Identity key file signing and verifying method
A verification method and identification technology, which is applied in the field of signing documents with identification keys and verification, and can solve problems such as the inability to realize the originality verification of signed documents
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
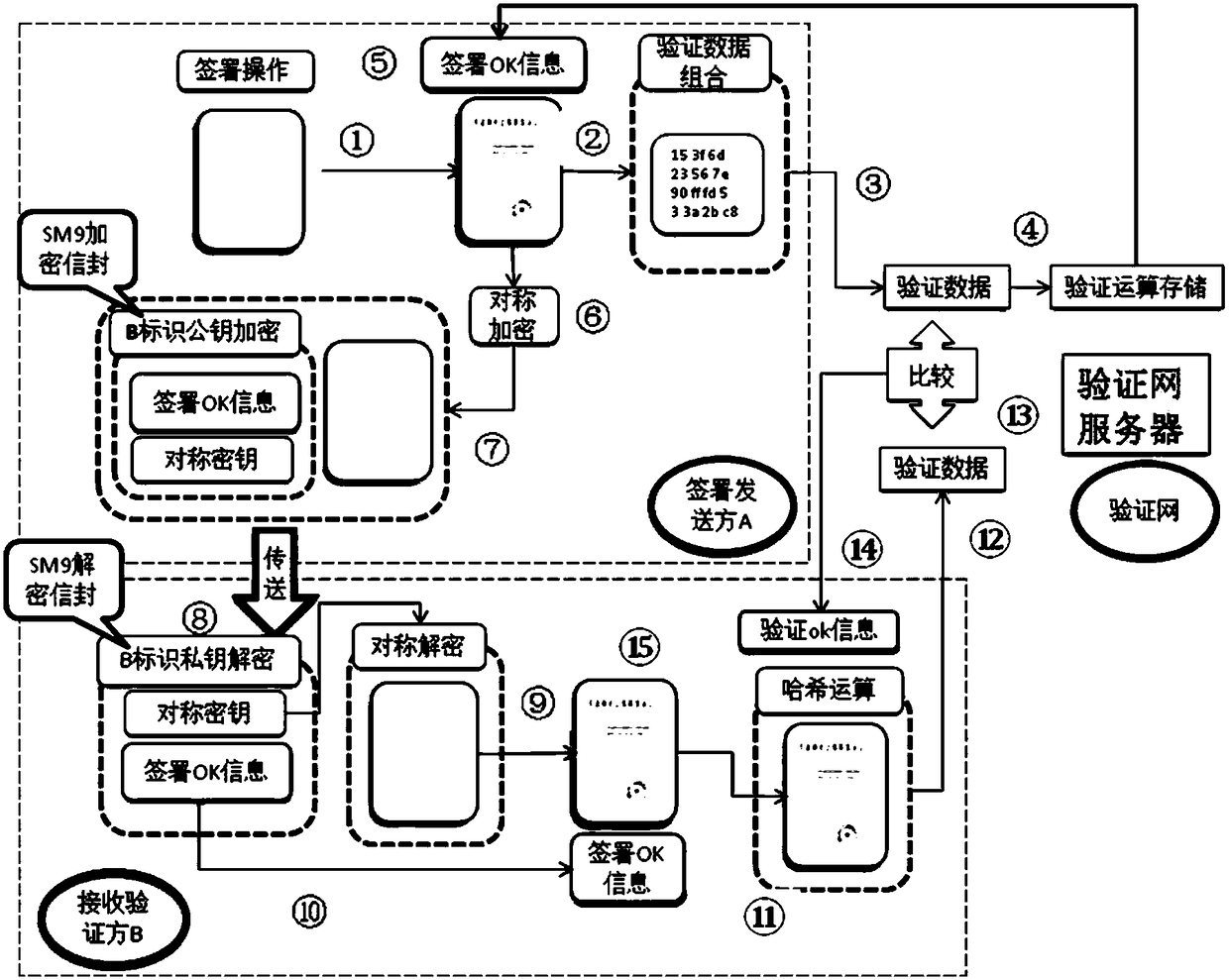
[0100] Embodiment: use the identification key to sign the document and the verification method to form a system, the system is to sign the document part and the verification part of the signed document by the identification key graphic, and use the Internet electronic document security signature composed of the identification key sending and document verification part , sending system;
[0101] (1) The identification key signing and signing verification parts include:
[0102] 1) Signer: identify the signer disk, card hardware and embedded identification graphics encryption algorithm, time-controlled random function update algorithm and electronic evidence data storage program;
[0103] 2) Client: The client operates the computer hardware and the built-in identification key signing operation algorithm, signature electronic evidence generation, storage algorithm, and verification network data exchange program;
[0104] 3) Verification network: Sign the verification terminal ne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com