Internal threat detection system based on mining of business process model and detection method thereof
A model mining and business process technology, which is applied in transmission systems, unstructured text data retrieval, special data processing applications, etc., can solve problems such as rarely considering the security of business activities, business system exceptions, leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
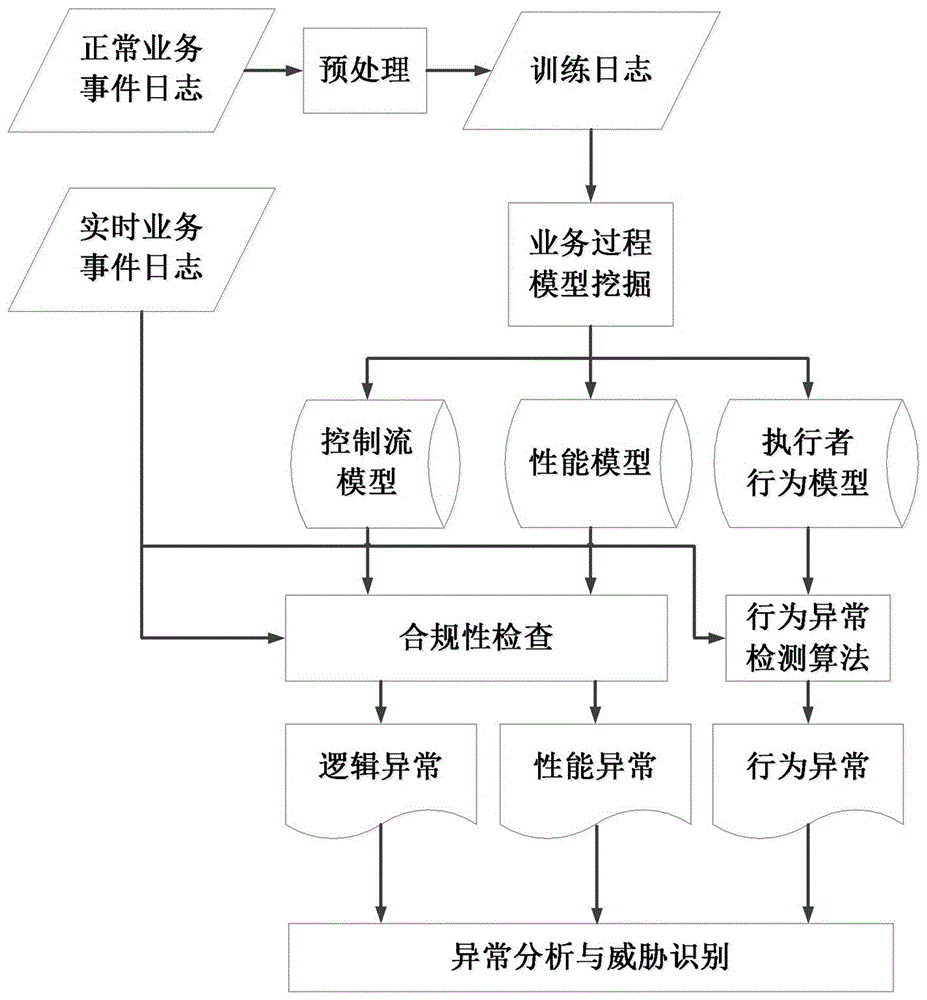
[0048] Embodiment one, see figure 1 As shown, an internal threat detection system based on business process model mining includes a model mining module, an anomaly detection module, and an anomaly analysis and threat identification module. Process model mining, in which the business process model includes the business control flow model, business performance model, and executor behavior model; the anomaly detection module detects logical anomalies in the event logs generated in real time during business operation based on the mined business process model , Abnormal business performance and abnormal behavior of executors; the abnormal analysis and threat identification module analyzes the detection results of the abnormal detection module, identifies and outputs internal threats suffered by the system.
[0049] Use the event log recorded under the normal operation of the business system as the data source to mine the business process model, and obtain the control flow model, p...
