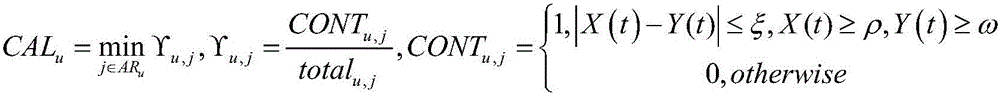Data tracking based recommendation system security detection method
A recommendation system and security detection technology, applied in the field of data processing, can solve problems such as low detection efficiency and system vulnerability, and achieve the effect of reducing error rate, avoiding invalidity or inefficiency, and overcoming low efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
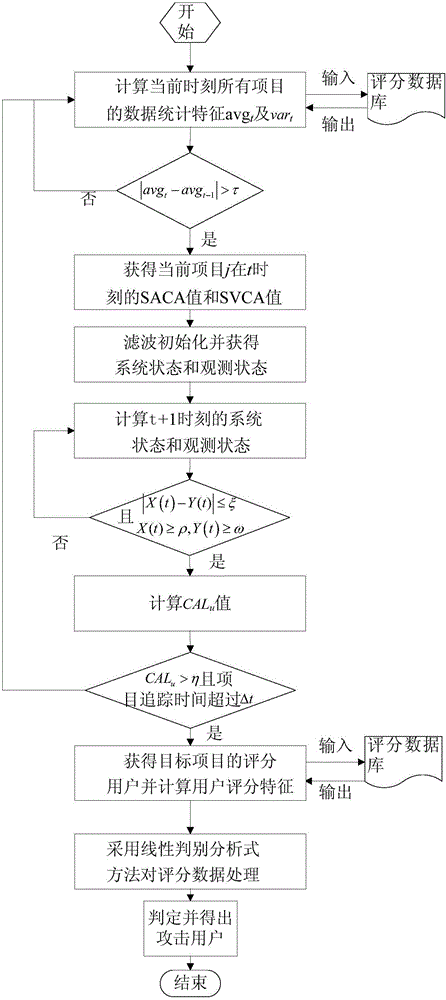
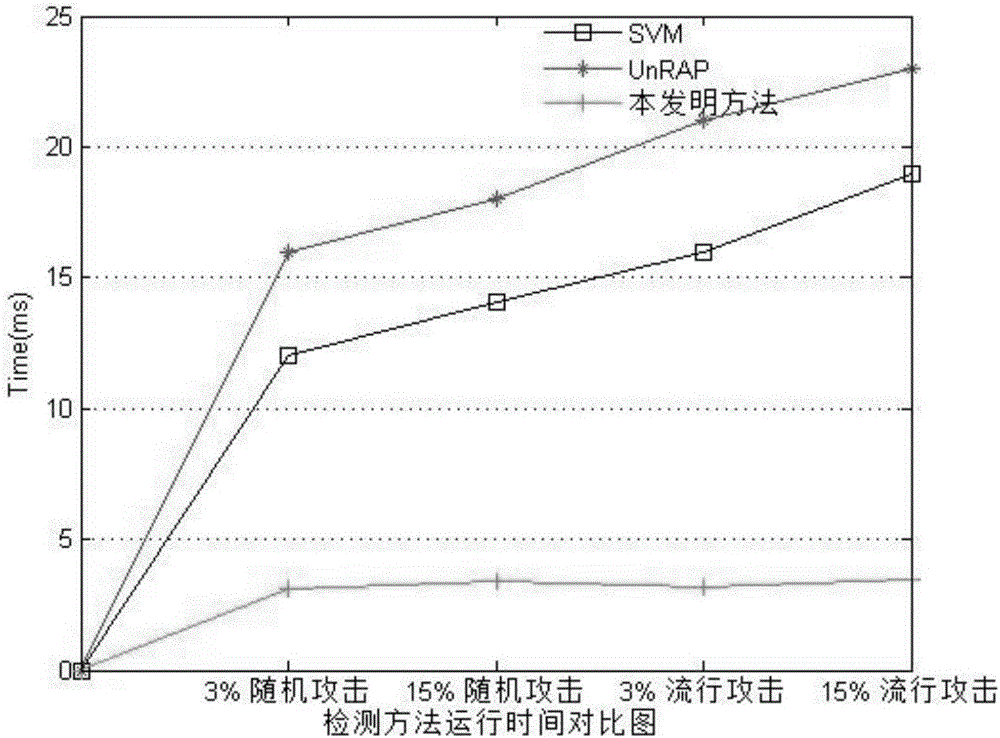
[0062] A specific embodiment is provided below to apply the detection method of the present invention to a real e-commerce scene. Here, the MovieLens dataset is used as the rating database of the recommendation system for experiments. The dataset is provided by the GroupLens research team of the University of Minnesota in the United States. It contains 100,000 rating records of 1,682 movies from 943 users, so it has rich attributes, The advantages of data authenticity are widely used in data mining and other fields. The comparative detection methods used in the present invention include SVM and UnRAP, both of which are relatively popular detection methods in current research and application. The present invention adopts the common random attack and popular attack in the recommendation system to attack the method of the present invention and the SVM and UnRAP methods. The attack scales (AttackSize) of these two types of attack methods are respectively 3% and 15%. Through the co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com