Malicious order identification method and device and electronic device
An order and malicious technology, applied in the network field, can solve the problems of low recognition success rate and narrow recognition range, and achieve the effect of increasing the success rate and expanding the scope
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] The technical solutions in the embodiments of the present invention will be described below with reference to the drawings in the embodiments of the present invention.
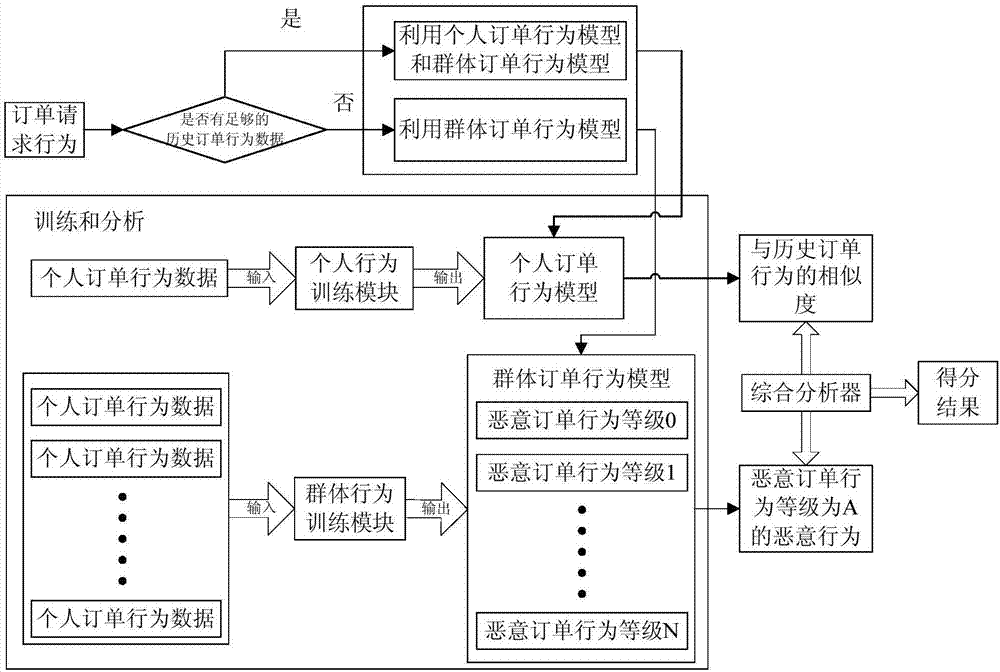
[0056] In the prior art, the identification of malicious orders often adopts targeted identification in each link. For example, there is a method of identifying the IP address accessed by the order. When it is detected that the number of orders from the same IP address increases sharply within a period of time, These orders can be determined as malicious orders, or these orders can be determined as suspicious orders and further identified. However, when a malicious user uses malicious means to make the access IP address of each malicious order different, the above method cannot identify these malicious orders, which shows that the identification success rate of the existing methods is low.
[0057] Based on this, the inventor believes that the user's historical order behavior includes the user's order h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com