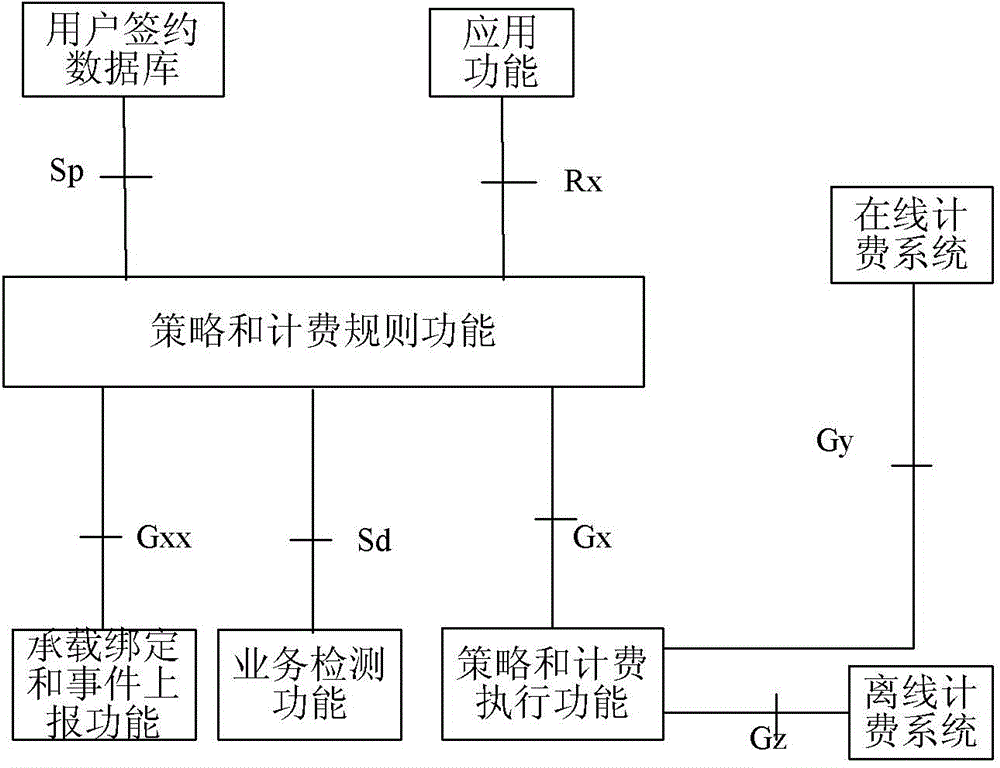
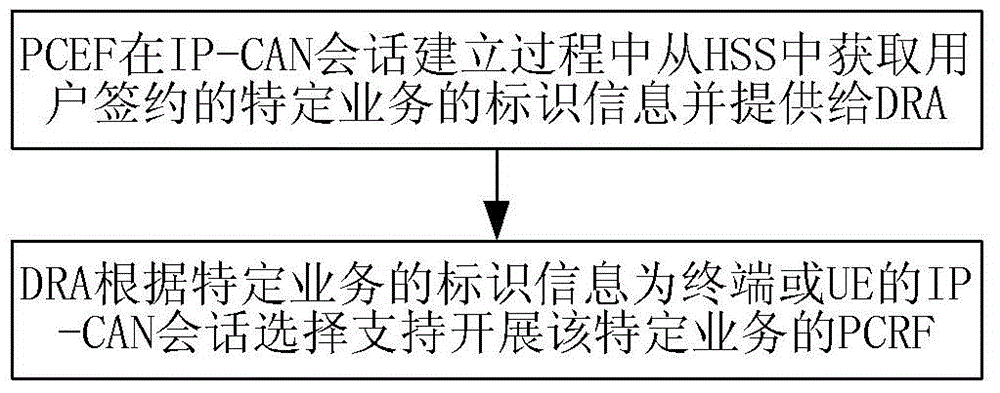
Method and apparatus for selecting policy and charging rules function
A technology of rules and policies, applied in the field of policy control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
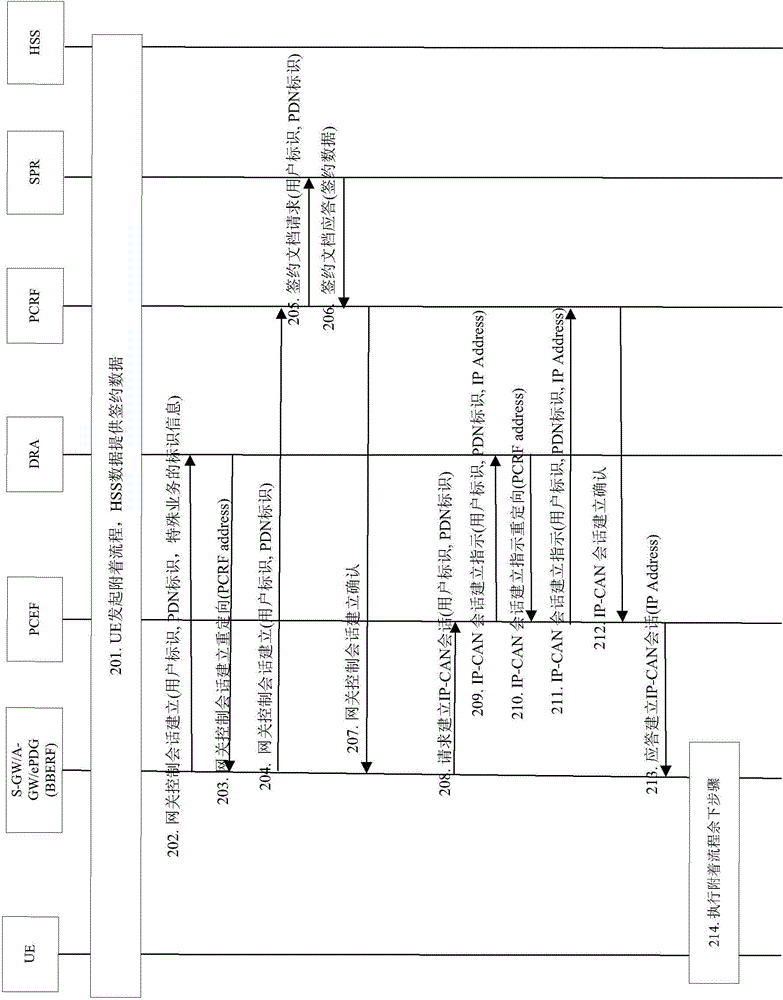
[0071] This embodiment describes that UE accesses from E-UTRAN (EvolvedUniversalTerrestrialRadioAccessNetwork, Evolved Unified Terrestrial Radio Access Network) and uses PMIPv6 protocol between S-GW (Serving Gateway) and P-GW (Packet Data Gateway), or from When a trusted non-3GPP network or an untrustworthy non-3GPP network accesses the 3GPP system and the PMIPv6 protocol is used between A-GW (Security Gateway) / ePDG (Evolved Packet Data Gateway) and P-GW, the process of establishing an IP-CAN session and PCRF selection process. DRA is RedirectAgent (redirect agent). image 3 It is a flowchart of Embodiment 1 of the selection method of PCRF of the present invention, such as image 3 As shown, it specifically includes the following steps:
[0072] Step 201: UE accesses through E-UTRAN or accesses from a trusted non-3GPP network and requests to establish an IP-CAN session. The UE initiates an attach request to the access network. During this process, for E-UTRAN access, the mo...
Embodiment 2
[0089] This embodiment describes when the UE accesses from E-UTRAN in a non-roaming scenario and the GTP (GPRS Tunnel Protocol, General Packet Radio Service Technology Tunneling Protocol) protocol is used between the S-GW and P-GW, or from a trusted When a 3GPP network or an untrusted non-3GPP network accesses the 3GPP system, when the GTP protocol is used