SDN layer-2 forwarding method and system
A two-layer forwarding and forwarding table technology, applied in the field of computer networks, can solve the problems of overloading the controller, consuming storage resources, affecting the performance of table lookup, etc., and achieves the effect of reducing difficulty and workload, reducing storage space, and reducing scale
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
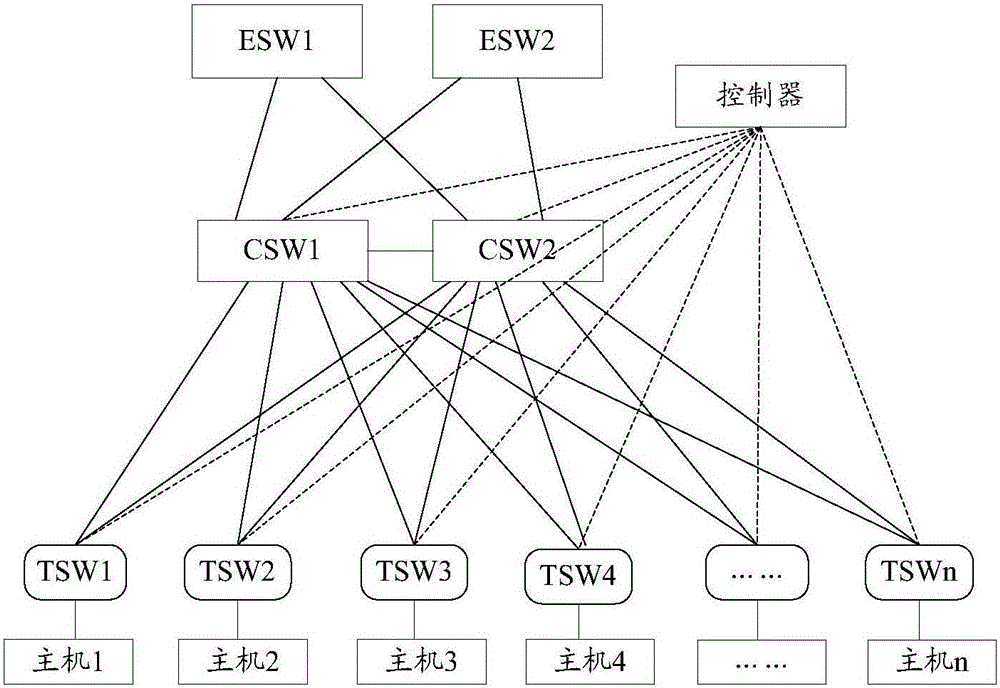
[0073]In the communication scenario of hosts on the same network segment belonging to different WAs, before sending a Layer 3 packet, the host first checks whether it has the MAC address of the destination IP. If not, the host first sends an ARP request, and the IP address requested by the ARP message is the IP address of the destination host, and is sent to the controller on the TSW. The controller generates a globally unique Proxy MAC and sends an ARP proxy to the requesting host. The controller learns the IP address and MAC address of the host requesting ARP, calculates the path according to the SPF, sends the Layer 2 forwarding table to all switches in the path, and sends the host routing table to all CSW controllers in the path. At the same time, the controller will check whether there is an entry record of the MAC address of the ARP Request, if not, the controller will send an ARP broadcast message, and the ARP request will be broadcast on all the trunk ports of the TSW....
example 2
[0091] In instance 1, Proxy MAC is the only proxy MAC in the network topology. When the CSW queries the host routing table, it queries the host MAC address corresponding to the destination IP in the entire network host routing table. The breadth of the query is to maximize the range of queries in the host routing table. When the number of host routing tables increases sharply, the query range and difficulty also increase proportionally. Considering the two-layer optimization that reduces complexity and improves performance, Example 2 proposes a Proxy MAC that uniquely identifies a switch based on different TSWs, and the host connected to the TSW is associated with the Proxy MAC of the TSW to which it belongs. Hosts under different TSW switches use Proxy MAC, the unique identifier of the TSW to which the target host belongs. When the CSW receives the Layer 3 data packet, it can query the host routing table according to the Proxy MAC corresponding to the TSW. Precisely narrow...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com