User privacy protection method based on secure smart contract k-anonymity incentive mechanism
A technology of smart contracts and incentive mechanisms, applied in the field of safe privacy protection, can solve problems such as potential safety hazards, the absence of a trusted third party, and failure of the incentive mechanism to operate normally, and achieve the effect of avoiding potential safety hazards
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
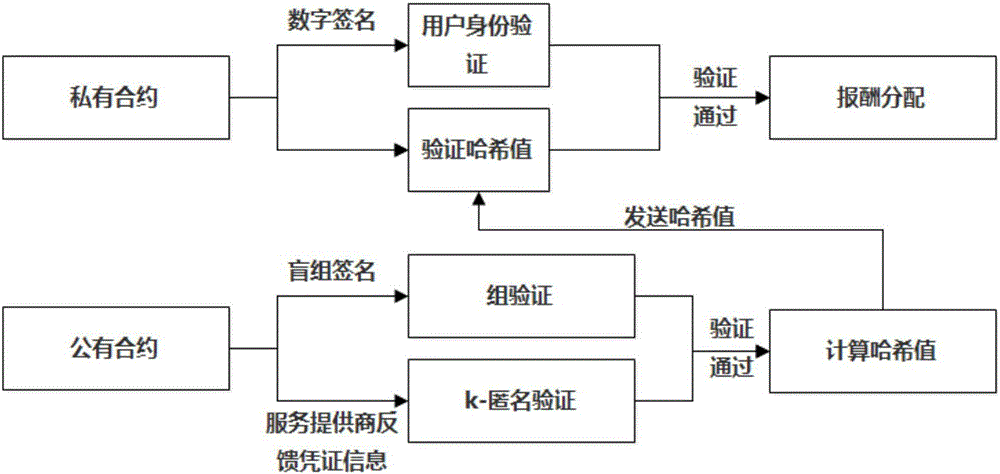
[0022] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
[0023] The execution flow of the incentive mechanism in this embodiment is as follows: figure 1 As shown, the following steps are included, wherein the buyer and the seller represent the buyer's client device and the seller's client device respectively:
[0024] (1) The buyer and the seller construct a smart contract after negotiating, and the buyer gives a bid b to realize k-anonymity i , the seller offers an asking price a for assisting in achieving k-anonymity j , record the buyer information and its bidding price in the smart contract in the order of decreasing bidding price, and record the seller information and its asking price in the smart contract in the order of increasing asking price.
[0025] (2) Buyers and sellers conduct an auction game, and select the winning buyers and sellers according to the following screening conditions:
[002...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com