Virtual machine behavior monitoring and locking method
A virtual machine and behavior technology, applied in the field of cloud computing, can solve the problems of insufficient integration, inflexibility, and poor use experience between third-party tools and cloud platforms, and achieve the effect of improving behavior monitoring and locking and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
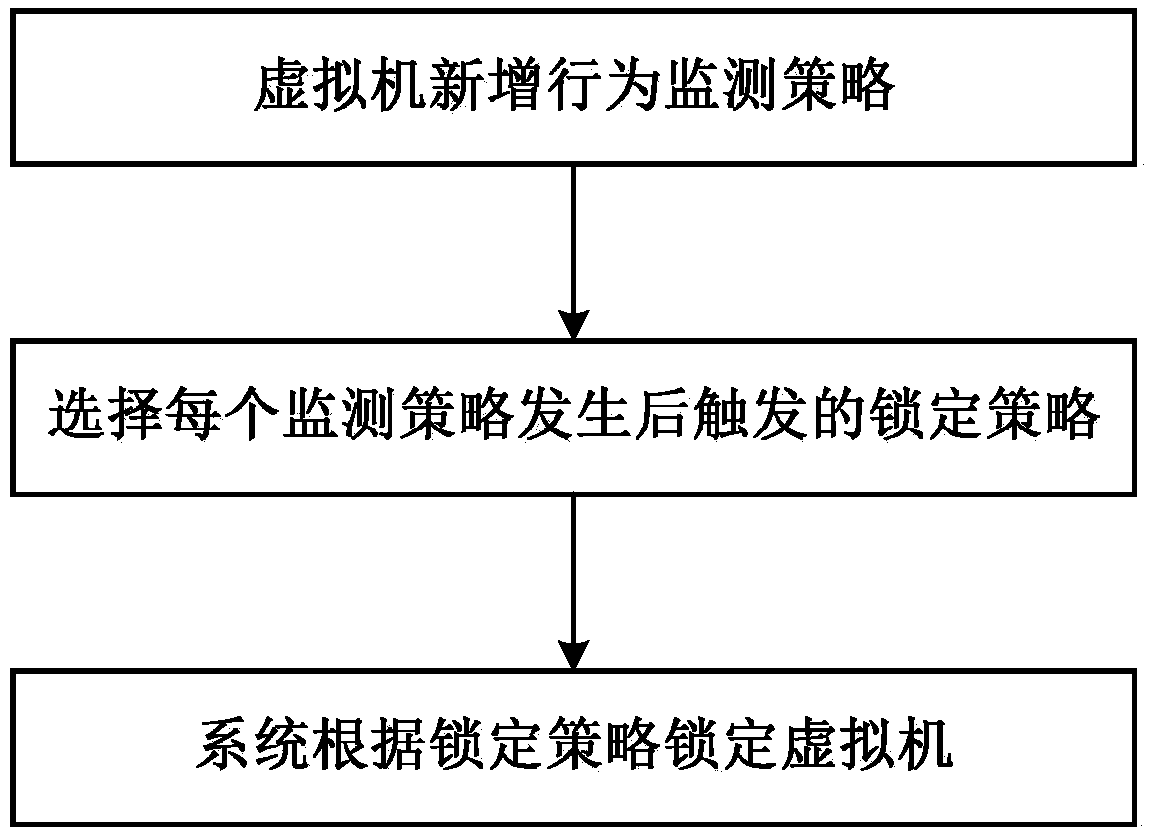
[0018] In order to make the purpose, technical scheme and advantages of the present invention clearer, the following will be further explained in detail in conjunction with the accompanying drawings and with actual implementation cases, such as figure 1 , 2 As shown, the specific implementation process is as follows:
[0019] 1. New behavior monitoring strategy for virtual machines;
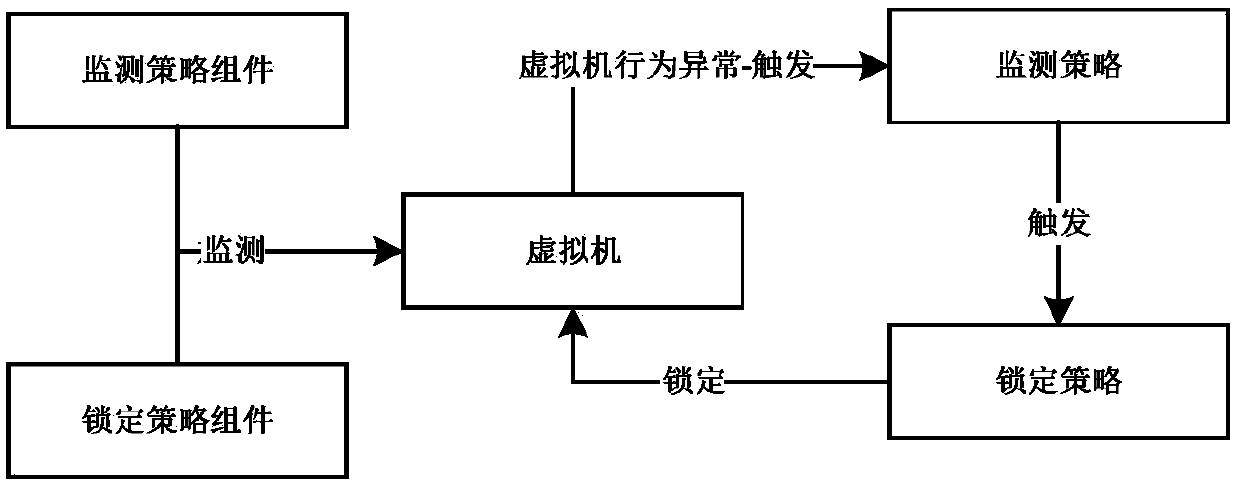
[0020] The behavior monitoring strategy refers to a strategy for monitoring the behavior of a virtual machine, such as how much the CPU utilization rate is, how much the memory utilization rate is, how much is the IO read and write, and how much is the bandwidth transmission. The policy will be monitored by the monitoring policy component.
[0021] Call the / rule / create.do method to create a monitoring policy with the following parameters:
[0022] / *
[0023] *meter_name policy name String
[0024] *meter_type policy type, CPU, memory, disk IO, bandwidth
[0025] *threshold alarm threshold...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com