between the A-GW / ePDG and the P-GW, the process of establishing an IP-CAN session and the selection process of PCRF. DRA is RedirectAgent. Figure 4 It is a flow chart of Embodiment 2 of the PCRF selection method of the present invention, which specifically includes the following steps:
[0090] Step 301: UE accesses through E-UTRAN or accesses from a trusted non-3GPP network and requests to establish an IP-CAN session. The UE initiates an attach request to the access network. During this process, for E-UTRAN access, the MME interacts with the HSS to obtain the subscription information of the UE, wherein the subscription in...
Embodiment 3
[0101] This embodiment describes that the user accesses from E-UTRAN and uses the PMIPv6 protocol between S-GW and P-GW, or accesses from a trusted non-3GPP network or accesses the 3GPP system from an untrusted non-3GPP network and A-GW When ePDG and P-GW adopt PMIPv6 protocol before, establish IP-CAN session process and PCRF selection process. DRA is (proxy server agent) ProxyAgent. Image 6 It is a flowchart of an embodiment of the PCRF selection method of the present invention, which specifically includes the following steps:
[0102] Step 401: UE accesses through E-UTRAN or accesses from a trusted non-3GPP network and requests to establish an IP-CAN session. The UE initiates an attach request to the access network. In this process, for E-UTRAN access, the MME interacts with the HSS to obtain the subscription information of the UE, wherein the subscription information carries the identification information of a specific service, and the MME sends it to the S-GW The sessio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com