A kind of wifi security authentication method
A security certification, the only technology, applied in the Internet field, can solve problems such as easy password leakage, to achieve the effect of avoiding password leakage and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
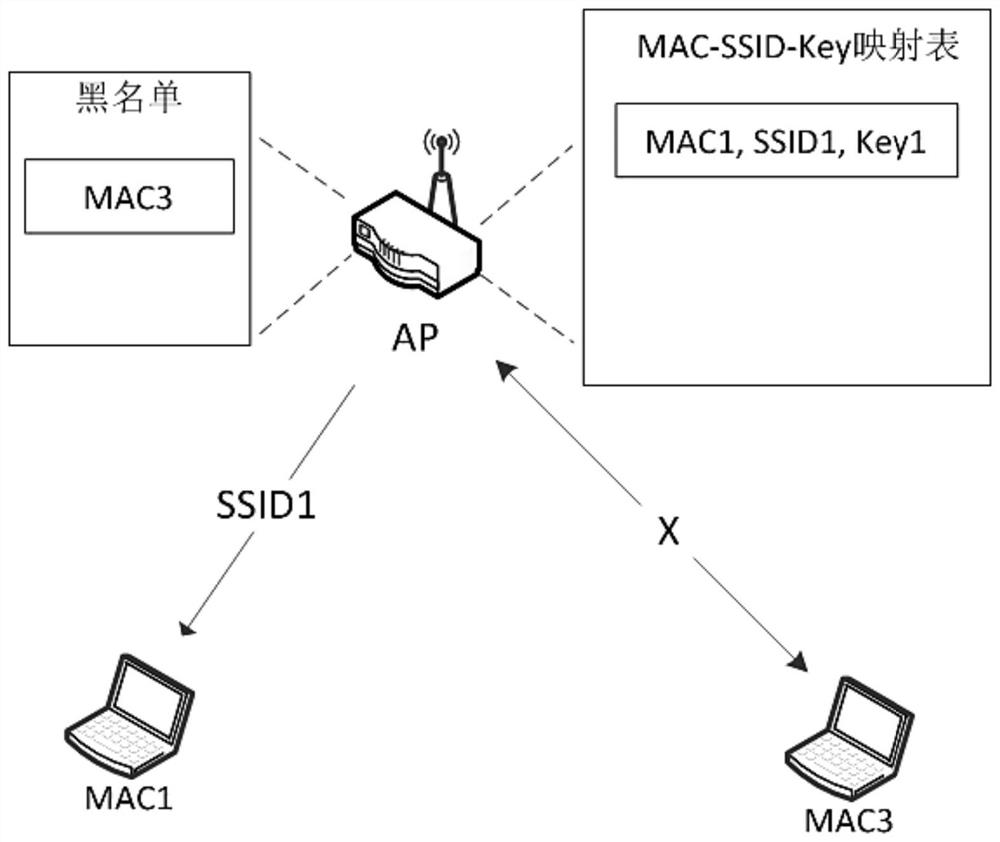
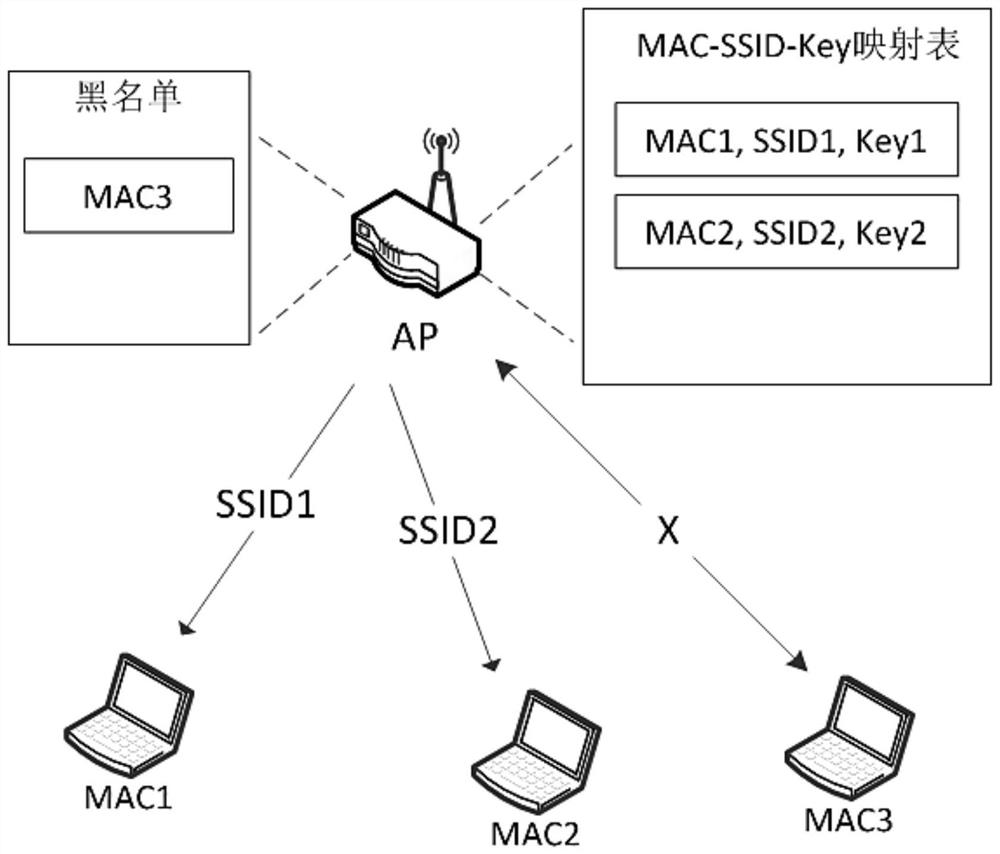
[0022] WiFi has a risk of password leakage. The root cause is that all users use the same SSID and password to access an AP. The present invention realizes the same WiFi, and the SSID and password accessed by each STA are different, so that the problem of password leakage can be avoided, thereby ensuring the security of WiFi access authentication.
[0023] Such as figure 1 and figure 2 A WiFi security authentication method shown includes the following steps:
[0024] Step 1: hide the Beacon frame broadcast by the AP in the AP, that is, cancel the SSID option, so that the STA cannot obtain the SSID name through passive scanning;
[0025] Step 2: The AP waits for the probe request frame from the STA;
[0026] Step 3: The STA actively sends a detection request frame to the AP, and the AP makes a judgment based on the STA's MAC address and the admission mechanism: if the access is not allowed, no corresponding processing is performed on the wireless frame of the STA, and step ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com