Network penetration testing method
A test method and network penetration technology, applied in electrical components, transmission systems, etc., can solve the problems of difficulty in penetration testing, no attack graph, and security testers spending a lot of time, etc., to achieve automation, reduce complexity, The effect of reducing complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
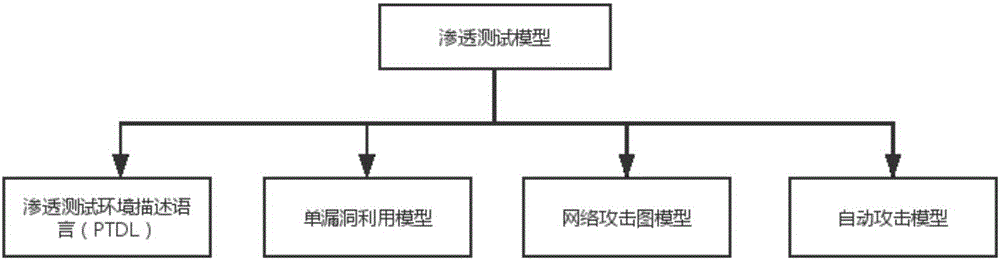
[0034] Example: such as figure 1 Shown is the penetration testing model, which includes four components: Penetration Testing Environment Description Language (PTDL), Single Vulnerability Exploitation Model (SVEM), Network Attack Graph Model, and Automatic Attack Model.
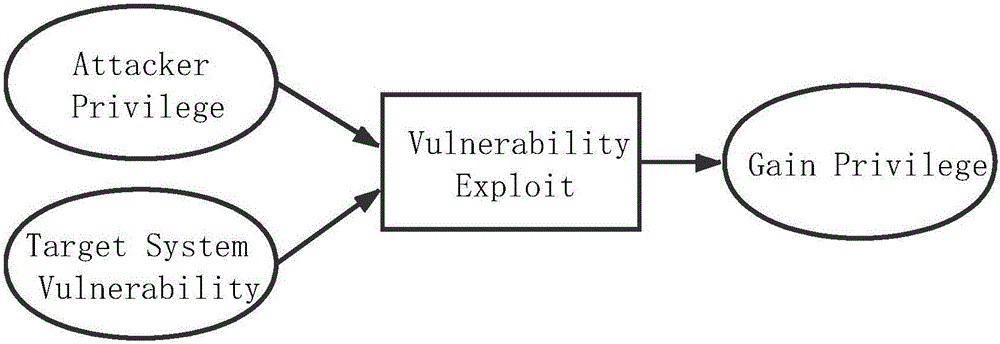
[0035] The penetration test environment description language uses XML to describe, including two sub-parts: network environment description and host vulnerability information description. The network description part is a series of descriptions for specific networks. Each specific network includes network ID, network segment and adjacency reachability. Network ID; host vulnerability information description includes a series of specific host information, including host ID, host IP, host network ID and a series of host vulnerability lists, each vulnerability includes vulnerability CVE number, vulnerability type, vulnerability attacker privilege And exploits to gain access.
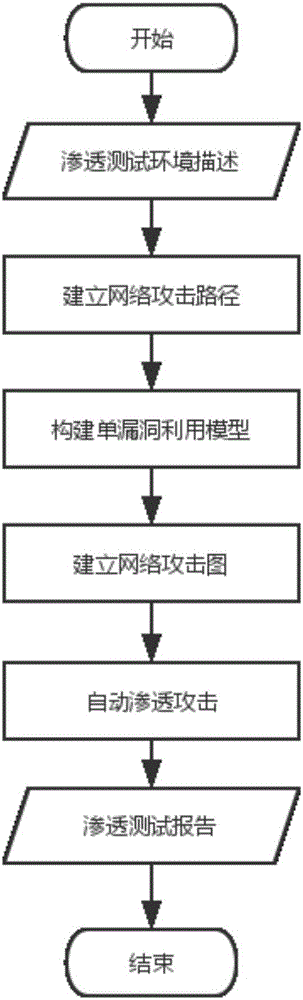
[0036] figure 2 Shown is the flowc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com