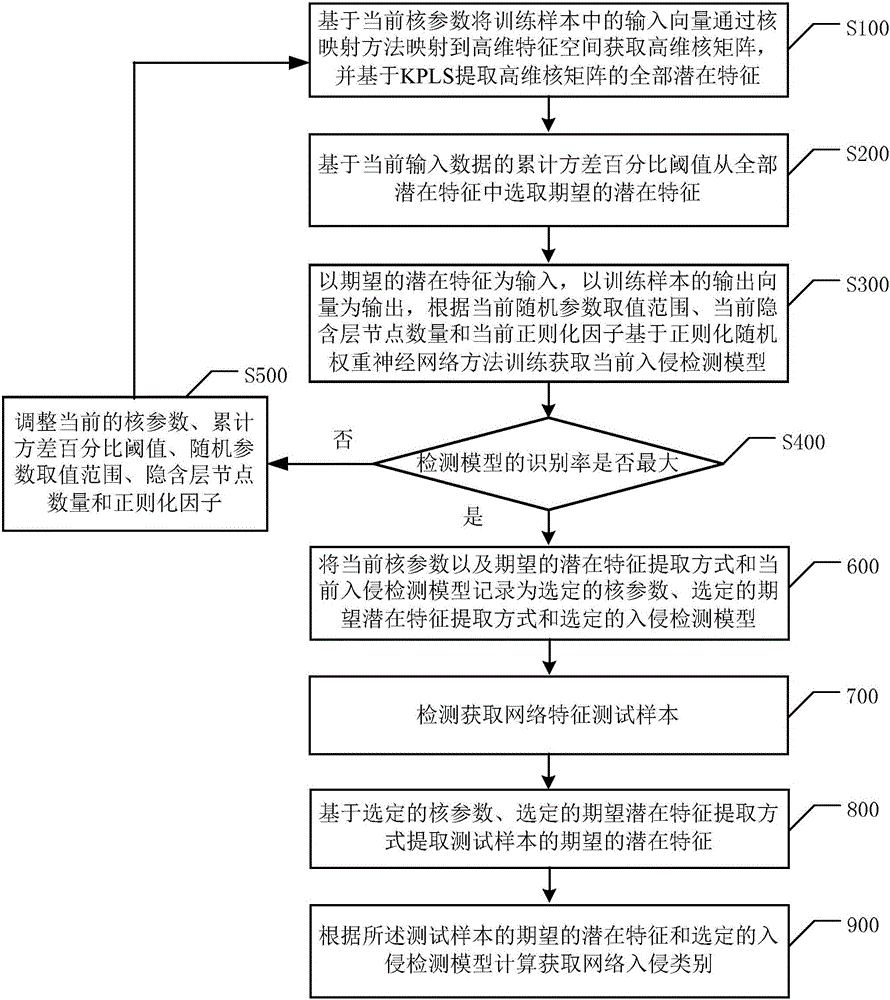
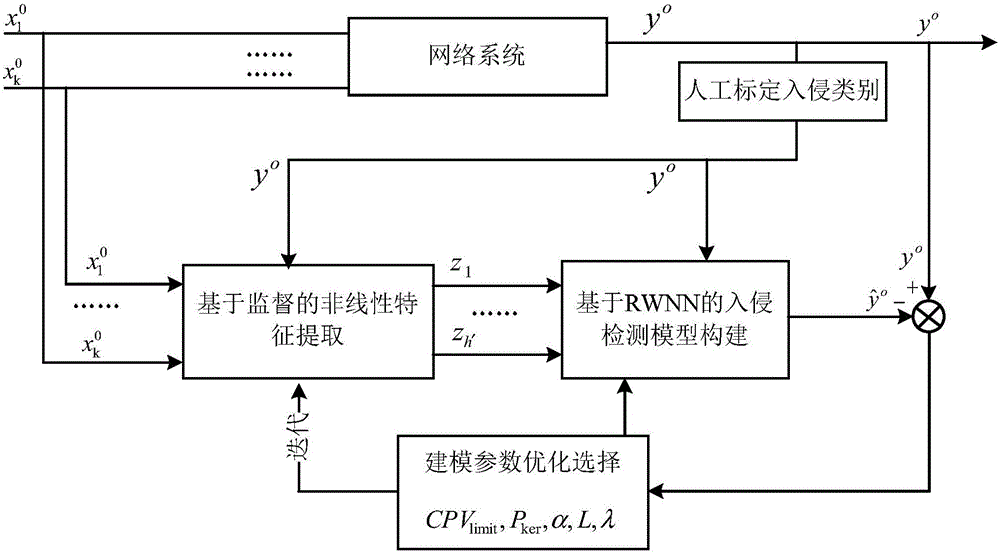
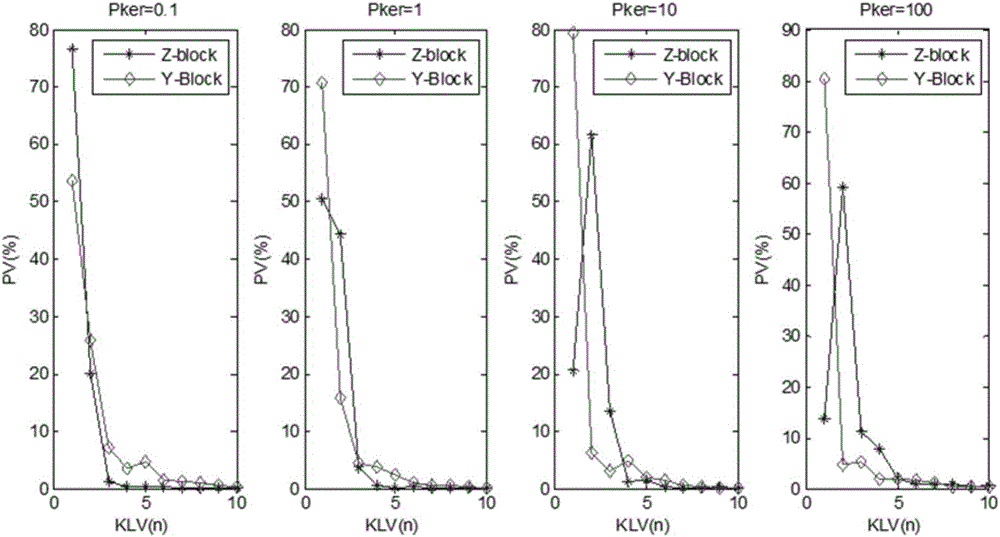
Network invasion abnormity detection method
A network intrusion and intrusion detection technology, applied in the field of network security, can solve problems such as the inability to guarantee universal approximation capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] The present invention is described below based on examples, but the present invention is not limited to these examples only. In the following detailed description of the invention, some specific details are described in detail. The present invention can be fully understood by those skilled in the art without the description of these detailed parts. Well-known methods, procedures, procedures, components and circuits have not been described in detail in order to avoid obscuring the essence of the present invention.
[0065] Furthermore, those of ordinary skill in the art will appreciate that the drawings provided herein are for illustrative purposes and are not necessarily drawn to scale.
[0066] Unless clearly required by the context, words such as "including", "comprising" and the like throughout the specification and claims should be construed in an inclusive rather than an exclusive or exhaustive sense; that is, "including but not limited to" meaning.
[0067] In ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com