Intelligent equipment machine learning safety monitoring system based on user behavior
A smart device and security monitoring technology, applied in computer security devices, transmission systems, instruments, etc., can solve the problems of not building a secure cloud platform, threats to users' life and property, and lack of protection for smart devices, so as to improve monitoring efficiency and success rate, high user behavior pattern correlation, and the effect of preventing extreme malicious operations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
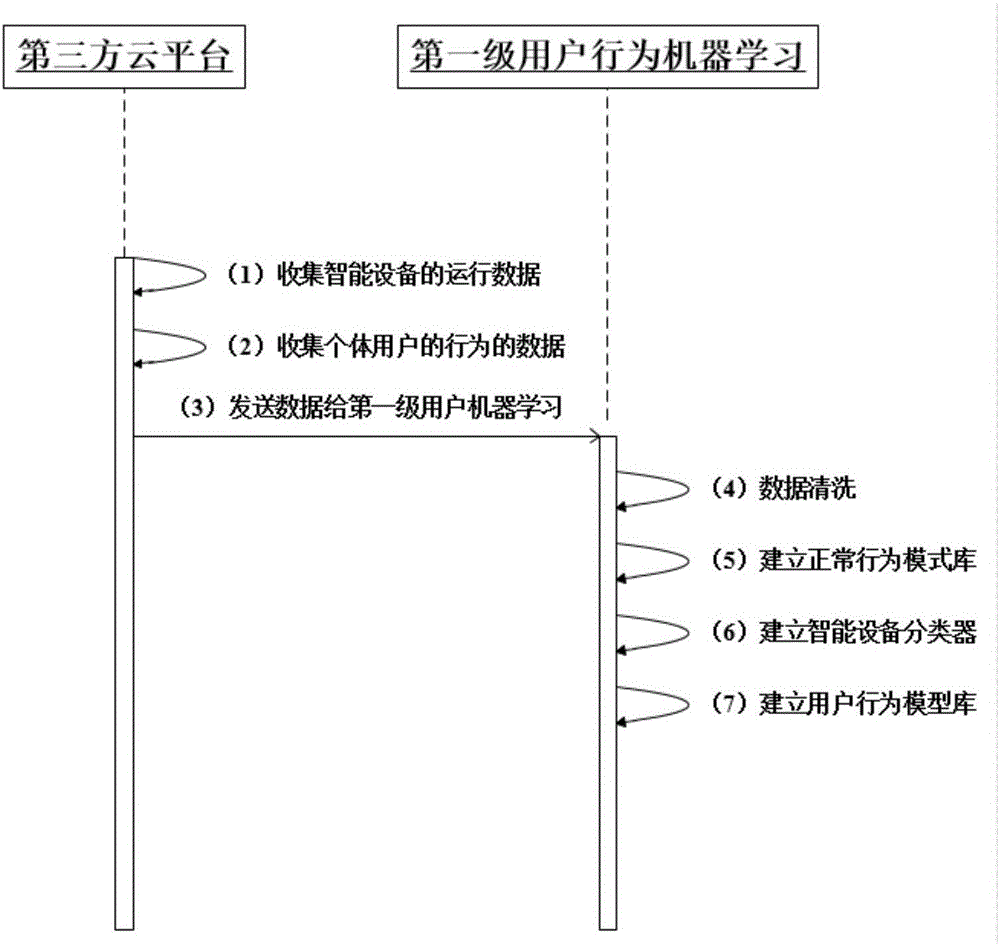
[0043] Based on user behavior data, the present invention proposes a two-layer model machine learning system, realizes the separation of cloud model and device-side model, and ensures that when the communication between the cloud or the cloud and the smart device is maliciously attacked, the smart device can pass through its own The machine learning module prevents the execution of malicious instructions.
[0044] In order to make the objectives, advantages and technical solutions of the present invention more clear, the present invention will be further described in detail below through specific implementation and in conjunction with the accompanying drawings.
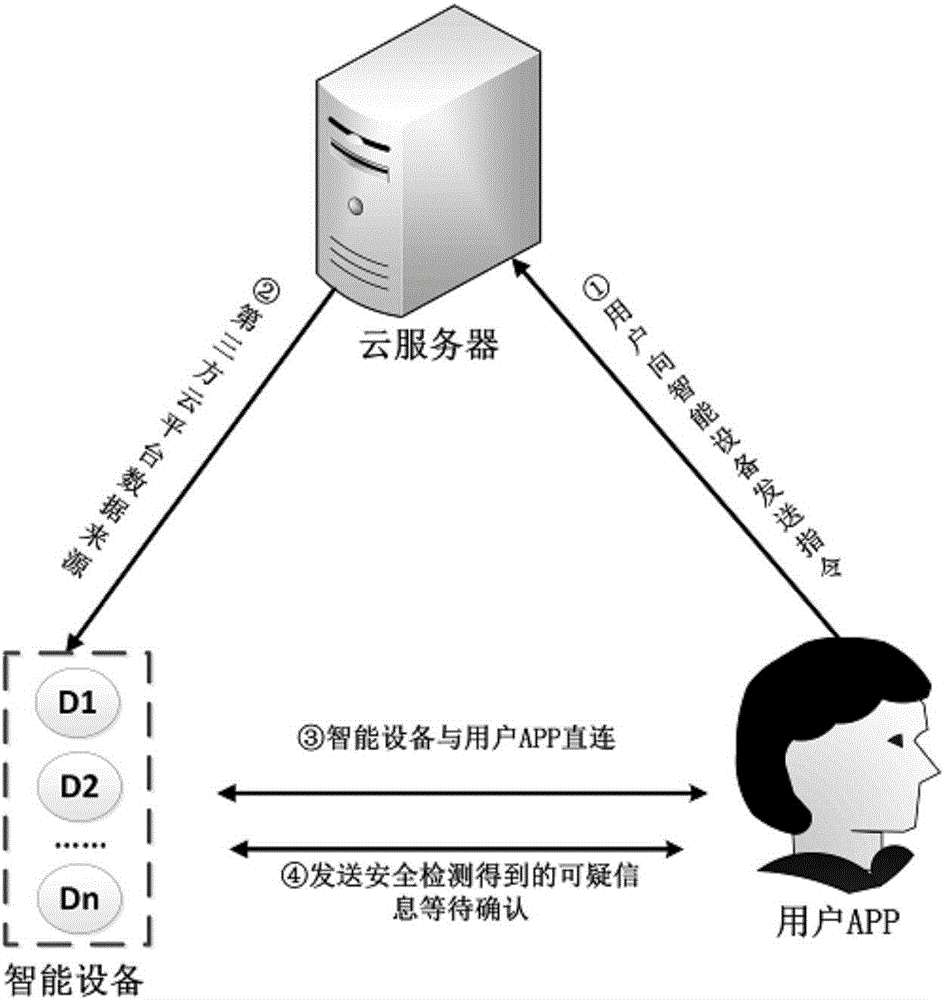
[0045] for figure 1 Describes the overall implementation framework of the program as a whole. In a nutshell, one is that when the user needs to use the mobile phone APP to send instructions to the cloud server (usually through Internet communication protocols such as WiFi), the cloud server will analyze them. The se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com