Data encryption transmission method and device
A data encryption and transmission method technology, applied in digital transmission systems, transmission systems, secure communication devices, etc., can solve problems such as weak data security and reliability, achieve fruitful results, mature research and development levels, and improve security and reliability sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
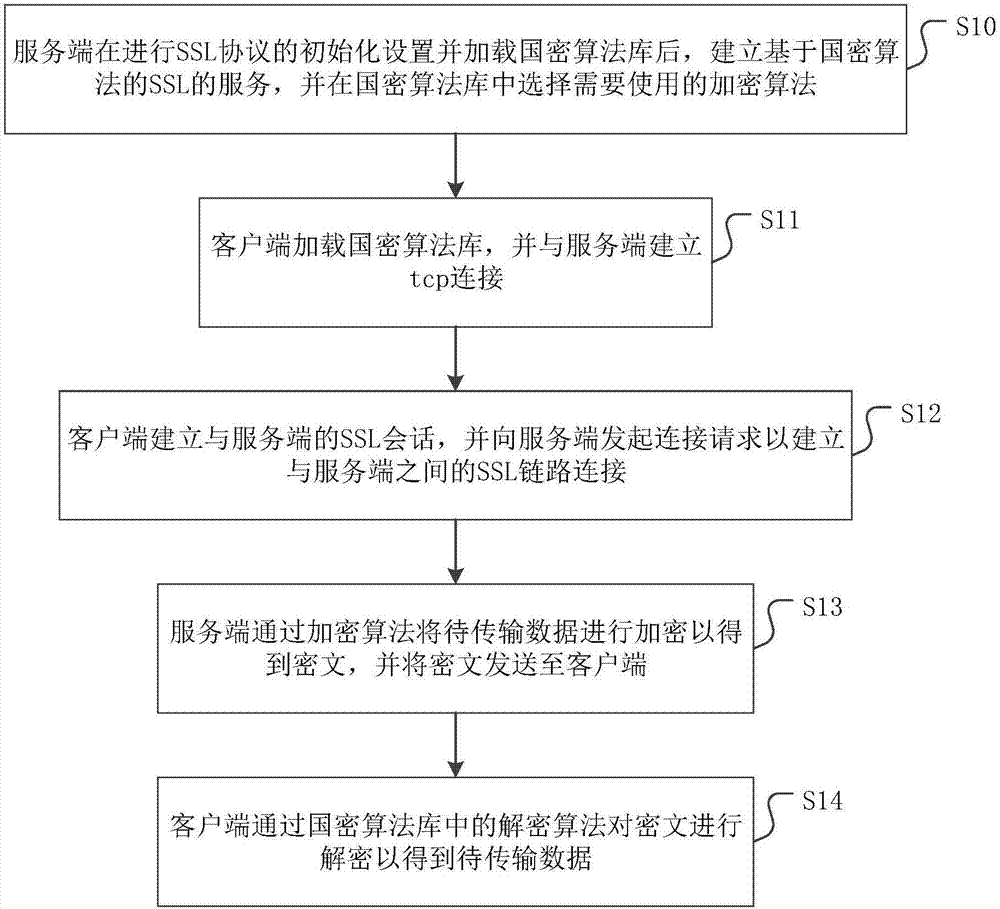
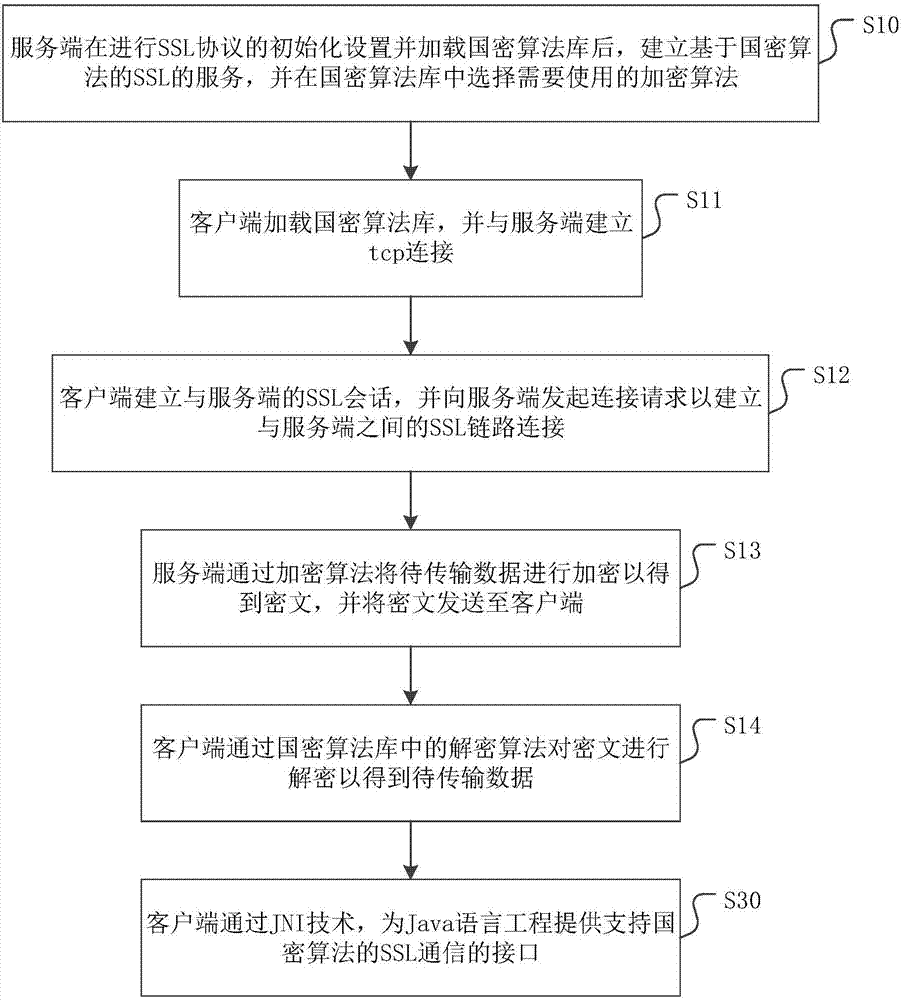
[0033] figure 1 It is a flow chart of a data encryption transmission method provided in this embodiment. Please refer to figure 1 , the data encryption transmission method is applied to the communication process based on the SSL protocol, and the specific steps include:
[0034] Step S10: After initializing the SSL protocol and loading the national secret algorithm library, the server establishes an SSL service based on the national secret algorithm, and selects the encryption algorithm to be used in the national secret algorithm library.
