Identity recognition method, electronic device and computer readable storage medium
An identity recognition and ID card technology, applied in the field of identity verification, can solve the problems of impersonating a returning visitor, the insurance formula cannot verify the customer's identity, and the customer's identity cannot be verified accurately, so as to avoid impersonation or forged identity cards.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
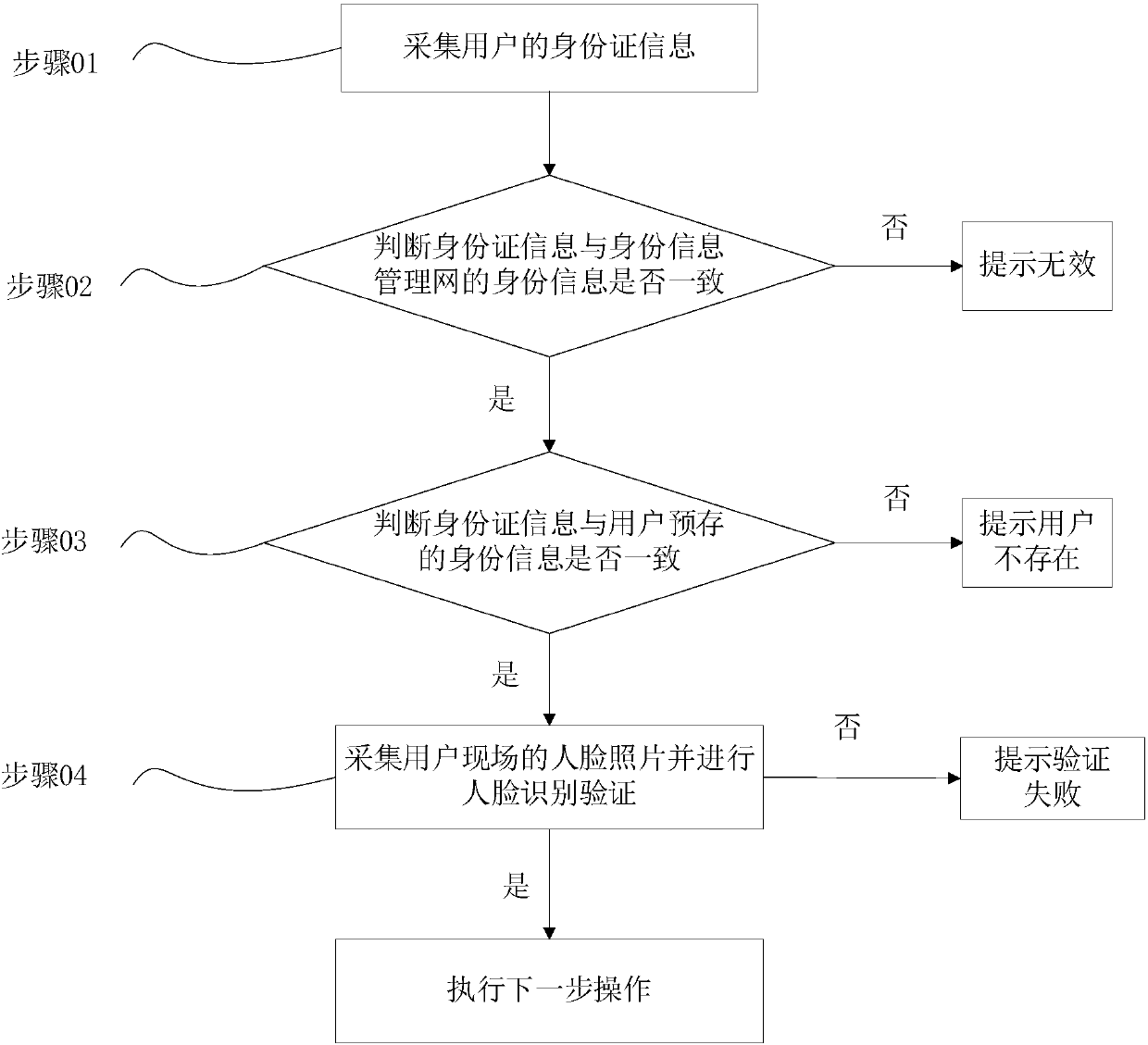
[0031] see figure 1 , the identification method of this embodiment includes the following steps:
[0032] Step 01, collect the ID card information of the user.
[0033] The ID card information includes the ID card number and the profile picture on the ID card. The verification control center sends an ID card information collection command to the information collection unit on the user end, and the information collection unit prompts the user to place the ID card in the designated area and turn on the camera on the user end to take pictures on the spot. The user's ID card photo, and collect the ID number and profile photo located in the ID card photo, the ID number and profile photo are used for matching verification with the identity information data on the identity information management network, and for pre-existing verification control center identity information for matching verification. Among them, it is preferable to identify the characteristics of the user through th...
