Quantum cellular neural network based video chaotic encryption method
A neural network, chaotic encryption technology, applied in biological neural network models, secure communication through chaotic signals, neural architecture, etc. Space, huge anti-attack performance, high encryption efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
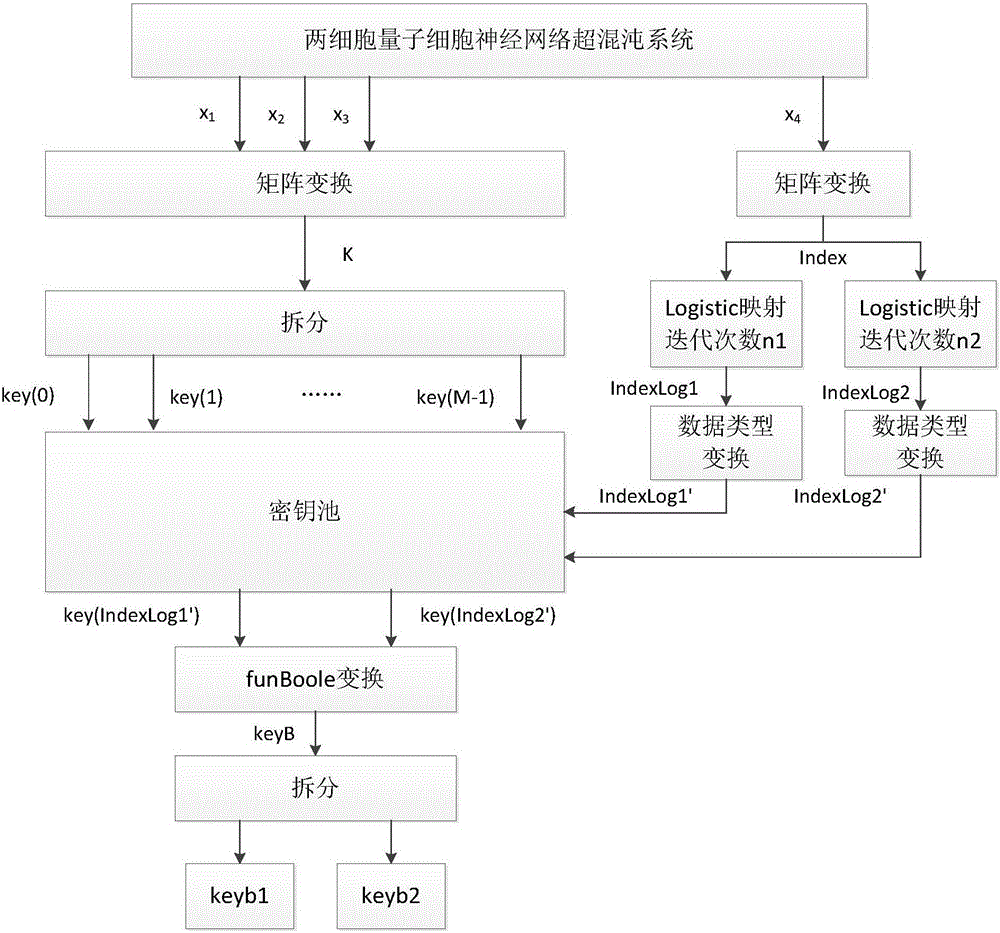
[0023] Specific implementation mode 1. Combination Figure 1 to Figure 6 Describe this embodiment, the video chaos encryption method based on quantum cellular neural network, figure 1 It is a schematic diagram of the key generation of the encryption method in this embodiment, and the key generation process is described in the following steps A1 to F1.
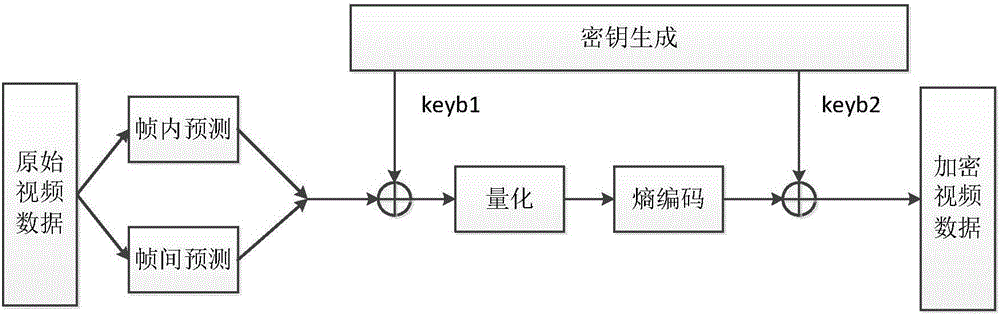
[0024] According to the H.264 video encoding standard, the encryption process of the video encryption method of the present invention is as follows: figure 2 As shown, the specific implementation details of the key generation module are as follows figure 1 , which is realized by step A1 to step F1.
[0025] A1. Take a two-cell quantum cellular neural network hyperchaotic system, and its state equation is:
[0026]
[0027] where x 1 ,x 2 ,x 3 ,x 4 is the state variable; ω 1 , ω 3 Proportional to the energy between quantum dots in each cell, ω 2 , ω 4 Represents the weighted influence of the difference in polariza...
specific Embodiment approach 2
[0074] Specific embodiment two, combine figure 2 , Figure 5 and Figure 6 This embodiment is described. This embodiment is another embodiment of the first embodiment: the key generation process and the encryption process in the embodiment are the same as those in the first embodiment.
[0075] combine Figure 5 To illustrate this embodiment, select the "person" video data in cif format with a size of 352*288. This embodiment operates under the JM8.6 basic mode of H.264, the video length is 30 frames, and the I frame interval is 8, where extract Figure 5 The 20th frame of the original image.
[0076] Figure 6 It is the ciphertext image of the 20th frame image of the "person" video data in this embodiment encrypted by the video encryption method of the present invention.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com