Abnormal traffic suppression method and abnormal traffic suppression device
An abnormal traffic and abnormal technology, applied in the computer field, can solve problems such as inhibiting VoLTE, avoid deletion and improve accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
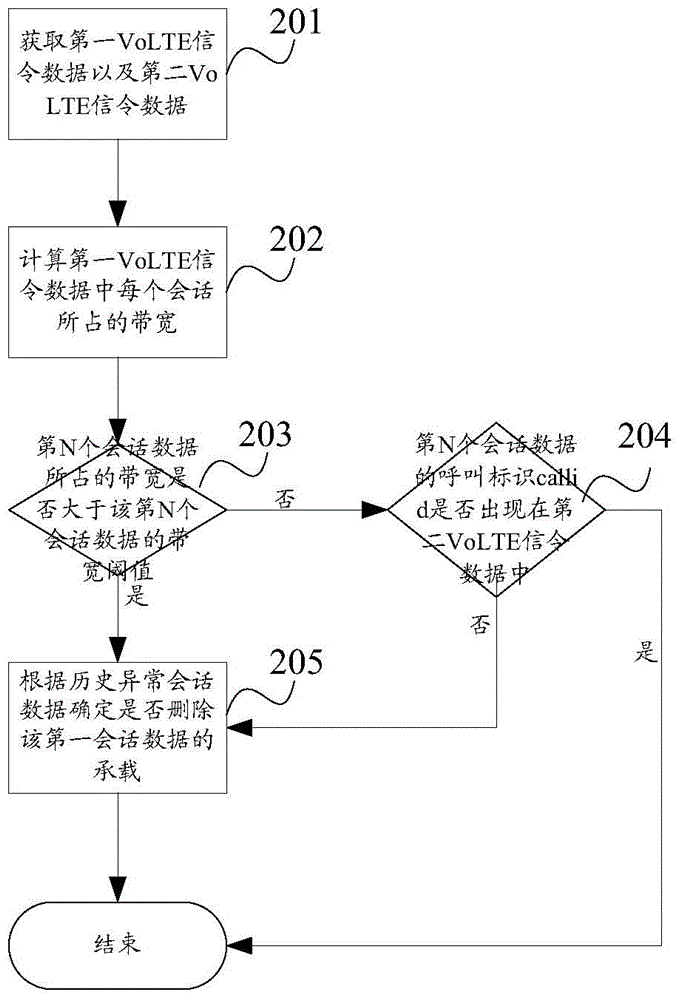
[0091] Such as figure 2 As shown, the first session data suppression flowchart provided by the embodiment of the present invention.
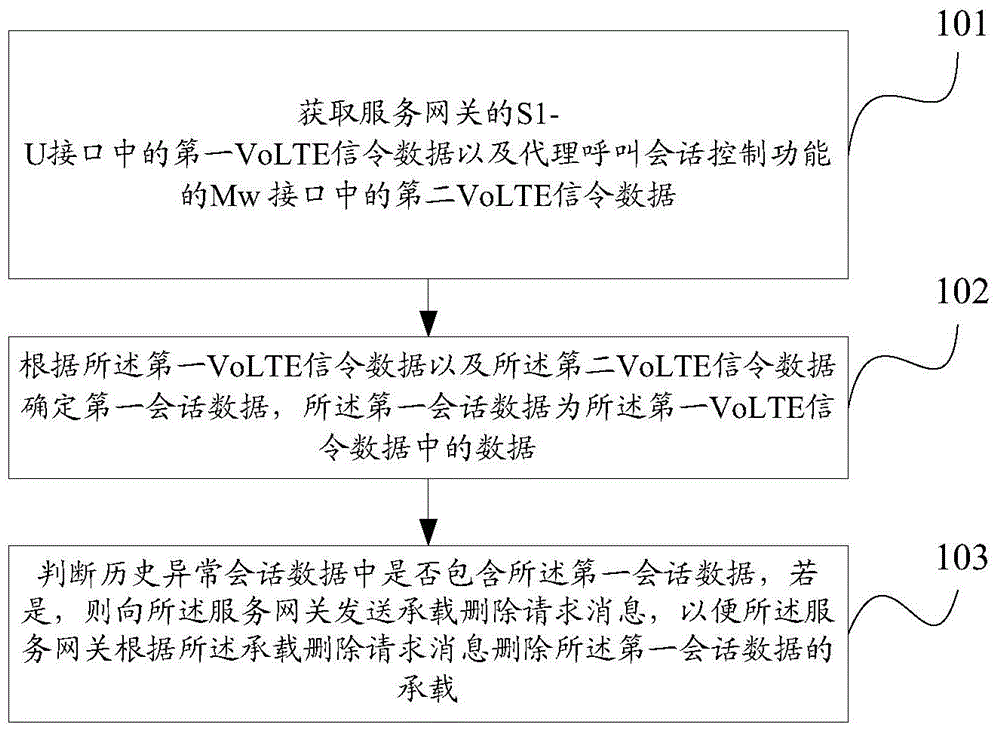
[0092] Step 201, respectively obtaining the first VoLTE signaling data in the S1-U interface of the serving gateway and the second VoLTE signaling data in the Mw interface of the proxy call session control function, and decoding the obtained VoLTE signaling data;
[0093] Step 202, calculating the bandwidth occupied by each session data in the first VoLTE signaling data;
[0094] Step 203, judge whether the bandwidth occupied by the Nth session data in the first VoLTE signaling data is greater than the bandwidth threshold of the Nth session data, if yes, then determine that the session data is the first session data, go to step 205; otherwise go to step 204;
