A security rule configuration method without ip firewall
A configuration method and firewall technology, applied in transmission systems, electrical components, etc., can solve problems such as changing the topology of the control network, difficulty in implementing firewall management configuration, installation and management defects, etc., to achieve clear processes, good real-time performance, and flow processing little effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
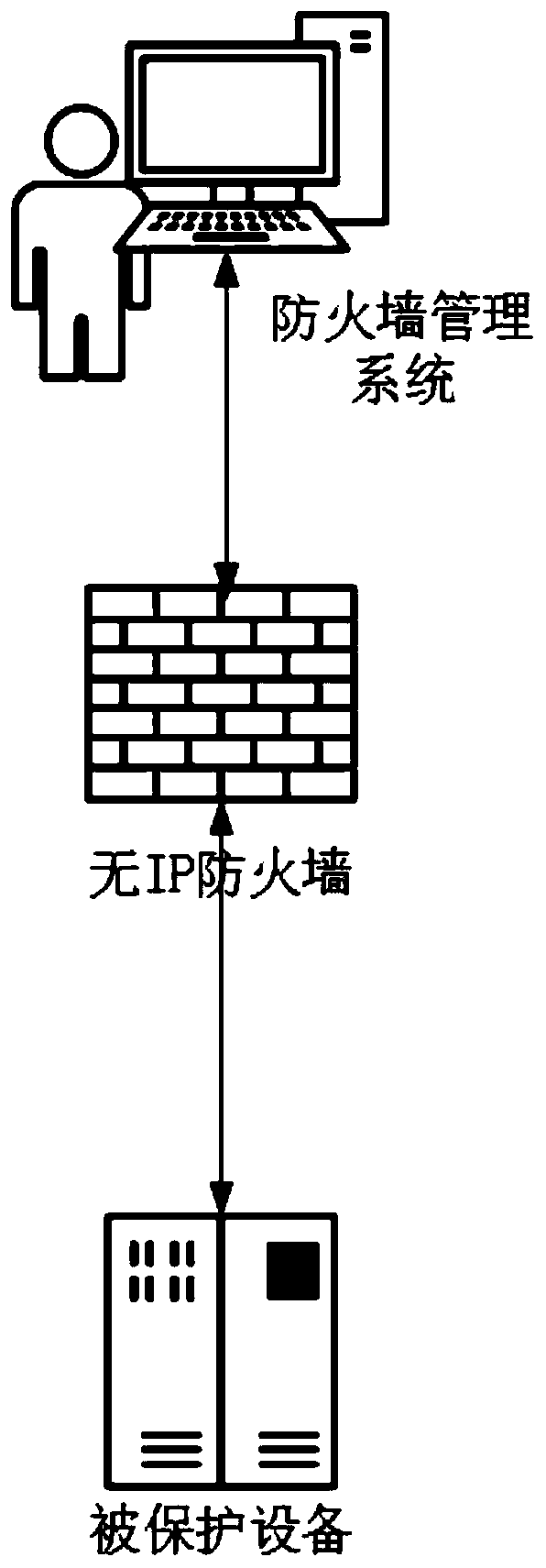
[0045] figure 1 It is a schematic diagram of deployment without IP firewall.
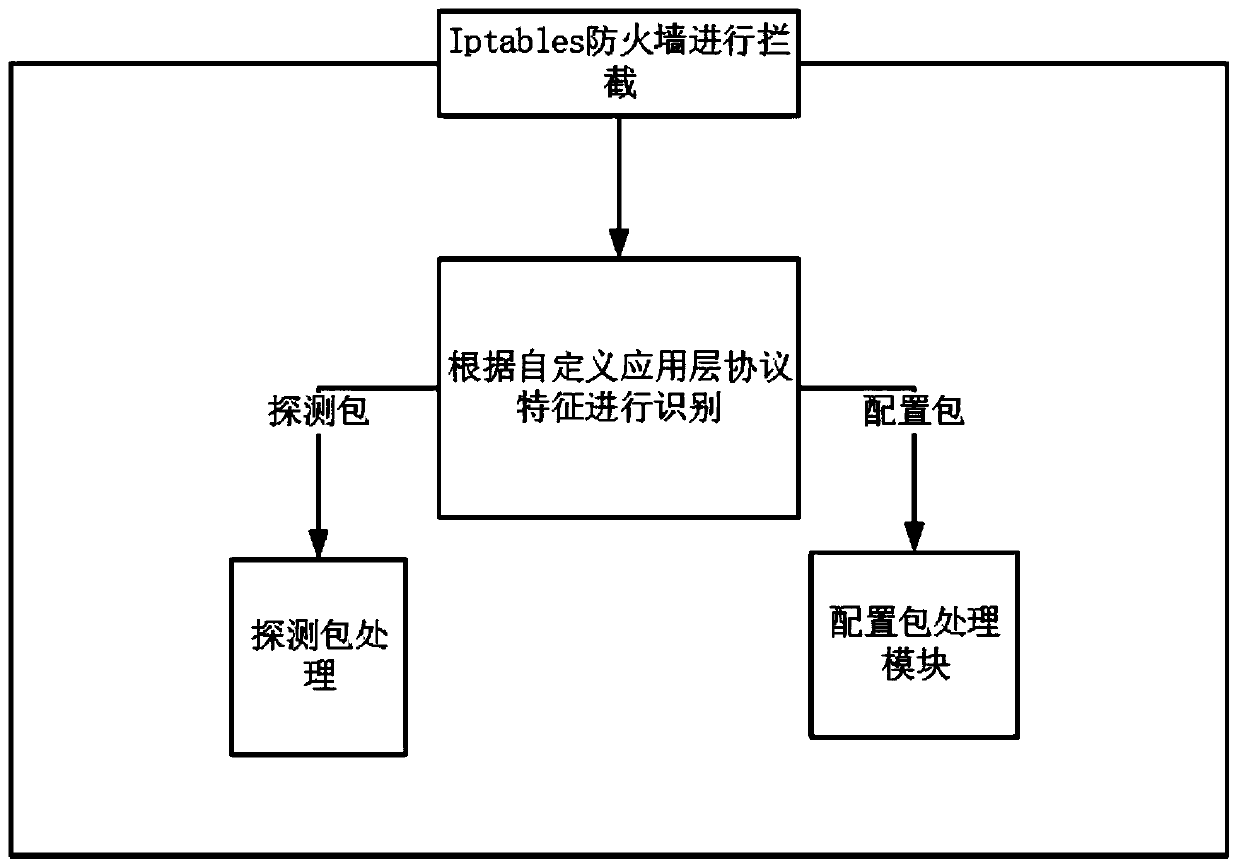
[0046] In this embodiment, a brand-new industrial firewall management and security rule configuration method is provided. All industrial firewalls no longer have IP addresses. The processing, non-IP communication module and the firewall management configuration system cooperate with each other to form a complete set of security rule configuration methods based on the non-IP industrial firewall.
[0047] Such as figure 1 As shown, when deploying a non-IP firewall, the non-IP firewall should be set between the industrial network and the protected device, and there must be a non-IP industrial firewall upstream of the protected device, because the firewall is in a non-IP mode, and the firewall management system cannot Send data packets directly to it. The firewall management system sends data packets with the IP address of the protected device as the destination address. At this time, it must pass thr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com