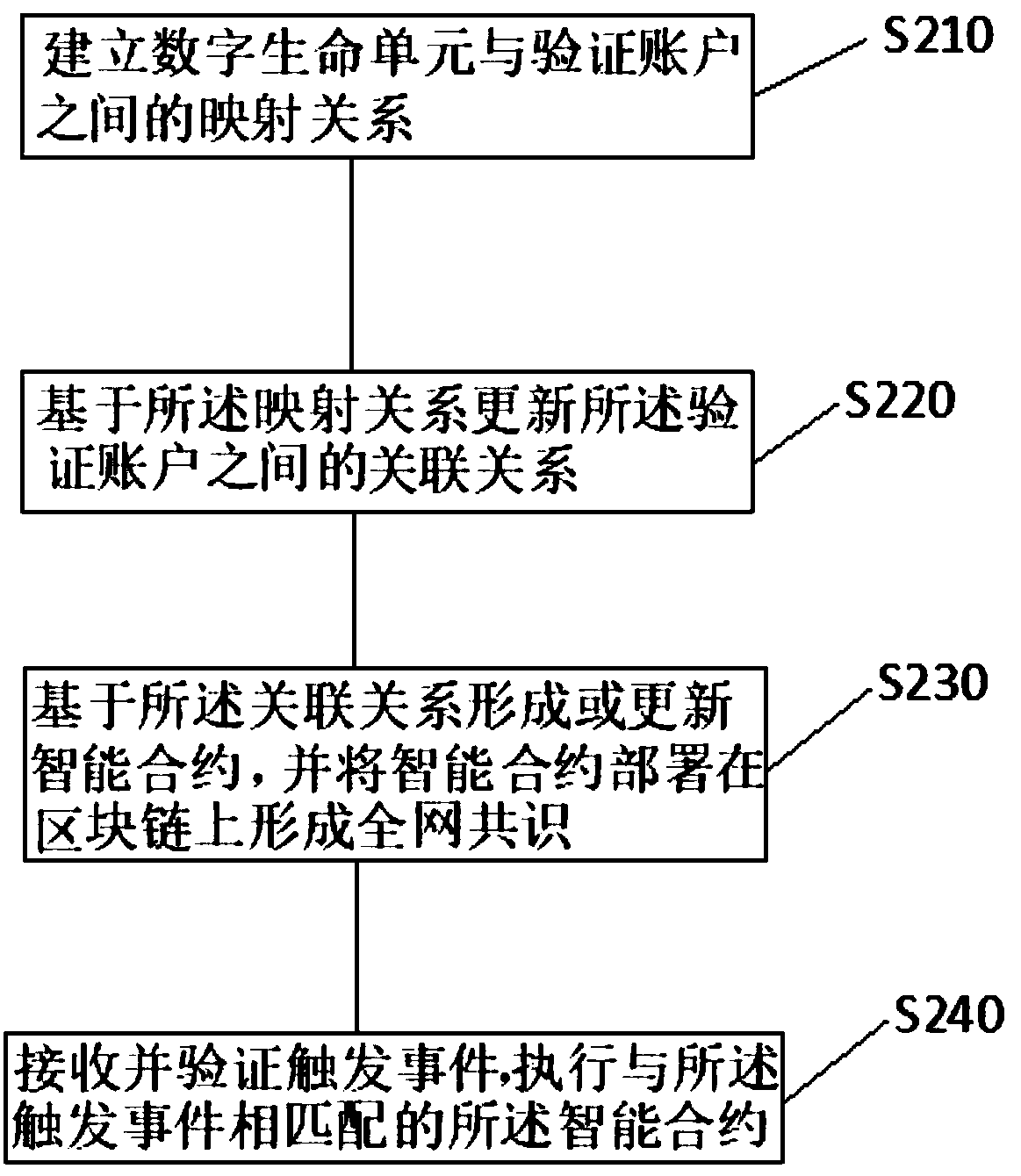
[0043] The first embodiment above can establish various relationships between the digital life unit and the verification account, and between the verification accounts. Based on the above relationship, the user can avoid being unable to read or operate the verification account due to the loss of the key. The result is still Only the account holder can read or operate the verification account, but if the account holder is insane or unable to read the account for other objective reasons, the verification account of the holder still cannot be verified. enabled. Based on this, if figure 2 As shown, the present invention further provides a storage method based on block chain technology, specifically:
[0044] Step S210, establishing a mapping relationship between digital life units and verification accounts; digital life can also be called siliconized life, which is a new life form created by electronic media such as computers, and is a digital life with natural life characterist...
