Fuzzification device and method of sensitive data
A sensitive data, fuzzing technology, applied in the field of data processing, can solve problems such as leaking enterprises, achieve the effect of preventing leakage and retaining normal operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
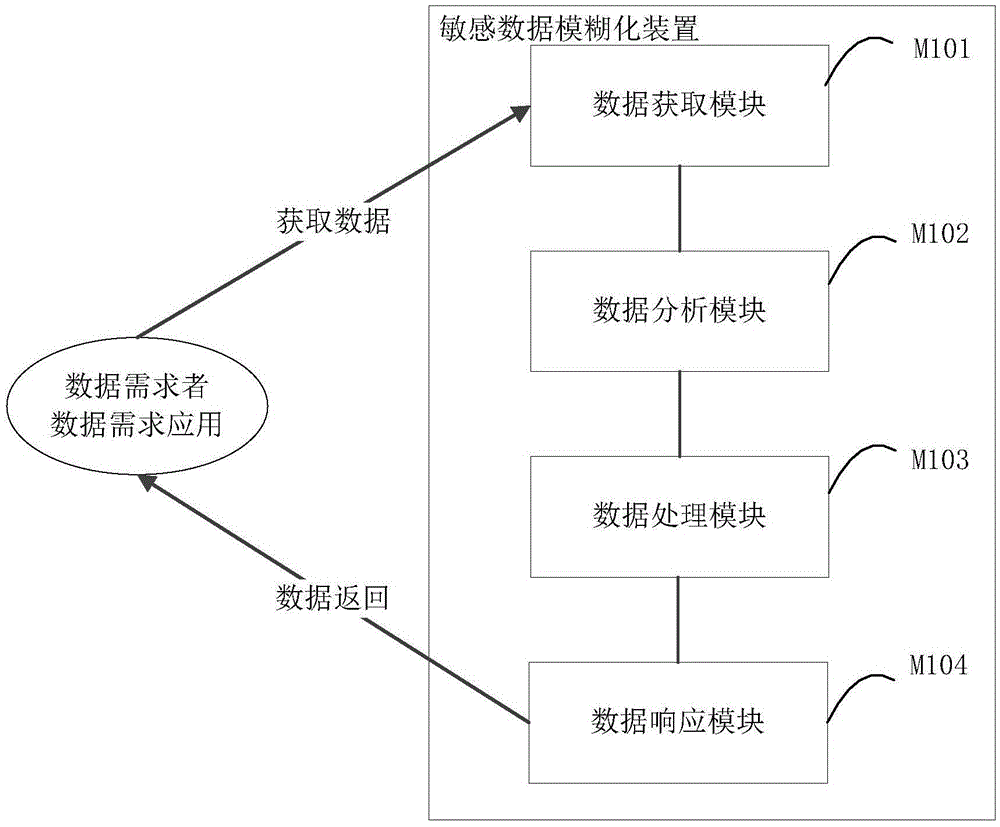
[0030] The embodiment of the present invention provides a sensitive data obfuscation device as an auxiliary accessory for the data demand application of the client that can access the server where the sensitive data resides, such as figure 2 The shown device includes a data acquisition module M101, a data analysis module M102, a data processing module M103 and a data response module M104.
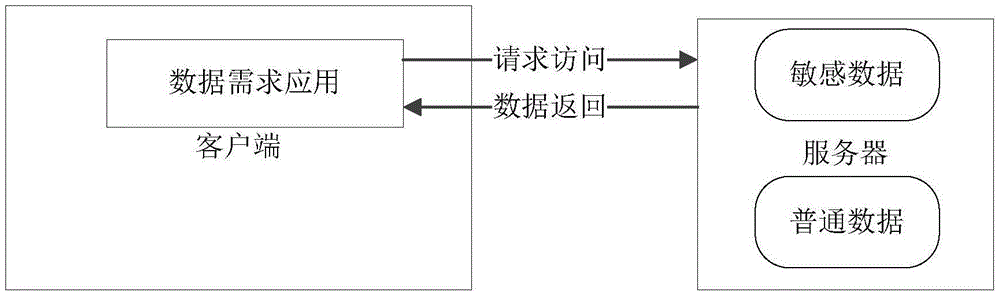
[0031] The data acquisition module M101 is used to obtain the return data requested from the server by the data demand application, and pass it to the data analysis module. The returned data requested from the server is directly used by the application program, which may cause sensitive data leakage, which may contain important information related to the company's business secrets. Therefore, the device obtains these data through data collection, capture, etc., and prepares for processing to eliminate data sensitivity, and transmits them to the data analysis module M102.
[0032] The data...
Embodiment 2
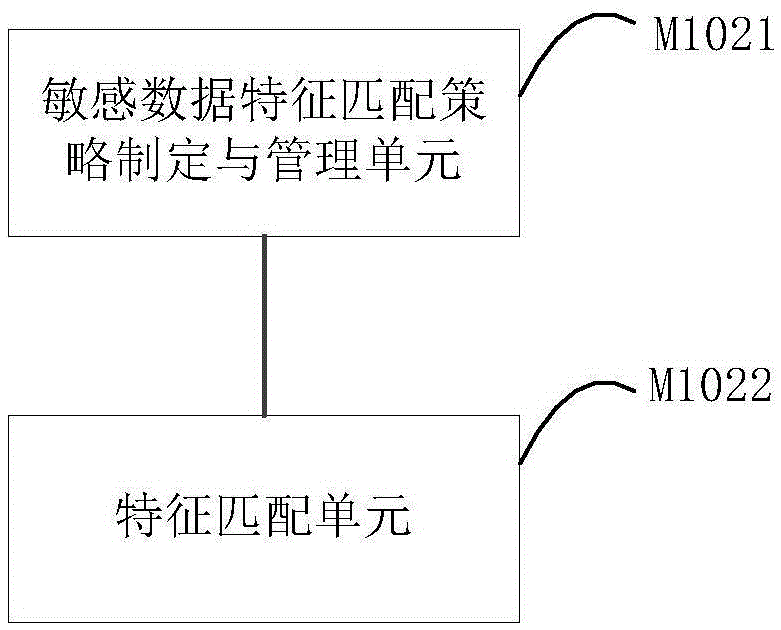
[0038] Such as image 3 As shown, the data analysis module M102 can further include a sensitive data feature matching strategy formulation and management unit M1021, which is used to formulate and manage sensitive data feature matching strategies; The data transmitted by the data acquisition module M101 is matched, and the sensitive data matching the characteristics are found, and then transmitted to the data processing module M103.
Embodiment 3
[0040] Such as Figure 4 As shown, the data processing module M103 may further include a sensitive data obfuscation strategy formulation and management unit M1031, which is used to formulate and manage a sensitive data obfuscation strategy suitable for the sensitive data feature matching strategy formulated by the data analysis module M102; The sensitive data obfuscation processing unit M1032 is used to perform fuzzy processing on the sensitive data transmitted from the data analysis module M102 according to the sensitive data obfuscation strategy, obtain fuzzy sensitive data, and transmit it to the data response module M104.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com