Method for mining unknown network protocol hidden behaviors through clustering instruction sequences
A technology of instruction sequence and cluster mining, applied in the field of network security, can solve the problems of no protocol security and limited protocol information, achieve high analysis efficiency and accuracy, and improve the effect of speed and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
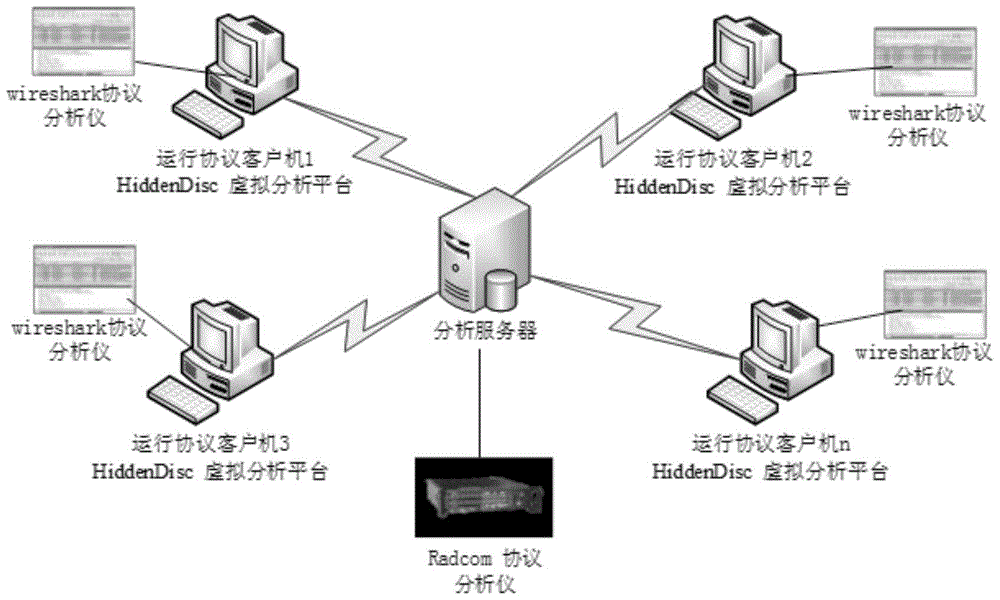
[0027] The present invention is suitable for figure 1 The network topology shown, the scene includes one analysis server and several clients running the protocol; each client is connected to the analysis server; the Wireshark tool is configured on each client to capture and analyze the protocol packets, and the analysis server is connected to Radcom hardware analysis The instrument performs secondary analysis on the protocol data packets; configures the self-developed HiddenDisk virtual analysis platform on the client computer, performs cluster analysis of the instruction sequence of the protocol program, mines the hidden behavior of the protocol, and evaluates the operating security of the protocol; each client computer will automatically The analysis result is transmitted to the analysis server, and after the analysis server performs correlation analysis, a protocol operation security assessment report is generated.
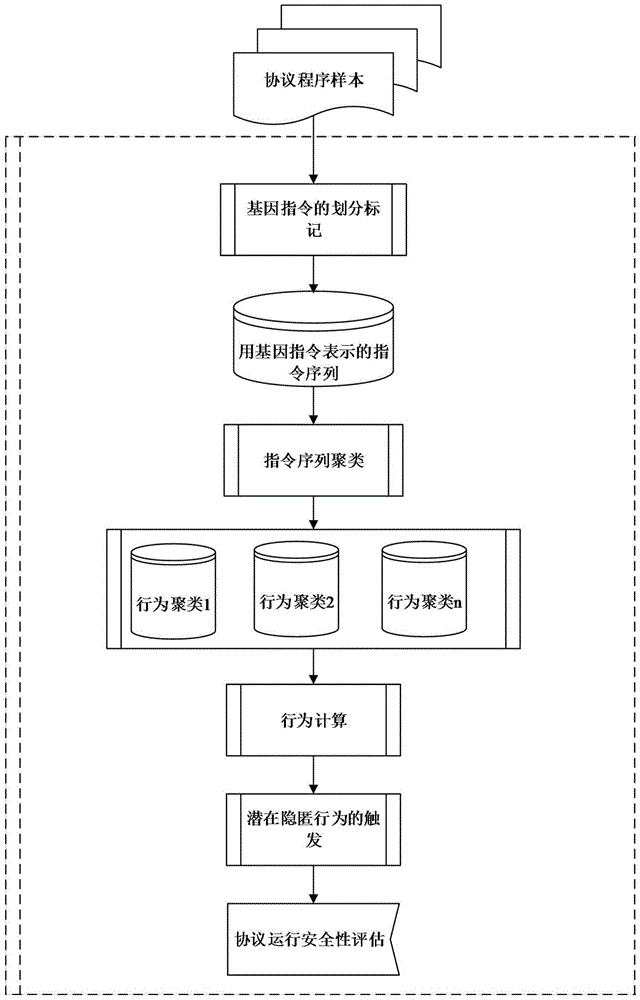
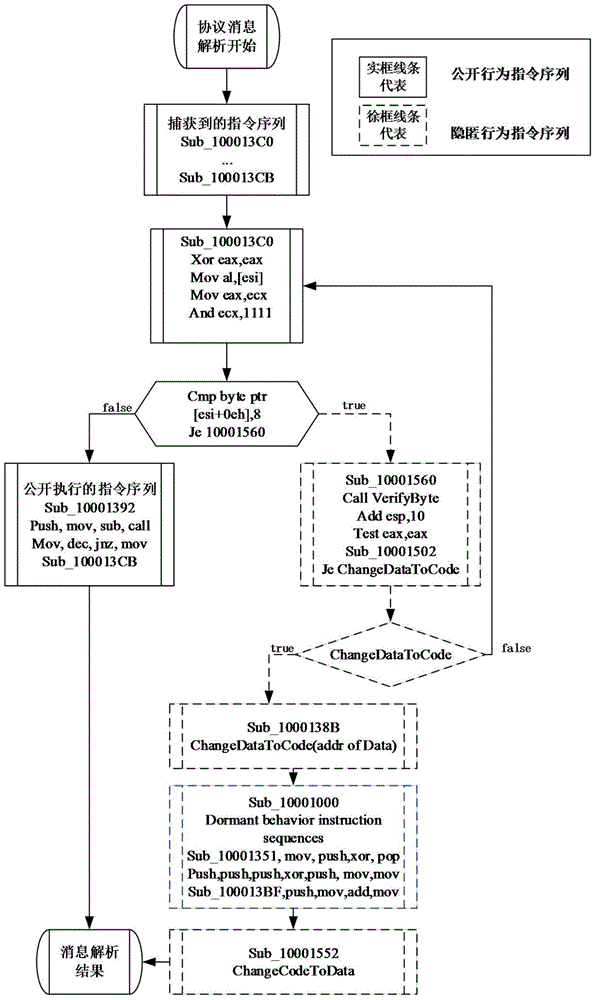
[0028] refer to figure 2 , the present invention utiliz...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com