Black box detection method and device of PHP code executing loophole
A code execution and detection method technology, applied in computer security devices, instruments, electrical digital data processing, etc., to improve work efficiency, save time for secondary vulnerability verification, and reduce the false positive rate of vulnerabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
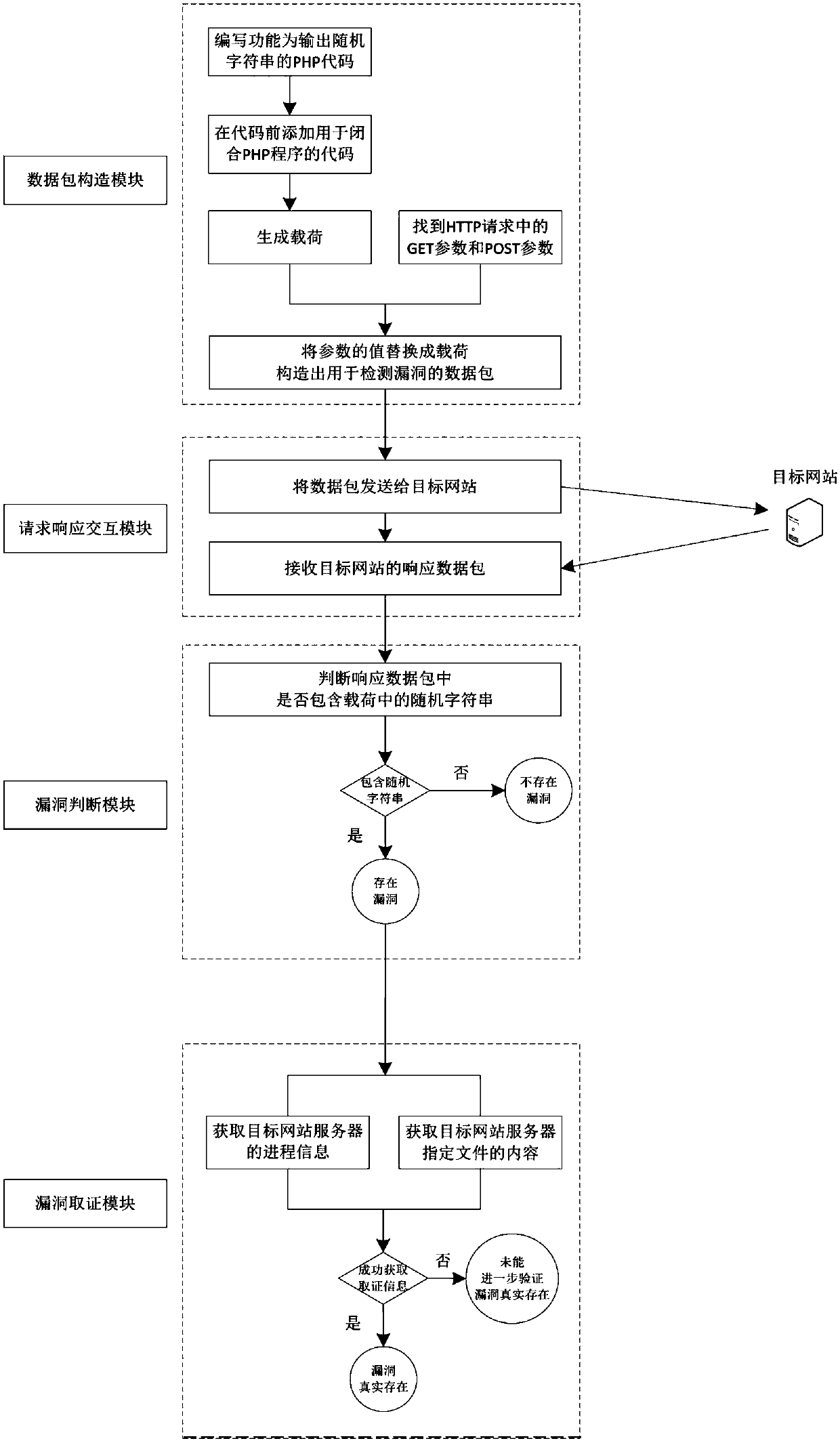
[0080] Packets used to detect vulnerabilities, such as:
[0081] http: / / 1.1.1.1 / test_1.php? data=print(c9de2ca853969fca6526811f099825691); / /
[0082] After sending to the target website, if the random string (c9de2ca853969fca6526811f099825691) exists in the received return page, it is judged that there is a PHP code execution vulnerability; if the random string does not exist, it is judged that the vulnerability does not exist.
example 2
[0084] Packets used to detect vulnerabilities, such as:
[0085] http: / / 1.1.1.1 / test_2.php? data='); print(c9de2ca853969fca6526811f099825691); / /
[0086] After sending to the target website, if the random string (c9de2ca853969fca6526811f099825691) exists in the received return page, it is judged that there is a PHP code execution vulnerability; if the random string does not exist, it is judged that the vulnerability does not exist.
example 3
[0088] Packets used to detect vulnerabilities, such as:
[0089] http: / / 1.1.1.1 / test_3.php? data="); print(c9de2ca853969fca6526811f099825691); / /
[0090] After sending to the target website, if the random string (c9de2ca853969fca6526811f099825691) exists in the received return page, it is judged that there is a PHP code execution vulnerability; if the random string does not exist, it is judged that the vulnerability does not exist.
[0091] (3) Vulnerability Forensics
[0092] (1) Obtain process information on the target website server
[0093] Generate payloads such as:
[0094] http: / / 1.1.1.1 / test_1.php? data=system('ps-ef'); / / After sending to the target website, if there is process list information in the received return page, it can be further verified that the vulnerability does exist; and the process list information is used as evidence collection information, It can be used by vulnerability detection personnel to intuitively judge and confirm the real existence of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com