Method and system for improving security rate of MIMO security communication system
A technology for secure rate and secure communication, applied in the field of improving the secure rate of a MIMO secure communication system, and can solve the problems of increasing hardware cost and system complexity, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
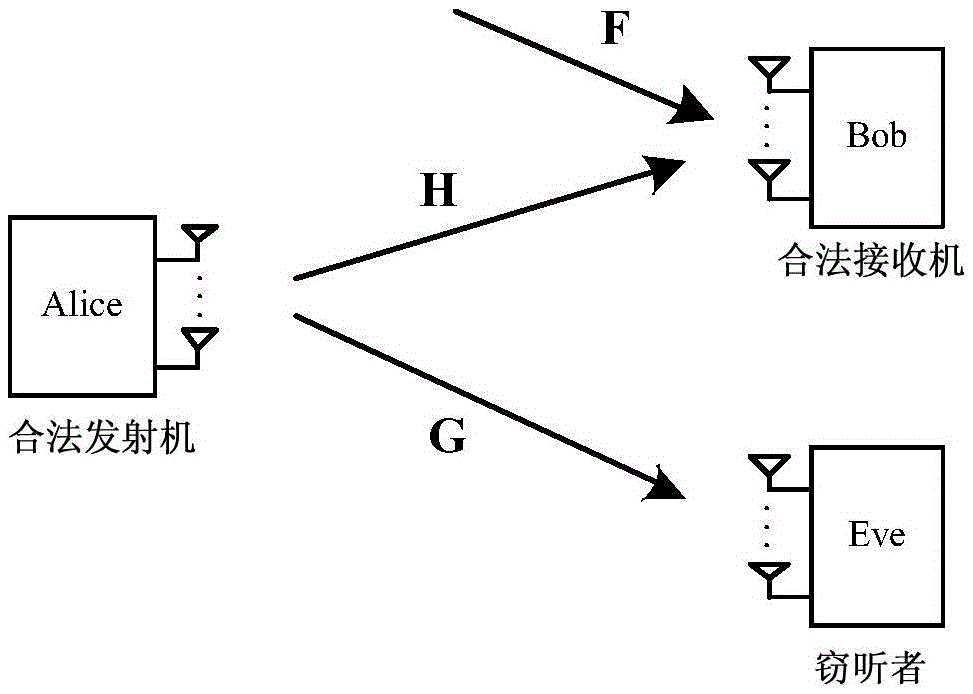
[0090] Such as figure 1 As shown, the secure communication system includes a transmitter, a legal receiver and an eavesdropper. The secure rate of a secure communication system is defined as the difference between the rate received by the legitimate receiver and the rate received by all eavesdroppers. For the sake of simplicity, the transmitter is called Alice, the legal receiver is Bob, and the eavesdropper is Eve. The antenna numbers of Alice, Bob and Eve are M, N respectively 1 and N 2 , where M≥N 2. Considering the narrowband transmission of the signal on a slow fading channel, the channel responses from Alice to Bob and Alice to Eve are: and
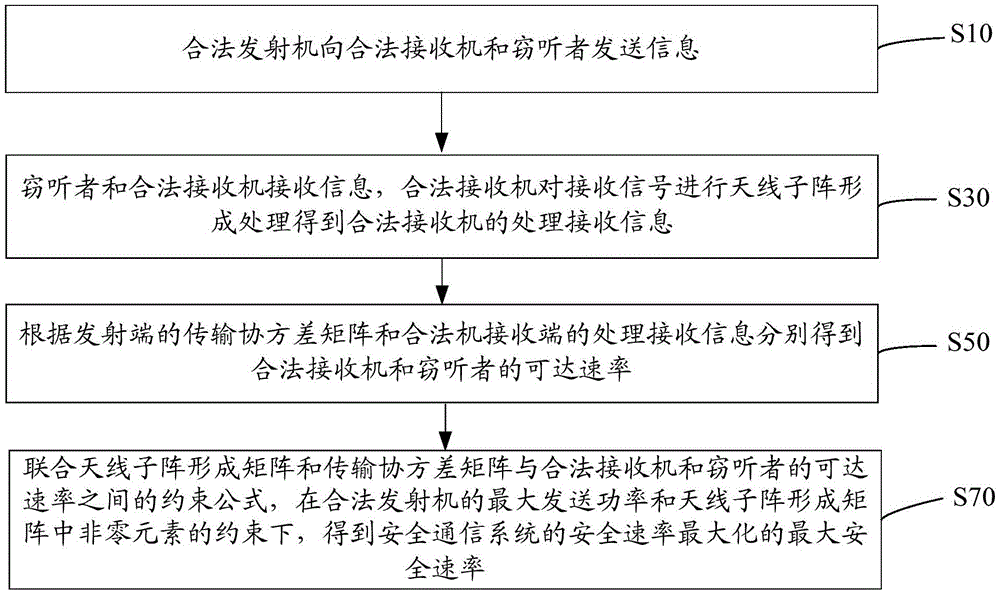
[0091] Such as figure 2 As shown, a method for improving the security rate of a MIMO security communication system includes:
[0092] S10: The legitimate transmitter sends information to the legitimate receiver and eavesdropper.
[0093] Among them, the signal sent by the legal transmitter is: Where M is the number of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com