[0095] Step 204, judging whether the call identifier callid of the Nth session data in the first VoLTE signaling data appears in the second VoLTE signaling data, if the call identifier ...
Embodiment 2
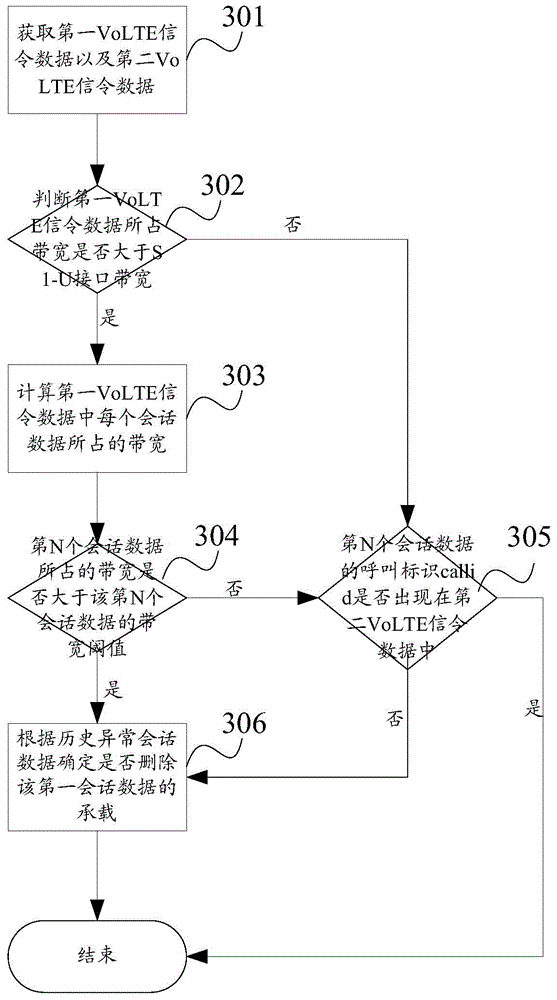
[0098] Further, after acquiring the first VoLTE signaling data and the second VoLTE signaling data, it is also possible to first determine whether the bandwidth occupied by the first VoLTE signaling data is greater than the bandwidth of the S1-U interface. If the bandwidth occupied by the first VoLTE signaling data If the bandwidth is greater than the S1-U interface bandwidth, then judge whether the bandwidth occupied by the Nth session data in the first VoLTE signaling data is greater than the preset threshold of the Nth session data bandwidth, if the first VoLTE signaling data occupies If the bandwidth is not greater than the bandwidth of the S1-U interface, it is directly judged whether the call identifier callid of the Nth session data in the first VoLTE signaling data appears in the second VoLTE signaling data. In this way, the recognition efficiency of the first session data can be improved. Specifically, see the following description for details.
[0099] Such as ima...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com