Byte substitution method applied to AES algorithm and system thereof
A byte replacement and algorithm technology, applied in digital transmission systems, transmission systems, encryption devices with shift registers/memory, etc., can solve problems such as potential safety hazards and slow software implementation speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
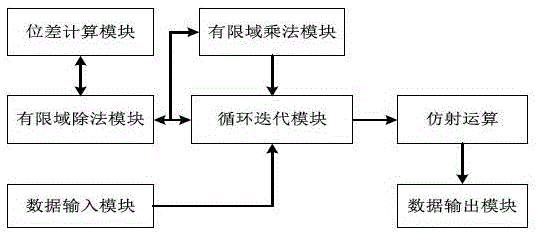
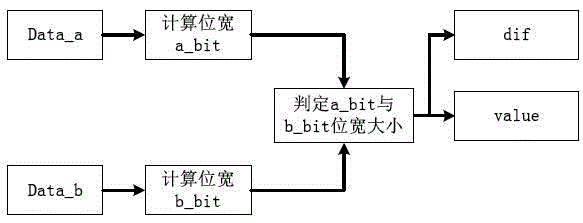
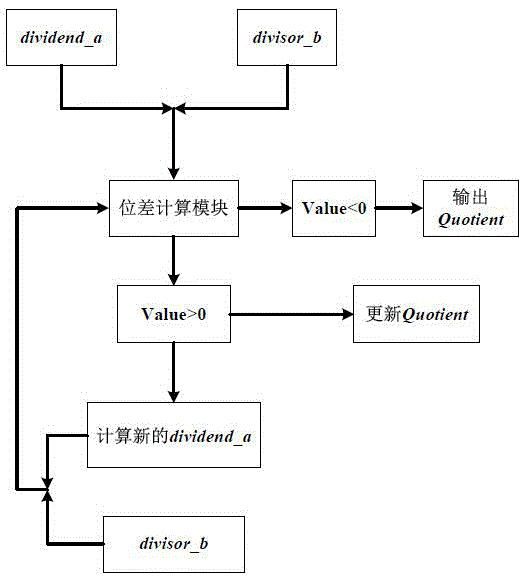
[0059] The AES algorithm adopts the Square (square) algorithm structure of the block cipher, and iteratively operates the round function. In the process of encryption and decryption, except for the last round, the same operation is performed in each round. The round function (round unit) of the encryption process includes four basic operations: byte substitution (SubBytes), row shift (ShiftRows), column mixing (MixColumns) and round key XOR (AddRoundkey); AES decryption process round function Including: inverse row shift (InvShiftRows), inverse byte substitution (InvSubBytes), round key XOR (AddRoundKey) and inverse column mix (InvMixColumns) four basic operations. Each operation of the round function in the decryption process is the reverse operation of the encryption process, but the order of operations is different from the encryption process. Wherein, the round key used for the XOR of the round key is obtained by key expansion. During the encryption process, the key expa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com