Embodiment 3
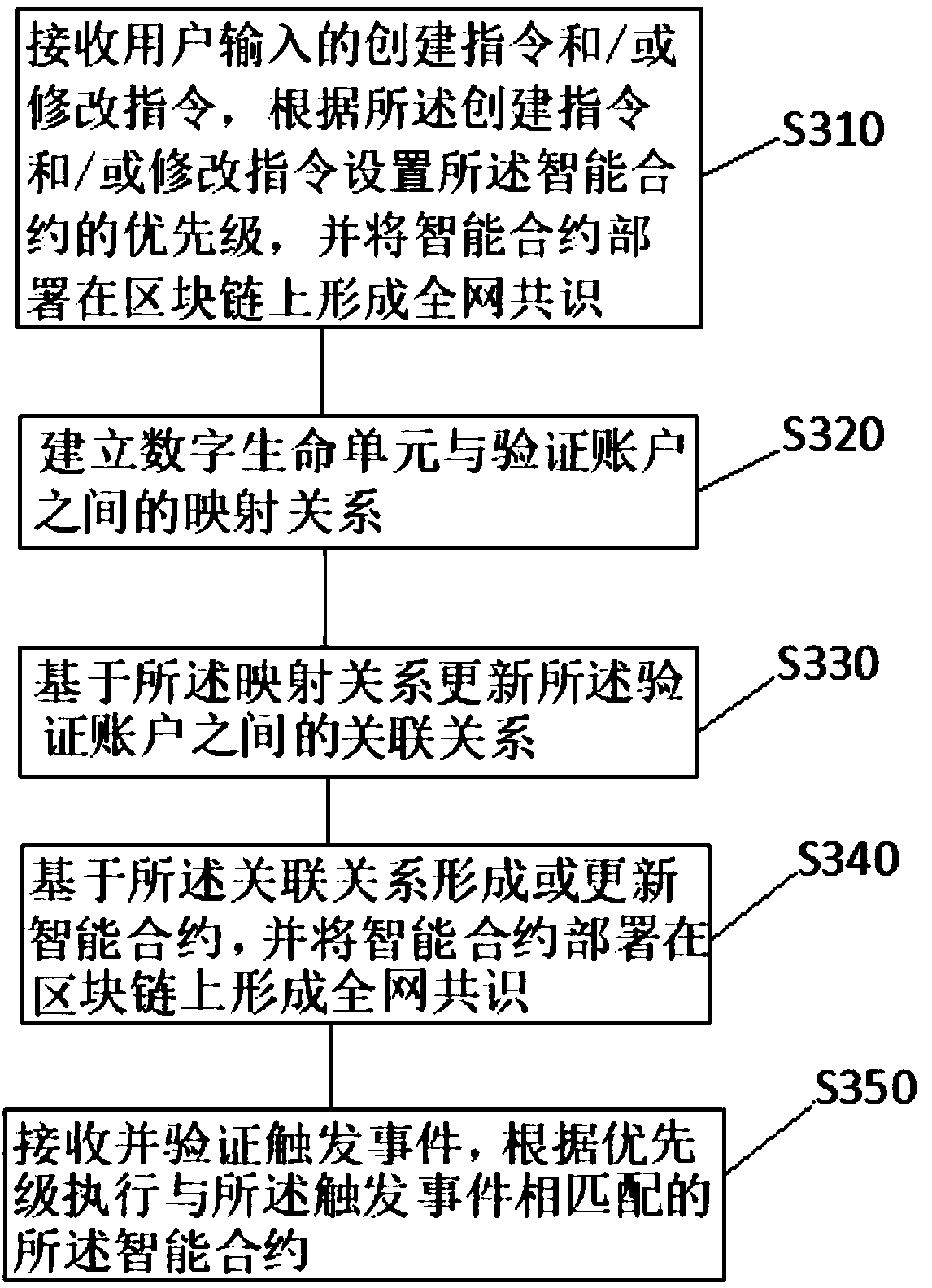
[0052] The second embodiment above solves the technical problem that the account holder's verification account cannot be activated when the account holder is insane or unable to read the account due to other objective reasons. The solution is to trigger When the time is verified as true, execute the smart contract that matches the trigger event, but there is still a technical problem in this technical solution, that is, the states of at least two smart contracts that match the trigger time Under this circumstance, smart contracts cannot be executed in an orderly manner.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com