Heterogeneous aggregation signcryption method in Internet of Things environment
An Internet of Things and environmental technology, applied in the field of information security, can solve the problems of inability to use secure communication, lack of aggregation verification, etc., to achieve the effect of improving execution efficiency, reducing computational overhead, and facilitating processing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
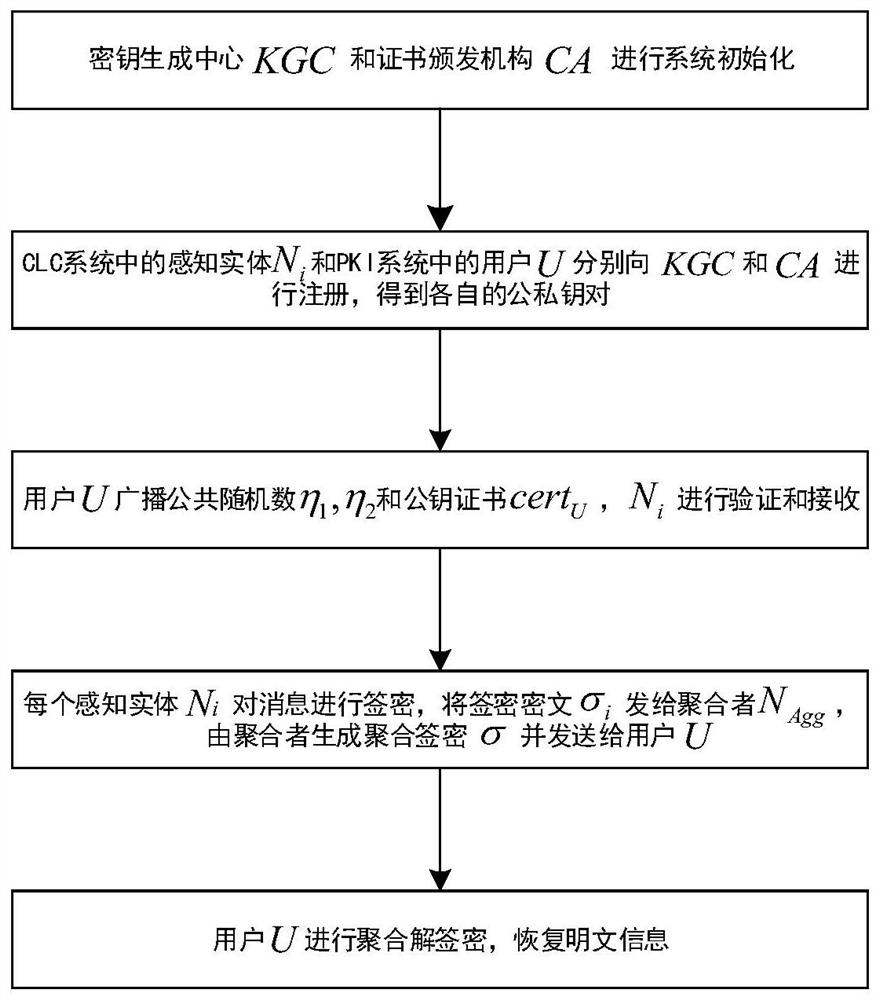
[0035] refer to figure 1 , the implementation steps of the present invention are as follows:
[0036] Step 1, system initialization.
