Operation execution method, springboard machine, cluster authentication server and bastion machine system
A technology for authenticating servers and operating execution, which is applied in the field of computer networks, can solve problems such as low security, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
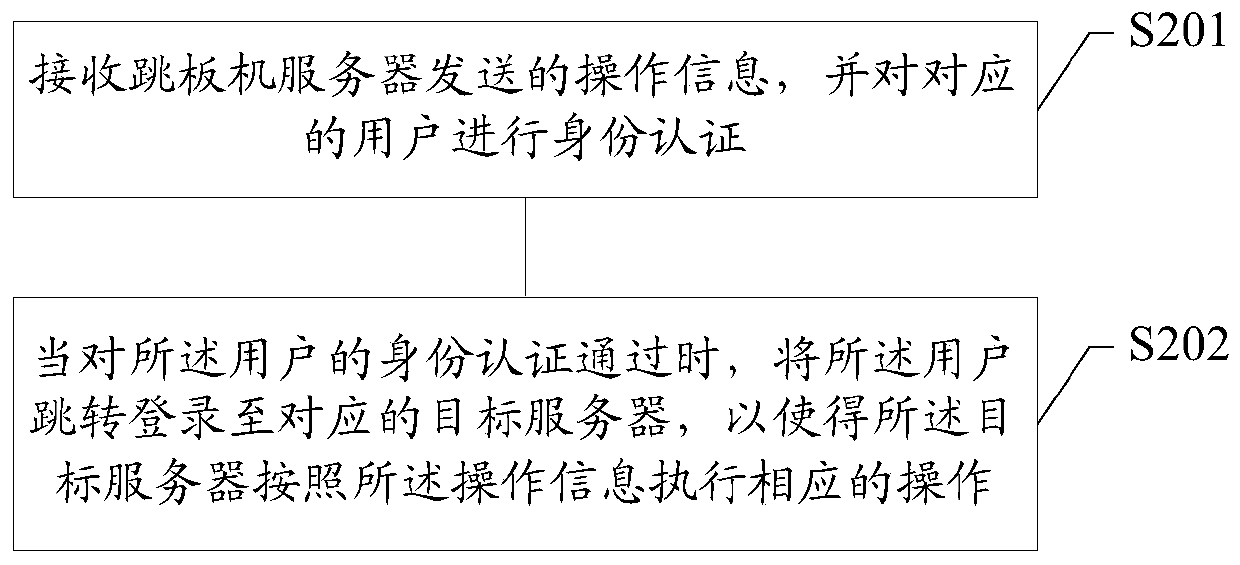
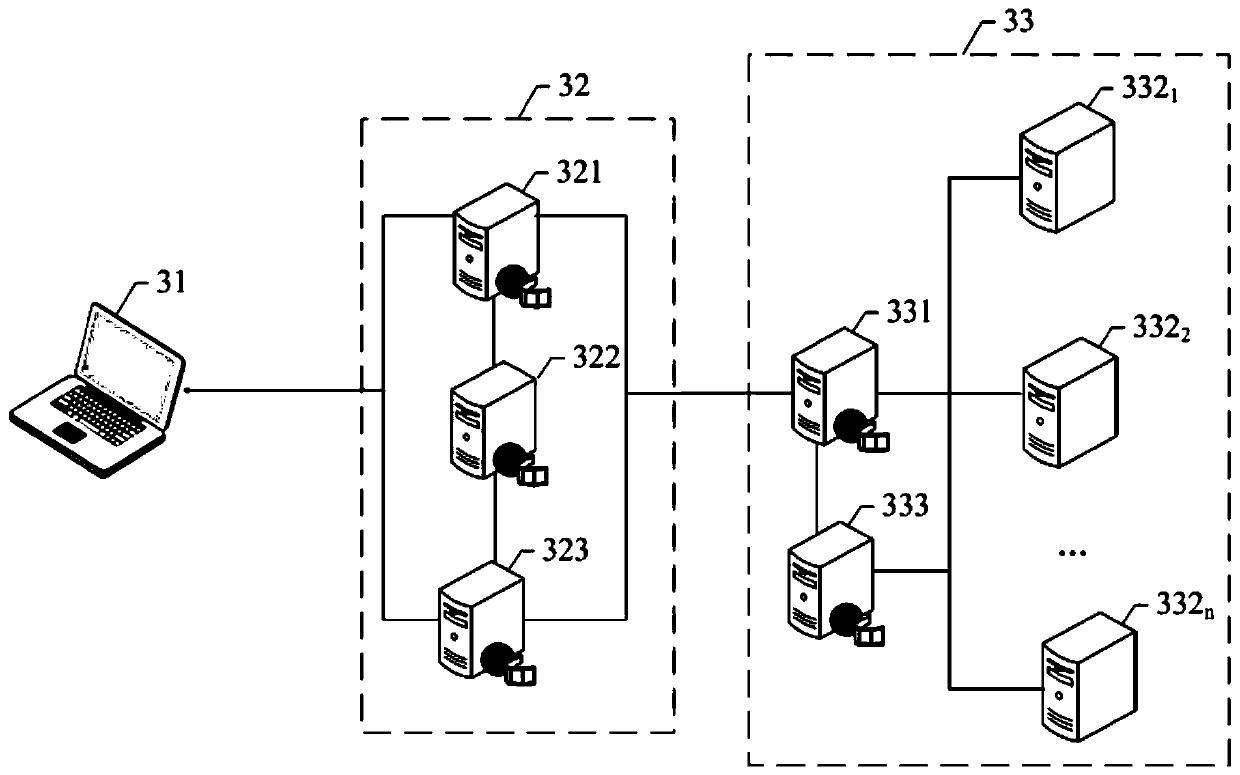
[0047] As stated in the background technology, the bastion host system in the prior art includes a springboard machine and a server cluster. The bastion host system does not allow users to directly log in to the servers in the server cluster for operation. In order to operate on the servers in the server cluster.
[0048] Among them, when the user logs in to the springboard machine, he inputs the corresponding user name and password information, and the springboard machine authenticates the user based on the user name and password entered by the user; when the user's identity verification passes, the user can perform the corresponding operation The instruction is sent to the springboard machine, and then the springboard machine forwards the user's operation instruction to the target server in the server cluster, so that the target server performs the corresponding operation.
[0049] It can be seen from the description that the above scheme only uses a fixed username and passw...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com