System and method for false response based on dynamic transformation and network security system and method
A dynamic transformation and false technology, applied in the field of network security, can solve the problems involving many modules, poor practicability and versatility, complex deployment, etc., and achieve the effect of widely promoting application value, maintaining security and stability, and defending against penetration attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
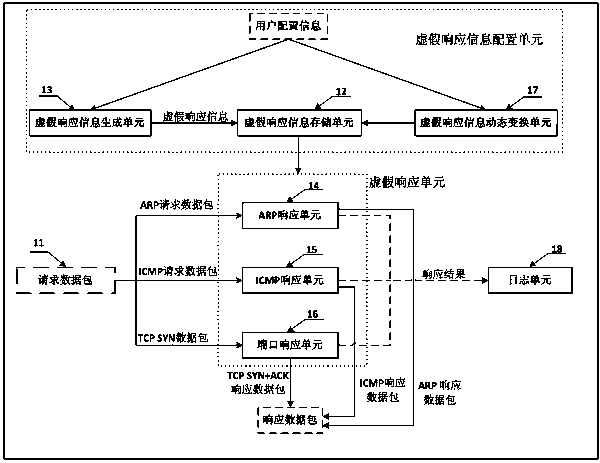
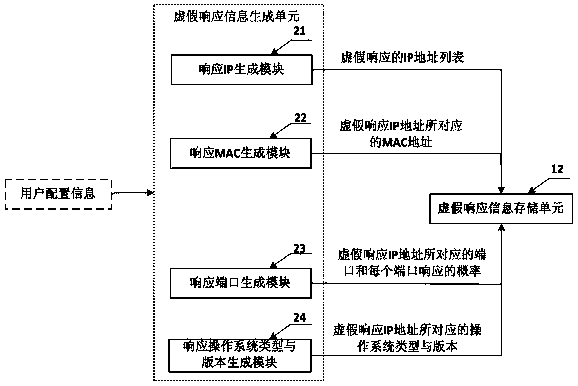
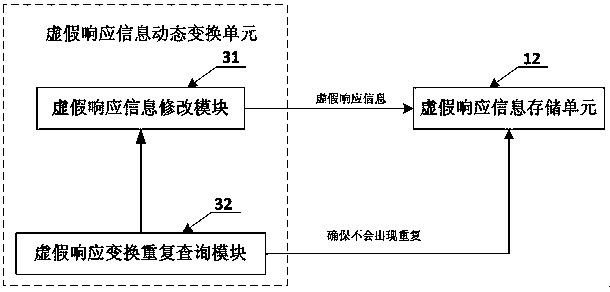
[0065] The difference between the false response system and the security system described in the second preferred embodiment of the present invention and the above-mentioned first preferred embodiment is only that the false response information generating unit 13 further includes a vulnerability information generating module 25, as attached Image 6 As shown, the user configuration information correspondingly includes a number of system vulnerability information that can be falsely responded to and the probability of each vulnerability information for a false response. The vulnerability information generation module 25 can perform false responses according to the user configuration information. A number of system vulnerability information and the probability of a false response to each vulnerability information, a number of vulnerability information corresponding to each IP address generated by the IP generation module 21 and the probability of a false response to each vulnerabil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com