Embodiment 2
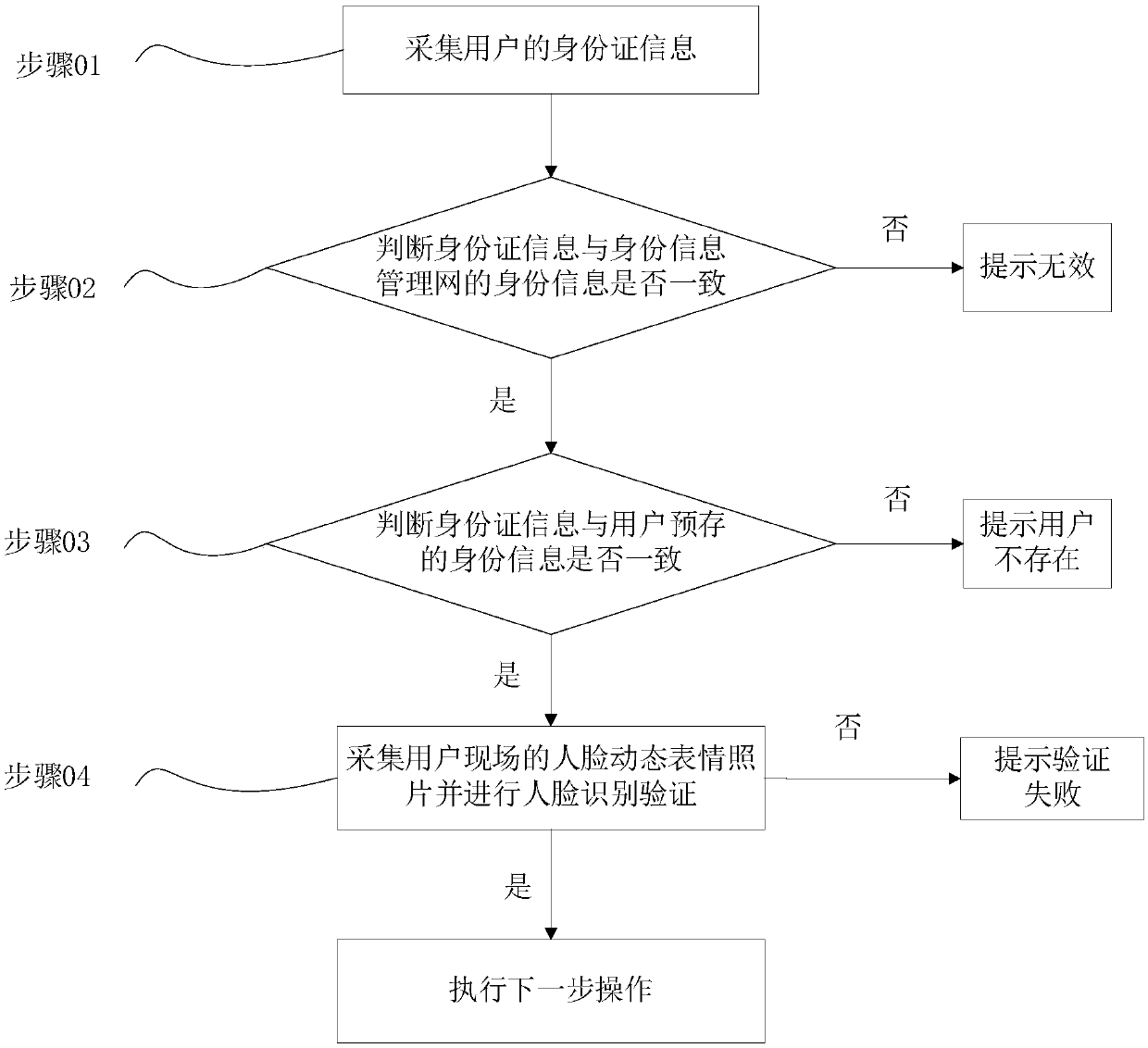
[0046] refer to figure 2 , showing a method for electronic image identification, which specifically includes the following steps:
[0047] Step 01, collect the ID card information of the user.
[0048] Step 02, determine whether the ID card information is consistent with the identity information of the identity information management network, if so, execute step 03, otherwise prompt invalid.
[0049] Step 03, judge whether the ID card information is consistent with the user's pre-stored identity information, if so, execute step 04, otherwise prompt that the user does not exist.
[0050] Step 04: Collect photos of facial dynamic expressions of the user on site and perform face recognition verification. If the verification is passed, the user is allowed to perform the next operation, and if the verification fails, it will prompt that the verification fails.
[0051] Wherein, the user makes a specified expression according to the prompt, and extracts the expression feature and...
Embodiment 3
[0053] refer to Figure 3-4 , shows an identity recognition system. In this embodiment, the identity recognition system is divided into one or more program modules, one or more program modules are stored in a storage medium, and are processed by one or more processors Executed to complete the present invention. The program module referred to in the present invention refers to a series of computer program instruction segments capable of completing specific functions, which is more suitable than the program itself to describe the execution process of the identification system in the storage medium. The following description will specifically introduce the program modules of this embodiment. Features:
[0054] The identity information collecting module 201 is used for collecting the ID card information of the user, including collecting the ID card number and avatar photo on the ID card, and is suitable for collecting the identity information of the ID card. The identity informa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com