A method and device for is-is protocol cross-level path calculation
A technology of hierarchical path and path calculation request, which is applied in the direction of digital transmission system, data exchange network, electrical components, etc., can solve the problems of high labor cost for configuration and maintenance, error-prone human configuration, and insufficient selection of human configuration, etc., to achieve reduction The effect of staffing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
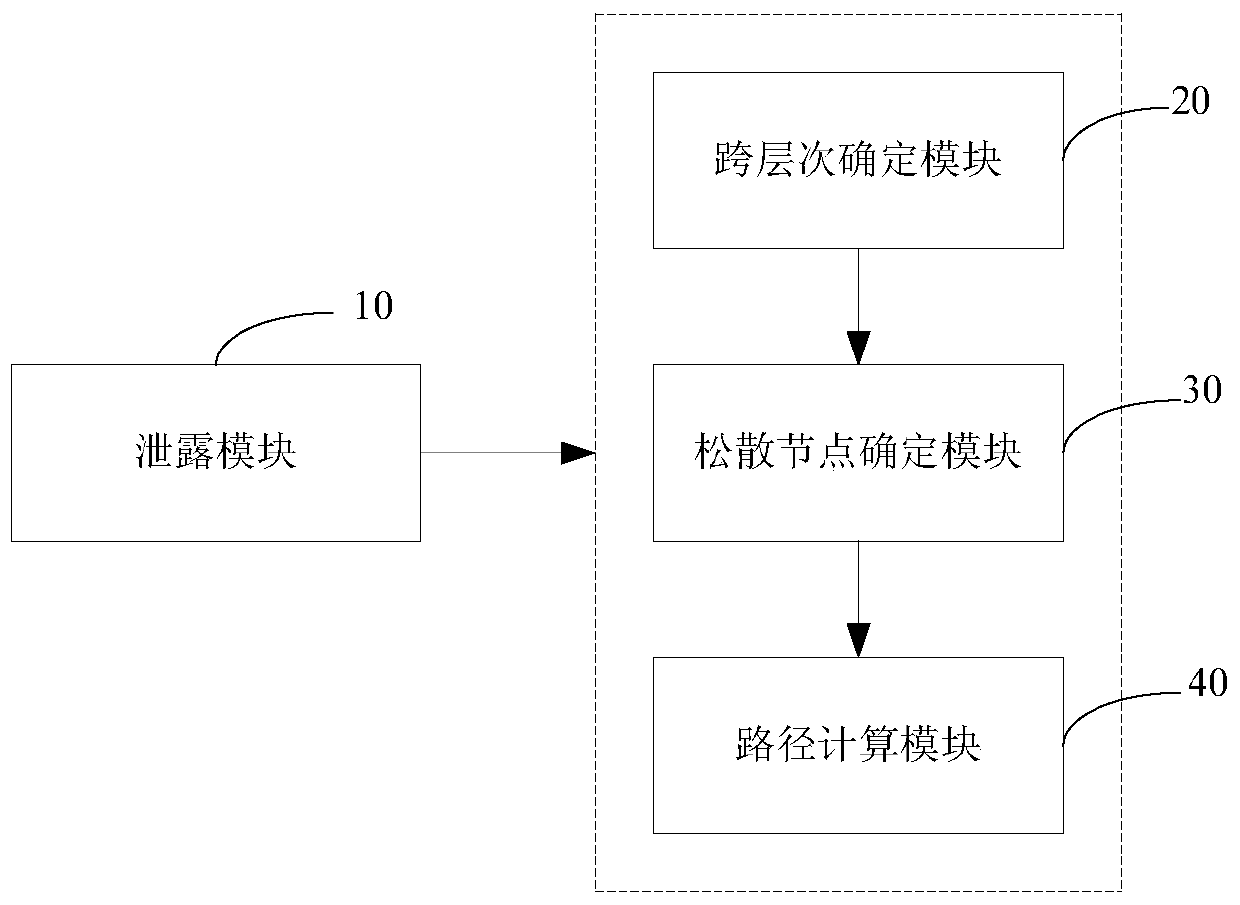
Image
Examples
Embodiment 1
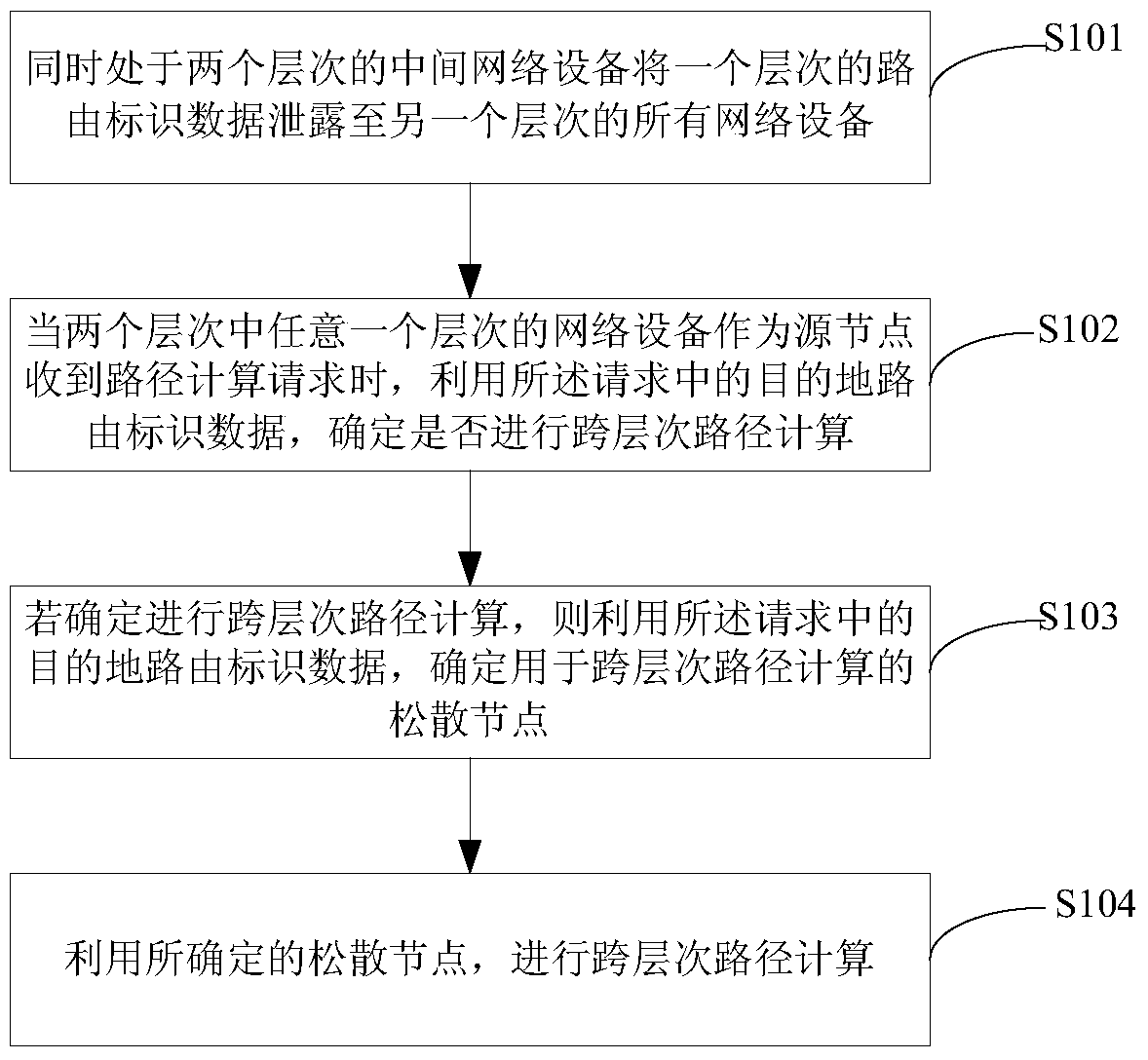
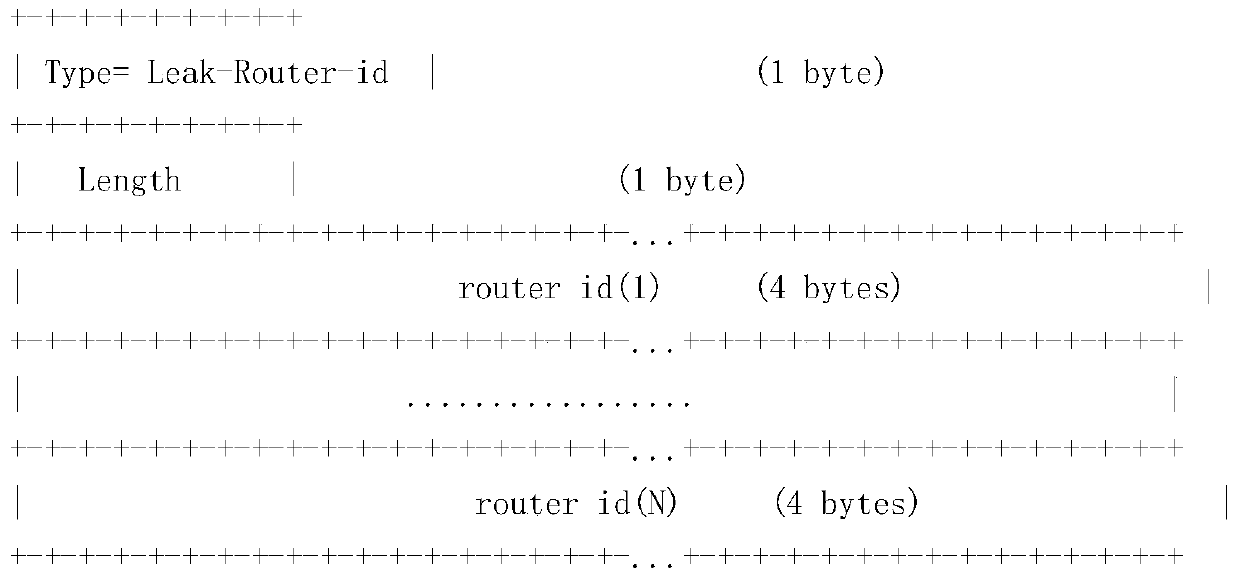
[0073] Such as Figure 4 As shown, in the network composed of R1, R2, R3, and R4, R1, R2, and R3 form an area, which is a Level 1 area, and establish a Level 1 neighbor relationship with each other. R2 and R4 establish a Level 2 backbone