Message authentication method and system based on quantum key card
A message authentication and quantum key technology, applied in transmission systems, digital transmission systems, and key distribution, can solve the problem of not being deciphered and not getting right and clear, to ensure security, reduce consumption, and reduce the consumption of data processing resources. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
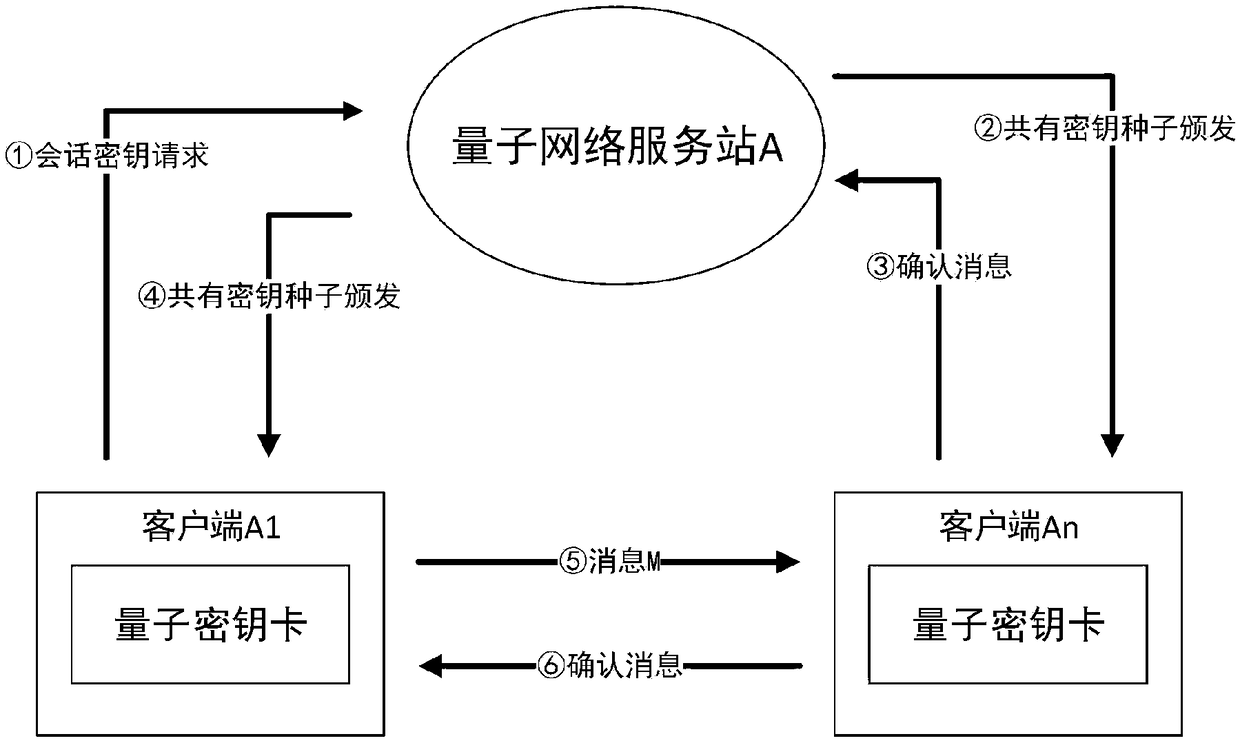
[0066] In this embodiment, the client A1 and the client An belong to the same quantum network service station, which has a quantum service center A, which can be regarded as the message authentication between the client A1 and the client An in the local area network. When there is direct communication between two clients, the public key issuance method required for message authentication is as follows: figure 2 shown.
[0067] Message authentication specifically includes the following steps:
[0068] Step 1.1: Quantum network service station A receives the common key request from client A1 and performs message authentication
[0069] 1.1.1 Start of message authentication: Client A1 first establishes a communication connection with the matching quantum key card.
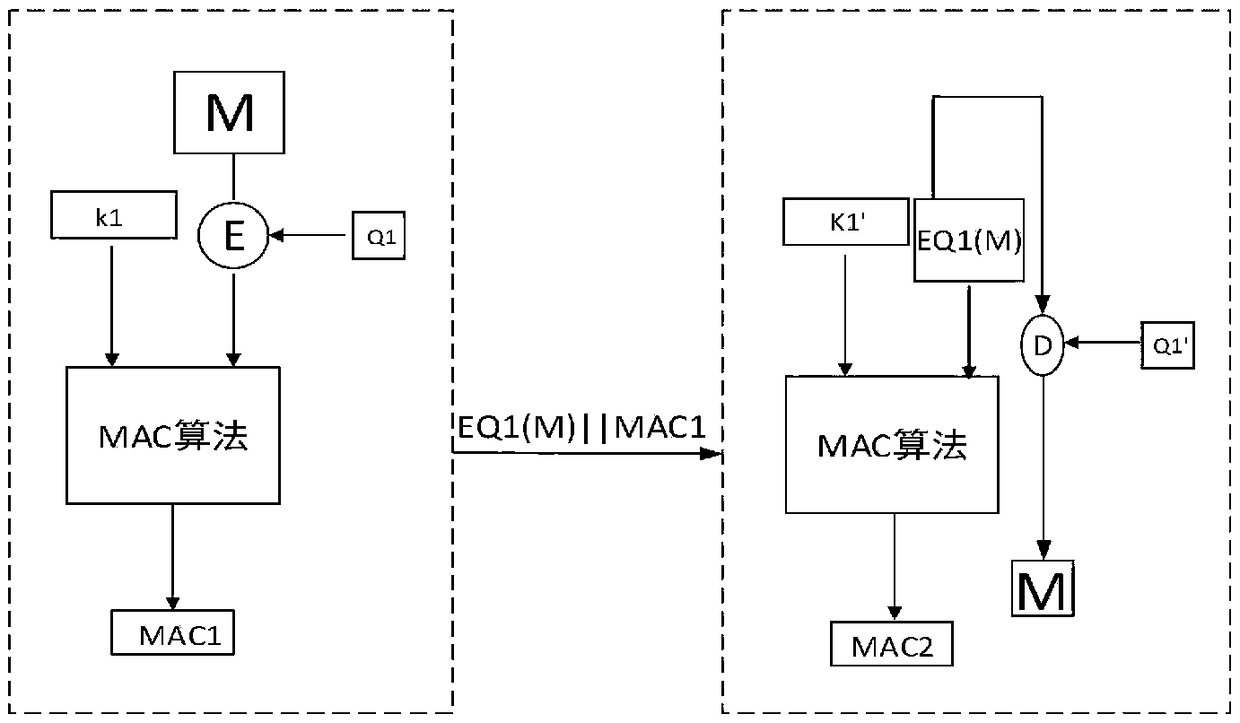
[0070] 1.1.2 User-side message authentication key generation: the quantum key card obtains the key K1 and key Q1 according to the stored key seed SS and the random number generated by the random number generator in...
