Network security protection method and device and electronic device
A technology of network security and terminal equipment, applied in the field of network security, can solve problems such as insufficient security defense performance of the Internet of Things to meet actual needs, damage to the perceived data security of the Internet of Things, and damage to the Internet of Things
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
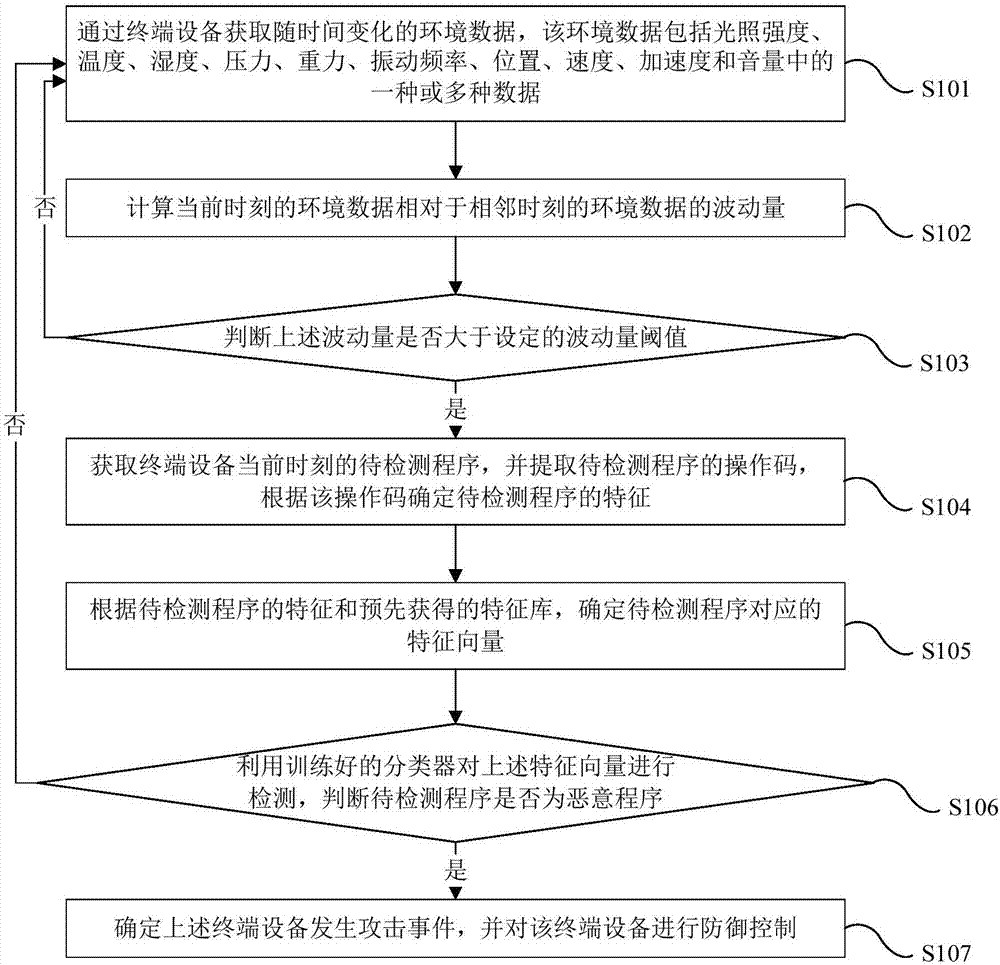
[0063] figure 1 A schematic flow diagram of the network security defense method provided by the embodiment of the present invention, such as figure 1 As shown, the method includes the following steps:
[0064] In step S101, the terminal device acquires environmental data that changes over time, and the environmental data includes one or more of light intensity, temperature, humidity, pressure, gravity, vibration frequency, position, speed, acceleration, and volume.
[0065] The perception layer of the Internet of Things is equipped with environmental data collection nodes for collecting environmental data. The terminal device is set at the perception layer of the Internet of Things, and the collected environmental data is transmitted to the Internet of Things through the setting of the terminal device. For example, the perception layer of the Internet of Things is equipped with multiple sensor acquisition boards, and the sensor acquisition boards are equipped with sensors. ...
Embodiment 2
[0107] Figure 5 A schematic diagram of the module composition of the network security defense device provided by the embodiment of the present invention, such as Figure 5 As shown, the device includes:
[0108] The data acquisition module 51 is configured to acquire environmental data that changes over time through the terminal device, wherein the environmental data includes one or more of light intensity, temperature, humidity, pressure, gravity, vibration frequency, position, speed, acceleration, and volume kinds of data;
[0109] Calculation and judgment module 52, used to calculate the fluctuation amount of the environmental data at the current moment relative to the environmental data at adjacent moments, and judge whether the fluctuation amount is greater than the set fluctuation amount threshold;
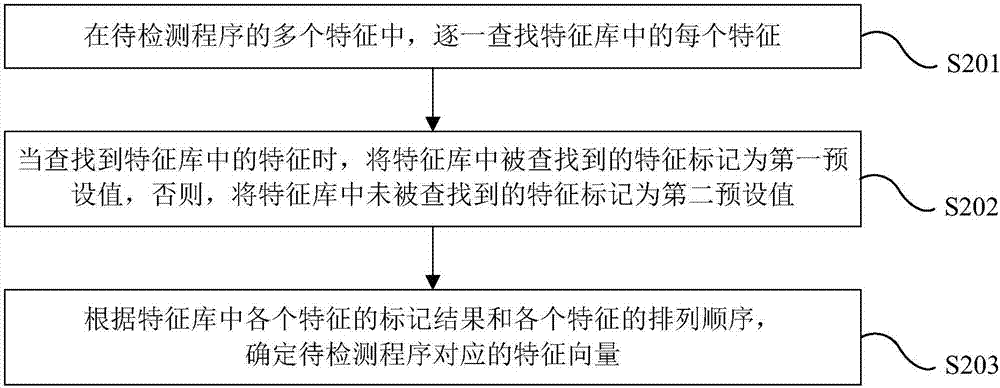
[0110] The feature extraction module 53 is used to obtain the program to be detected at the current moment of the terminal device when the judgment result of the calculat...
Embodiment 3
[0124] see Figure 6 , the embodiment of the present invention also provides an electronic device 100, including: a processor 40, a memory 41, a bus 42 and a communication interface 43, the processor 40, the communication interface 43 and the memory 41 are connected through the bus 42; Executable modules, such as computer programs, stored in the execution memory 41 .
[0125] Wherein, the memory 41 may include a high-speed random access memory (RAM, Random Access Memory), and may also include a non-volatile memory (non-volatile memory), such as at least one disk memory. The communication connection between the system network element and at least one other network element is realized through at least one communication interface 43 (which may be wired or wireless), and the Internet, wide area network, local network, metropolitan area network, etc. can be used.
[0126] The bus 42 may be an ISA bus, a PCI bus or an EISA bus, etc. The bus can be divided into address bus, data bu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com