area, and establish a Level 1 area. 2 neighbors. Obviously, R2 is in the Level 1 area and also in the Level 2 backbone area. The TE router-ids of R1, R2, R3, and R4 intermediate systems are 1.1.1.1, 2.2.2.2, 3.3.3.3, and 4.4.4.4, respectively, which are unique identifiers in the TE network. Obviously, the level 1 function of R1, R2, and R3 ISIS is enabled, and the level 1 function of MPLS is enabled at the same time. R2, the level2 function of R4ISIS is enabled, and the level2 function of MPLS is enabled at the same time. R2 is a router of level 1 / Level 2, and the MPLS function of level 1 / Level 2 is enabled at the same time. Assume that a tunnel is currently configured to calculate the destination from router-id1.1.1.1 to 4.4.4.4, that is,...
Embodiment 2
[0079] Such as Figure 4 , a network composed of R1, R2, R3, and R4. R1, R2, and R3 form an area, which is a Level 1 area, and establish a Level 1 neighbor relationship with each other. R2 and R4 establish a Level 2 backbone area, and establish a Level 2 Neighborhood. Obviously, R2 is in the Level 1 area and also in the Level 2 backbone area. The TErouter-ids of R1, R2, R3, and R4 intermediate systems are 1.1.1.1, 2.2.2.2, 3.3.3.3, and 4.4.4.4, respectively, which are unique identifiers in the TE network. Obviously, the level 1 function of R1, R2, and R3 ISIS is enabled, and the level 1 function of MPLS is enabled at the same time. R2, the level2 function of R4ISIS is enabled, and the level2 function of MPLS is enabled at the same time. R2 is a level 1 / Level 2 router, and the MPLS function of level 1 / Level 2 is enabled at the same time. Assume that a tunnel is currently configured to calculate the destination from router-id 4.4.4.4 to 1.1.1.1, that is, the tunnel from R4 t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com