Embodiment 2
[0050] Embodiment two, see figure 1 As shown, it is basically the same as Embodiment 1, except that: the model mining module includes a training log acquisition unit, a business control flow model mining unit, a business performance model mining unit, and an executive behavior model mining unit,
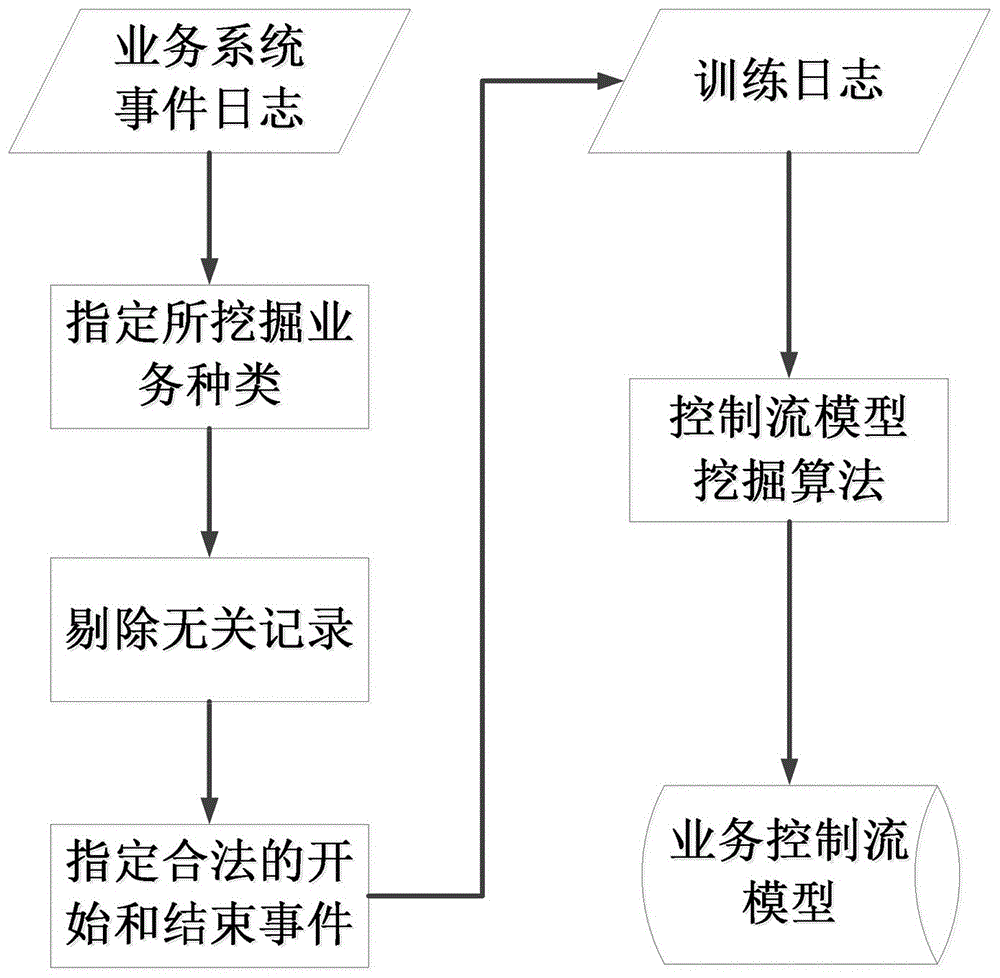
[0051] Among them, the training log acquisition unit filters the event logs of each business process in the business system according to the type of business to be mined, and filters the logs by specifying legal start and end events to obtain the training logs. The training log information includes the Multiple event sequences generated during business execution, the task name, timestamp, executor, and execution status corresponding to each event;
[0052] The business control flow model mining unit uses the training log to mine the business control flow model, and the business control flow model information includes the logical structure information between business events;
[005...
Embodiment 3
[0059] Embodiment three, see figure 2 As shown, a detection method of an internal threat detection system based on business process model mining includes the following steps:
[0060]Step 1. According to the event log of each business event in the business system, filter and screen according to the business type, propose records in the event log that are irrelevant to the mined business type, and specify the start event and end event of the business, obtain the training log, and mine through the process Methods The business control flow model mining is carried out on the training log, and according to the business control flow model and the training log, the business performance model mining and the executor behavior model mining are respectively carried out through statistical analysis methods, in which the business control flow model information includes the information between business events The logical structure information of the training log information includes multip...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com