Embodiment 2
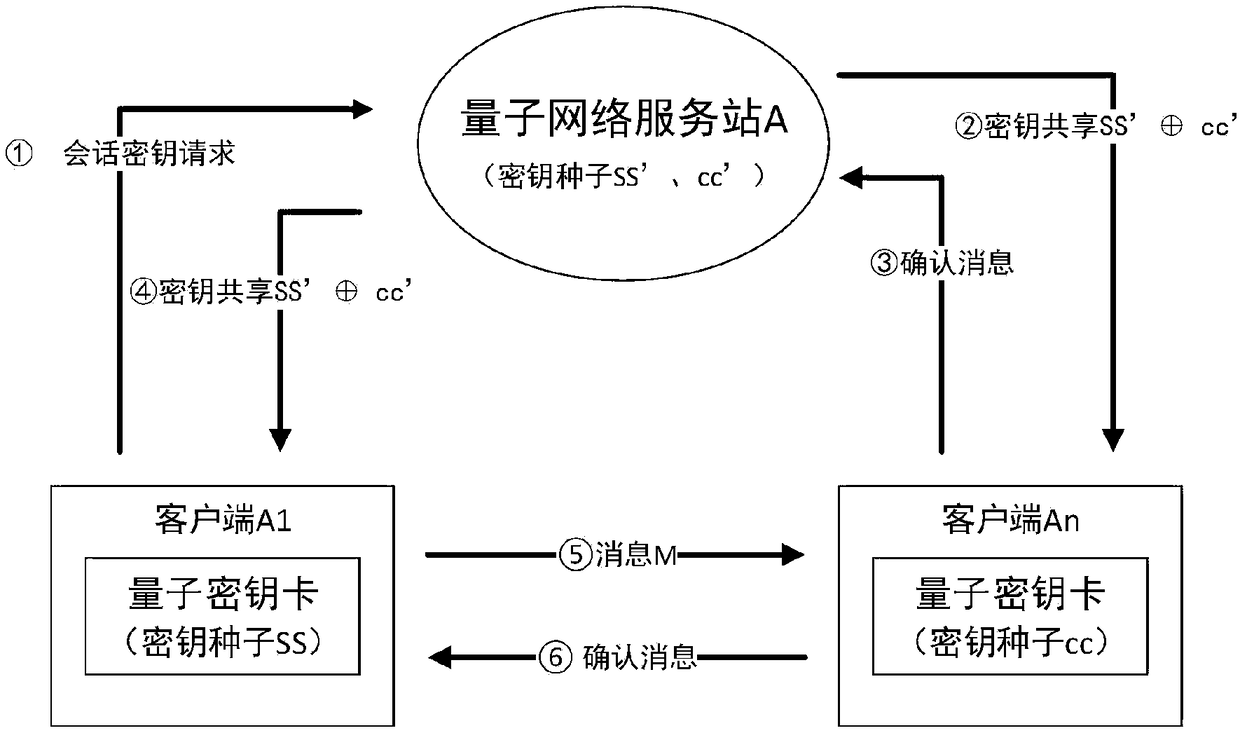
[0103] Such as image 3 As shown, the difference between the message authentication system of this embodiment and that of Embodiment 1 is that a different common key seed generation method is adopted. In this embodiment, the source of the common key for the communication between client A1 and client An is to XOR and encrypt the two corresponding key seeds stored in quantum network service station A for A1 and An respectively, and send them to the client respectively A1 and An. The corresponding key seed may be the key seed used by the quantum network service station A to communicate with the client A1 and the client An, or two other key seeds may be used, and the former is used in this embodiment.
[0104] In this embodiment, message authentication includes the following steps:
[0105] Step 2.1: Quantum network service station A receives the common key request from client A1 and performs message authentication
[0106]2.1.1 Start of message authentication: Client A1 first ...
Embodiment 3
[0119] Such as Figure 4 As shown, the difference between the message authentication system of this embodiment and Embodiment 1 lies in the issuing method of the common key, including the following steps:
[0120] Step 3.1: Quantum network service station A receives the common key request from client A1 and performs message authentication
[0121] 3.1.1 Start of message authentication: Client A1 first establishes a communication connection with the matching quantum key card.
[0122] 3.1.2 Generation of session key request: the quantum key card uses a random number generator to generate a random number N1 as the unique identifier of this service, and appends the request information R of this session key to generate a session key Request M1.
[0123] 3.1.3 The user side sends a session key request and performs message authentication: the matching quantum key card of client A1 packs the session key request and sends it to quantum network service station A. Quantum network ser...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com