Multi-tenant cloud computing-oriented container security monitoring method and system
A technology of security monitoring and cloud computing, which is applied in the field of cloud computing security to achieve the effect of ensuring system performance, realizing queryability and traceability, and ensuring security isolation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045]In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below through specific embodiments and accompanying drawings.
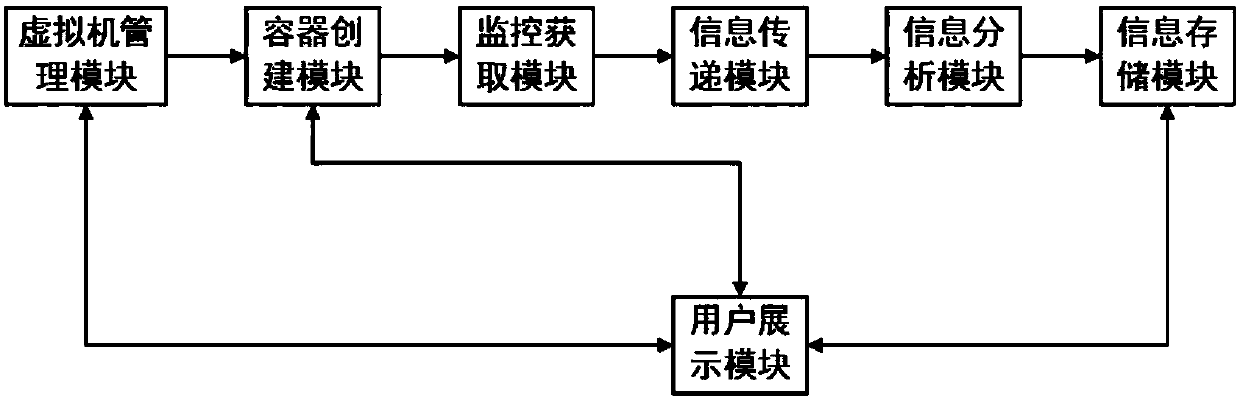
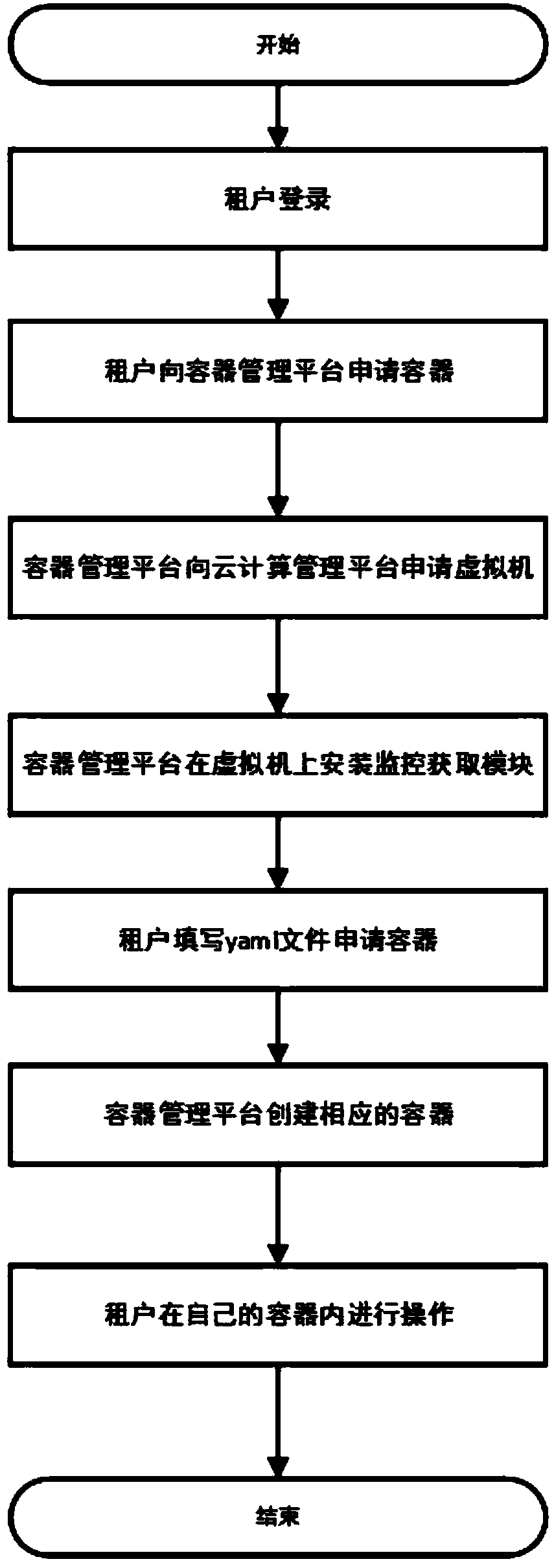
[0046] Container (Container) technology is an operating system-level lightweight virtualization technology. Its principle is to isolate based on Linux kernel technology. A process in a container cannot perceive the behavior of other containers and hosts, and is relatively independent and safe. operating environment. This embodiment describes a container monitoring system for multi-tenant cloud computing by using Docker as a container engine on a Linux system as an example.