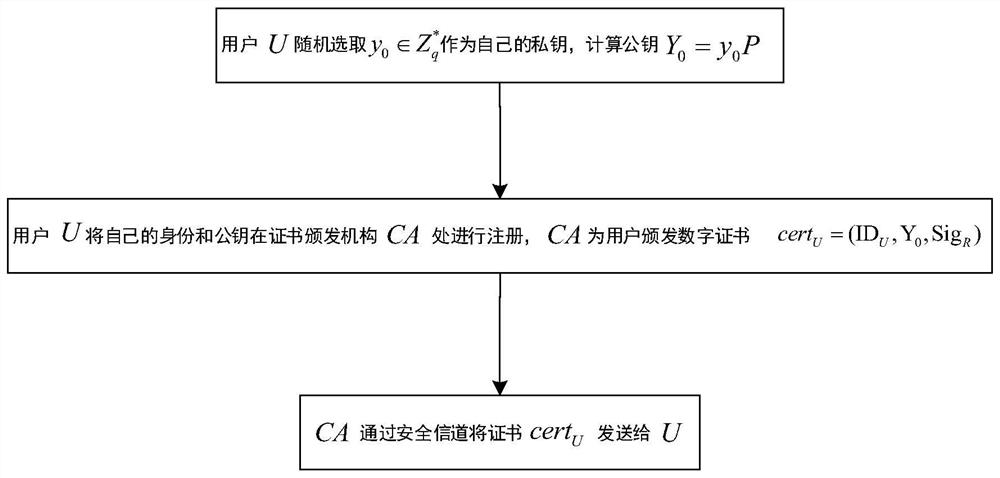
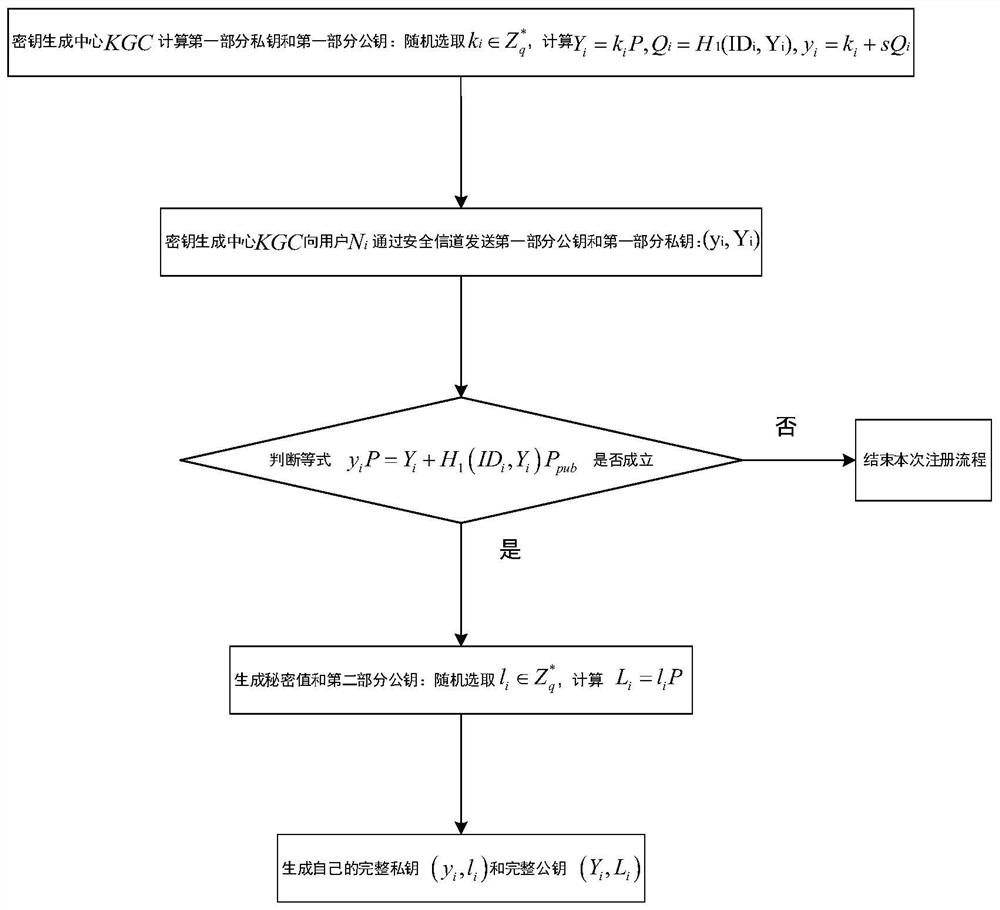
[0037] (1a) The key generation center KGC in the CLC system generates system public parameters params={q,k,E / F q ,G,P,P pub ,H 1 ,H 2 ,H 3 ,H 4}, where k is a security parameter; q is a large prime number, q>2 k ;E / F q is a prime field F q The elliptic curve on the elliptic curve; G represents the additive cyclic group composed of points on the elliptic curve; P is the generator of G; P pub is the public key of KGC; H 1 , H 2 , H 3 and H 4 are four collision-free safe hash functions, H 1 is to map 0 / 1 sequences of different lengths to Hash function in H 2 is a hash function that maps the elements in G to bits of the same length as the message to be signed encrypted, H 3 is to map 0 / 1 sequences of different lengths to Hash function in H 4 is to map 0 / 1 sequences of different lengths to Hash function in;
[0038] (1b) KGC ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com