Account risk identification method and device
A risk identification and account technology, applied in the field of information security, can solve the problem of low accuracy of account risk identification scheme, and achieve the effect of improving accuracy and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
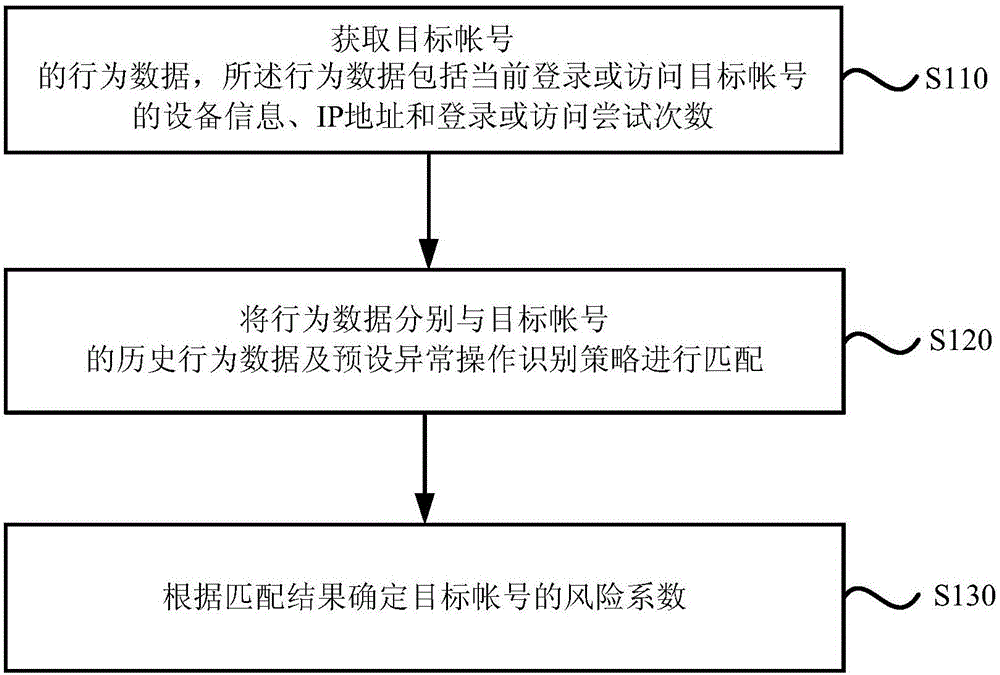
[0021] figure 1 It is a schematic flowchart of an account risk identification method provided in the first embodiment of the present invention. The method in this embodiment can be executed by an account risk identification device, where the device can be implemented by software and / or hardware. Such as figure 1 As shown, the account risk identification method provided in this embodiment specifically includes the following steps:
[0022] Step 110: Obtain behavioral data of the target account, where the behavioral data includes the device information of the current login or access to the target account, the IP address, and the number of login or access attempts.
[0023] Among them, the target account is an account that has completed user registration that can be monitored by a back-end server for a certain application or a certain web page, such as a QQ account, a WeChat account, a forum account, and a shopping website account.
[0024] When the background server detects that the t...
Embodiment 2
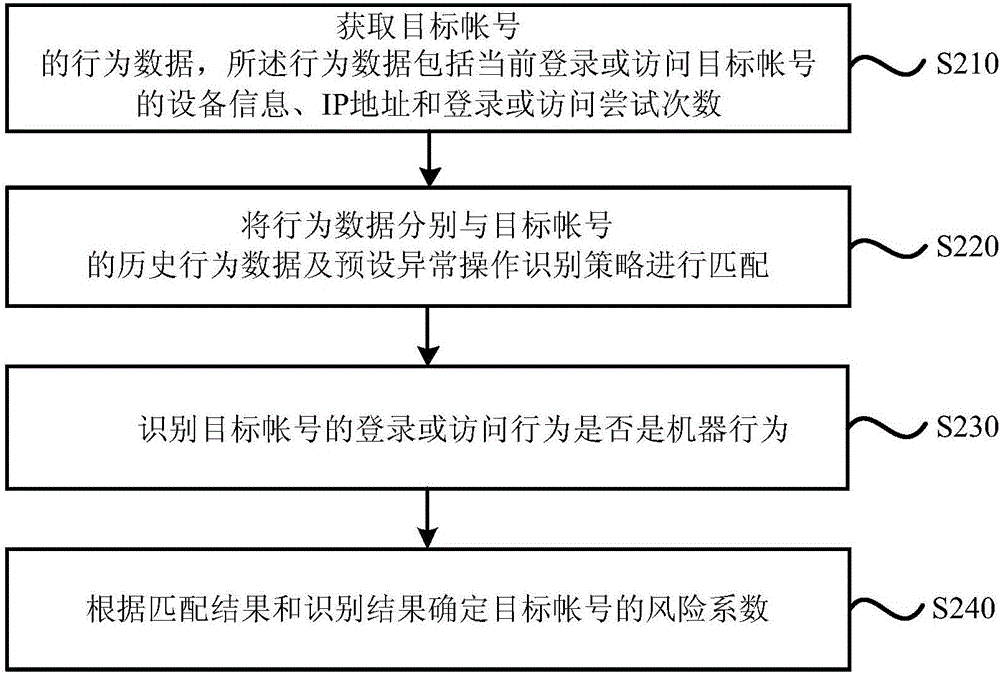
[0041] figure 2 It is a schematic flowchart of an account risk identification method provided in the second embodiment of the present invention. This embodiment refines the step of "determine the risk coefficient of the target account based on the matching result" in the foregoing embodiment. reference figure 2 , The embodiment of the present invention specifically includes the following steps:
[0042] Step 210: Obtain behavioral data of the target account, where the behavioral data includes the device information of the current login or access to the target account, the IP address and the number of login or access attempts.
[0043] Step 220: Match the behavior data with the historical behavior data of the target account and the preset abnormal operation identification strategy respectively.
[0044] Step 230: Identify whether the login or access behavior of the target account is a machine behavior.
[0045] Exemplarily, the machine behavior is different from the user's normal be...
Embodiment 3
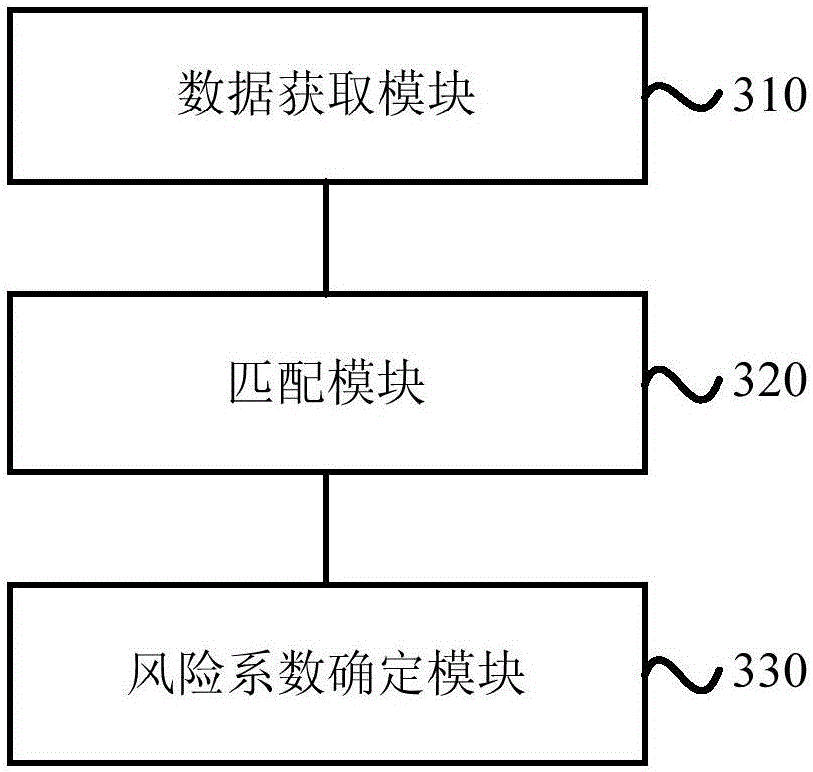
[0052] image 3 It is a structural block diagram of an account risk identification device provided in the third embodiment of the present invention. The device can be implemented by software and / or hardware, and is generally integrated in a background server. Such as image 3 As shown, the device includes: a data acquisition module 310, a matching module 320, and a risk factor determination module 330.
[0053] Wherein, the data acquisition module 310 is used to acquire the behavior data of the target account. The behavior data includes the device information, IP address, and the number of login or access attempts that are currently logged in or access the target account; the matching module 320 is used to compare all The behavior data is matched with the historical behavior data of the target account and the preset abnormal operation identification strategy; the risk coefficient determination module 330 is configured to determine the risk coefficient of the target account accor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com