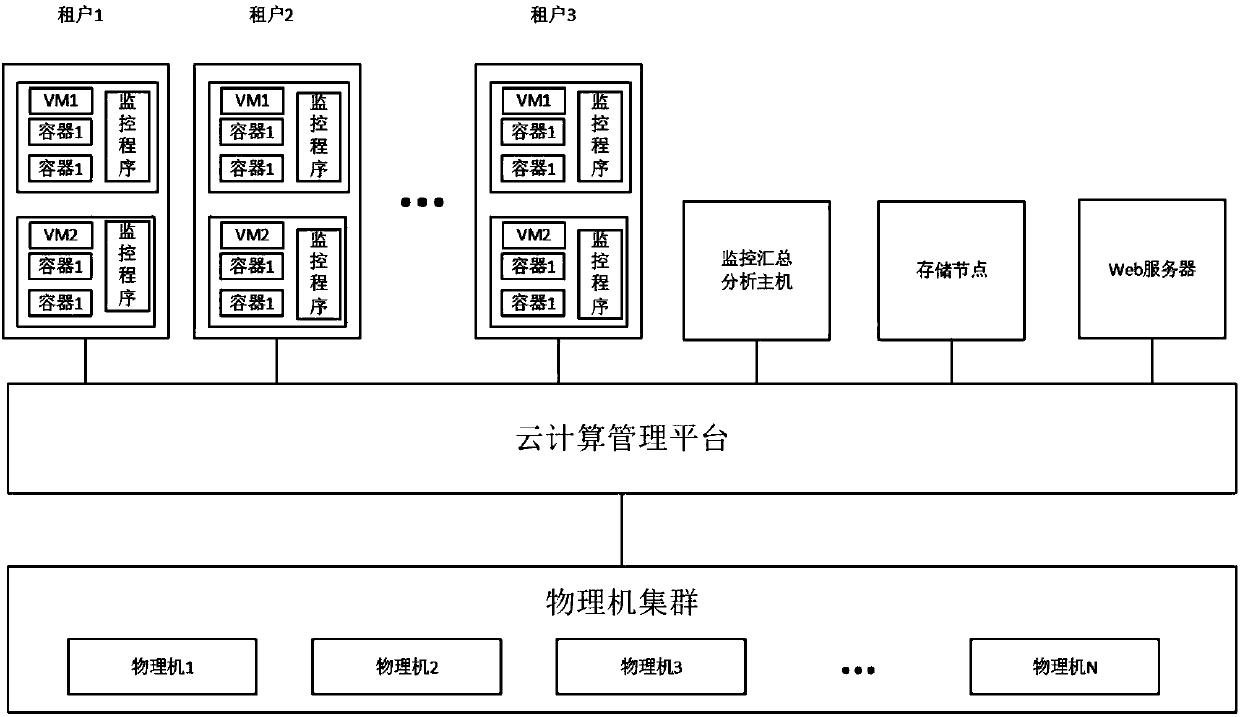
[0047] figure 1 Shown is a typical system architecture diagram of the container monitoring system provided in this embodiment. The hardware layer of the system is a physical machine cluster composed of multiple physical machines, which is managed uniformly by using a cloud c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com