[0035] In this step, the server initializes the SSL protocol to configure various parameters of the SSL protocol to ensure that the SSL protocol can run normally on the server and prepare for subsequent SSL protocol transmission. The purpose of loading the national secret algorithm library is to provide sufficient encryption algorithm support for the SSL protocol, so that the SSL protocol can specifically select the required national secr...
Embodiment approach
[0036] As a preferred implementation manner, the national secret algorithm library is specifically the GmSSL national secret algorithm library.
[0037] Since the GmSSL national secret algorithm library is the result of high investment and research efforts in the scientific research field on the national secret algorithm, there are fewer loopholes and it is more secure.
[0038] Correspondingly, as a preferred implementation manner, in step S11, the client loads the national secret algorithm library specifically as follows:
[0039] The client loads the GmSSL national encryption algorithm library through the GmSSL program.
[0040] GmSSL, as an open source program that integrates the national secret algorithm library and corresponding command line tools, can realize a series of matters such as encryption and transmission of transmitted data between the client and the server on different system platforms. Although the current GmSSL program generally runs on the Linux system pl...
Embodiment 2
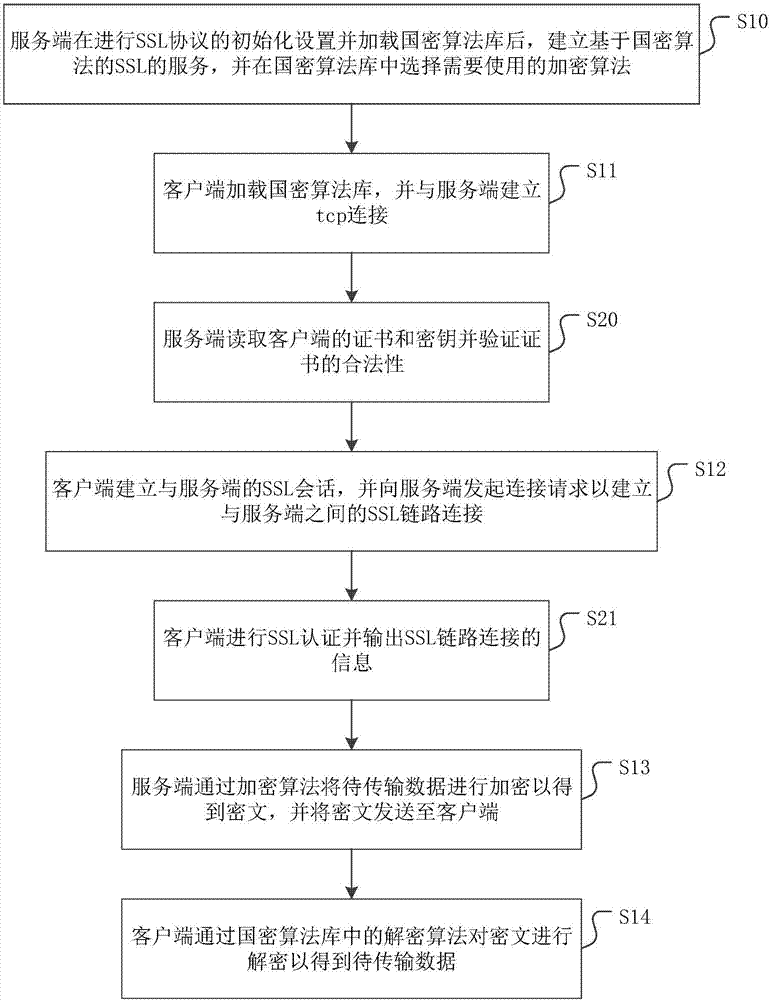
[0053] figure 2 It is a flow chart of another data encryption transmission method provided by the embodiment of the present invention. figure 2 In steps S10-S14 and figure 1 Same, no more details here.
[0054] Such as figure 2 As shown, as a preferred implementation, after the client loads the national secret algorithm library and establishes a tcp connection with the server, that is, after step S11, it also includes:
[0055] Step S20: the server reads the client's certificate and key and verifies the validity of the certificate.
[0056] In this step, the server uses the certificate and key provided by the client to determine whether the client is a legal user that can communicate with itself. It can be understood that, before the data is transmitted from the server to the client, verifying the legality of the identity of the client can further ensure the security of the communication transmission data.
[0057] Such as figure 2 As shown, as a preferred embodiment...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com